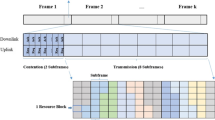
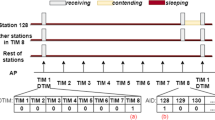
Abstract
This paper proposes an enhanced IEEE 802.11 CSMA/CA media access scheme designated as CSMA/CA-RBTv, in which RBT denotes the Registered Backoff Time and v denotes vector for Machine-to-Machine (M2M) communication. In the proposed CSMA/CA-RBTv, when a mobile node transmits data to the AP, it attaches a random number called the RBT, which denotes the next time slot the mobile node would like to transmit its next data packet, to the packet. Once the AP receives the packet, it extracts the RBT and adds it to a Registered-Time-Slot-List (RTSL) used to conduct channel access scheduling. Before transmitting the ACK packet to the mobile node, the AP (1) selects the node with the smallest RBT from the RTSL list as the next one to access the wireless channel and (2) uses RTSL to make a bit vector marking which time slots have been registered for data transmission, i.e., channel access. Then, the AP appends the aforementioned two pieces of channel access information to the ACK packet. Since the ACK packet is transmitted in a broadcast manner, all of the mobile nodes which overhear the transmission know which node has the next right to access the channel and which time slots are still available for channel access. Consequently, the occurrence of collisions can be reduced, which also results in decreasing power consuming. The simulation results show that CSMA/CA-RBTv has significant improvement in both transmission performance and energy efficiency of the M2M network as the number of mobile nodes increases.


















Similar content being viewed by others
References
Jain PC (2012) M2M wireless communication, annual seminar on C-DAC Noida technologies
Chen M, Wan J, Li F (2012) Machine-to-machine communications architectures standards and application. KSII Trans Internet Inf Syst 6(2):480–497
Wu G, Talwar S, Johnsson K, Himayat N, Johnson KD (2011) M2M: from mobile to embedded internet. IEEE Commun Mag 49(4):36–43
Dua A, Kumar N, Bawa S, Rodrigues JJPC (2015) An intelligent context-aware congestion resolution protocol for data dissemination in vehicular Ad Hoc networks. Mob Netw Appl 20(2):181–200
Lu RX, Li X, Liang XH, Shen XM, Lin XD (2011) GRS: the green, reliability, and security of emerging machine to machine communications. IEEE Commun Mag 49(4):28–35
Zhang X, Yang K, Wang P, Hong X (2015) Energy efficient bandwidth allocation in heterogeneous wireless networks. Mob Netw Appl 20(2):137–146
Bi S and Zhang YJ (2012) Mitigating power law delays: the use of polynomial back off in IEEE 802.11 DCF. Proceedings of IEEE International Conference on Communications (ICC), pp 5210–2515
Shurman M, Al-Shua’b B, Alsaedeen M, Al-Mistarihi MF and Darabkh KA (2014) N-BEB: new backoff algorithm for IEEE 802.11 MAC protocol, proceedings of the 37th international conference on information and communication technology, electronics and microelectronics (MIPRO), pp. 540–544
Balador A., Movaghar A. (2010) The novel contention window control scheme for IEEE 802.11 Mac Protocol, 2010 second international conference on networks security wireless communications and trusted computing (NSWCTC), 2:134–137
Hong KH, Lee SK, Kim KS, Kim YH (2012) Channel condition based contention window adaptation in IEEE 802.11 WLANs. IEEE Trans Commun 60(2):469–478
Yu Q, Zhuang YQ, Ma LX (2012) Dynamic contention window adjustment scheme for improving throughput and fairness in IEEE 802.11 wireless LANs, proceedings of 2012 I.E. global communications conference (GLOBECOM), pp. 5074–5080
Chun S, Dai XH, Liang PY, Han Z (2012) Adaptive access mechanism with optimal contention window based on node number estimation using multiple thresholds. IEEE Trans Wirel Commun 11(6):2046–2055
Ganchev A, Narayanan L (2011) Selfishness detection for backoff algorithms in wireless networks, 2011 I.E. 7th international conference on wireless and mobile computing, networking and communications (WiMob), pp. 517–524
Cheng MH, Hwang WS, Lin CH, Su HK (2013) A oneself adjusts backoff mechanism for channel access in IEEE 802.11 DCF WLAN, 2013 seventh international conference on complex, intelligent, and software intensive systems (CISIS), pp. 287–292
Syed I, Kim BS, Roh BH, Oh IH (2015) A novel contention window backoff algorithm for IEEE 802.11 wireless networks, 2015 IEEE/ACIS 14th international conference on computer and information science (ICIS), pp. 71–75
Munni TN, Mahbub N, Nirjhor KI, Uddin MF (2014) On the optimal contention window size in IEEE 802.11 based WLANs under co-channel interference, 2014 international conference on electrical and computer engineering (ICECE) pp. 394–397
Abeysekera BAHS, Matsuda T, Takine T (2008) Dynamic contention window control mechanism to achieve fairness between uplink and downlink flows in IEEE 802.11 wireless LANs. IEEE Trans Wirel Commun 7(9):3517–3525
Bharatiya M, Prasad S (2008) MILD based sliding contention window mechanism for QoS in wireless LANs, fourth international conference on wireless communication and sensor networks, pp. 105–110
Lin HH, Wei HY and Vannithamby R (2012) DeepSleep: IEEE 802.11 enhancement for energy-harvesting machine-to-machine communications, proceedings of 2012 I.E. global communications conference (GLOBECOM), pp. 5231–5236
Huang CM, Cheng RS, Tu TH (2015) CSMA/CA-RBT: a novel media access and power saving mechanisms for M2M communications, proceedings of the eleventh international conference on wireless and mobile communications (ICWMC)
Gilbert EN (1960) Capacity of a burst-noise channel. Bell Syst Tech J 39:1253–1266
Acknowledgments
The authors would like to thank the National Science Council, Taiwan, R.O.C. for financially supporting this research under Contract No. MOST 102-2221-E-006-114-MY3, MOST 103-2627-E-168-001, MOST 103-2622-E-168-018-CC3.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Cheng, RS., Huang, CM. & Tu, TH. A CSMA/CA-Based Media Access Protocol Using the Registered Backoff Time Vector (RBTv) Mechanism for M2M Communications. Mobile Netw Appl 22, 83–97 (2017). https://doi.org/10.1007/s11036-016-0680-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-016-0680-1