Abstract
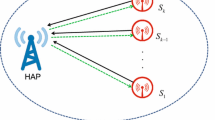
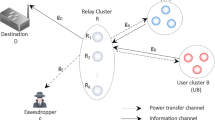
In this paper, we investigate radio frequency (RF) energy harvesting (EH) in wireless sensor networks (WSNs) using non-orthogonal multiple access (NOMA) uplink transmission with regard to a probable secrecy outage during the transmission between sensor nodes (SNs) and base station (BS) in the presence of eavesdroppers (EAVs). In particular, the communication protocol is divided into two phases: 1) first, the SNs harvest energy from multiple power transfer stations (PTSs), and then, 2) the cluster heads are elected to transmit information to the BS using the harvested energy. In the first phase, we derive a 2D RF energy model to harvest energy for the SNs. During the second phase, the communication faces multiple EAVs who attempt to capture the information of legitimate users; thus, we propose a strategy to select cluster heads and implement the NOMA technique in the transmission of the cluster heads to enhance the secrecy performance. For the performance evaluation, the exact closed-form expressions for the secrecy outage probability (SOP) at the cluster heads are derived. A nearly optimal EH time algorithm for the cluster head is also proposed. In addition, the impacts of system parameters, such as the EH time, the EH efficiency coefficient, the distance between the cluster heads and the BS, and the number of SNs as well as EAVs on the SOP, are investigated. Finally, Monte Carlo simulations are performed to show the accuracy of the theoretical analysis; it is also shown that the secrecy performance of NOMA in RF EH WSN can be improved using the optimal EH time.












Similar content being viewed by others
References
Wan J, Tang S, Shu Z, Li D, Wang S, Imran M, Vasilakos AV (2016) Software-defined industrial internet of things in the context of industry 4.0. IEEE Sens J 16(20):7373–7380
Wang S, Wan J, Li D, Zhang C (2015) Implementing smart factory of industrie 4.0: an outlook. Int J Distrib Sensor Netw 12(1):1–10
Wang S, Wan J, Zhang D, Li D, Zhang C (2016) Towards the smart factory for industrie 4.0: a self-organized multi-agent system assisted with big data based feedback and coordination elsevier computer networks. Comput Netw 101:158–168
Al-Turjman F, Radwan A (2017) Data delivery in wireless multimedia sensor networks: challenging and defying in the IoT era. IEEE Wireless Commun 24(5):126–131
Williams JM, Khanna R, Ruiz-Rosero JP, Pisharody G, Qian Y, Carlson CR, Liu H, Rmirez-Gonzalez G (2017) Weaving the wireless web: toward a low-power, dense wireless sensor network for the industrial IoT. IEEE Microwave Mag 18(7):40–63
Ye W, Ordonez F (2008) Robust optimization models for energy-limited wireless sensor networks under distance uncertainty. IEEE Trans. Wireless Commun 7(6):2161–2169
Trapasiya SD, Soni HB (2017) Energy efficient policy selection in wireless sensor network using cross layer approach. IET Wireless Sens Syst 7(6):191–197
Liu H-H, Su J-J, Chou CF (2017) On energy-efficient straight-line routing protocol for wireless sensor networks. IEEE Syst J 11(4):2374–2382
Nguyen TG, So-In C, Nguyen NG, Phoemphon S (2017) A novel energy-efficient clustering protocol with area coverage awareness for wireless sensor networks. Peer to Peer Networking and Applicat 10(3):519–536
Sheng Z, Mahapatra C, Zhu C, Leung VCM (2015) Recent advances in industrial wireless sensor networks toward efficient management in IoT. IEEE Access 3:622–637
Li F, Li Y, Zhao W, Chen Q, Tang W (2006) An adaptive coordinated MAC protocol based on dynamic power management for wireless sensor networks. In: Proc Int Conf on wireless Commun and mobile computing, pp 1073–1078
Li Y, Yu N, Zhang W, Zhao W, You X, Daneshmand M (2011) Enhancing the performance of LEACH protocol in wireless sensor networks. In: Proc IEEE Conf on Comput Commun workshops, pp 223–228
Cao B, Ge Y, Kim CW, Feng G, Tan H, Li Y (2013) An experimental study for inter-user interference mitigation in wireless body sensor networks. IEEE Sens J 13(10):3585–3595
Nguyen TG, So-In C, Nguyen NG (2017) Barrier coverage deployment algorithms for mobile sensor networks. J of Internet Technology 18(7):1–11
Li T, Dong Y, Fan P, Letaief KB (2017) Wireless communications with RF-based energy harvesting: from information theory to green systems. IEEE Access PP(99):1–13
Shaikh FK, Zeadally S (2016) Energy harvesting in wireless sensor networks: a comprehensive review. Renew Sustain Energy Rev 55:1041–1054
Van NTP, Hasan SF, Gui X, Mukhopadhyay S, Tran H (2017) Three-step two-way decode and forward relay with energy harvesting. IEEE Commun Lett 21(4):857–860
Habibu H, Zungeru AM, Susan AA, Gerald I (2014) Energy harvesting wireless sensor networks: design and modeling. Int J Wireless Mobile Netw 6(5):17–31
Alanazi A, Elleithy K (2015) Real-time QoS routing protocols in wireless multimedia sensor networks: study and analysis. Sensors 15(9):22209–22233
Teng Z, Kim K (2010) A survey on real-time MAC protocols in wireless sensor networks. Commun and Network 2(2):104–112
Rachamalla S, Kancharla A (2013) Survey of real-time routing protocols for wireless sensor networks. Int J of Comput Sci Eng Survey 4(3):35–44
Hua Y-K, Pang A-C, Hsiu P-C, Zhuang W, Liu P (2012) Distributed throughput optimization for zigbee cluster-tree networks. IEEE Trans Parallel Distrib Syst 23(23):513–520
Zhiqiang W, Jinhong Y, Ng DWK, Elkashlan M, Zhiguo D (2016) A survey of downlink non-orthogonal multiple access for 5G wireless communication networks. ZTE Commun 14(4):17–25
Dai L, Wang B, Yuan Y, Han S, I C-l, Wang Z (2015) Non-orthogonal multiple access for 5G: solutions, challenges, opportunities, and future research trends. IEEE Commun Mag 53(9):74–81
Men J, Ge J (2015) Performance analysis of non-orthogonal multiple access in downlink cooperative network. IET Commun 9(18):2267–2273
Diamantoulakis PD, Pappi KN, Karagiannidis GK, Xing H, Nallanathan A (2017) Joint downlink/uplink design for wireless powered networks with interference. IEEE Access 5:1534–1547
Higuchi K, Benjebbour A (2015) Non-orthogonal multiple access (NOMA) with successive interference cancellation for future radio access. IEICE Trans Commun E98-B(3):403–414
Ding Z, Peng M, Poor HV (2015) Cooperative non-orthogonal multiple access in 5G systems. IEEE Commun Lett 19(8):1462–1465
Liu Y, Ding Z, Elkashlan M, Poor HV (2016) Cooperative non-orthogonal multiple access with simultaneous wireless information and power transfer. IEEE J Sel Areas Commun 34(4):938–953
Chen Z, Ding Z, Dai X, Zhang R (2016) A mathematical proof of the superiority of NOMA compared to conventional OMA. IEEE Trans Signal Process 65(19):5191–5202
Zeng M, Yadav A, Dobre OA, Tsiropoulos GI, Poor HV (2017) On the sum rate of MIMO-NOMA and MIMO-OMA systems. IEEE Wireless Commun Lett 6(4):534–537
Saito Y, Kishiyama Y, Benjebbour A, Nakamura T, Li A, Higuchi K (2014) Non-orthogonal multiple access (NOMA) for cellular future radio access. In: Proc IEEE Veh Technology Conf, pp 1–5
Fan L, Yang N, Duong TQ, Elkashlan M, Karagiannidis GK (2016) Exploiting direct links for physical layer security in multiuser multirelay networks. IEEE Trans Wireless Commun 15(6):3856–3867
Xiaomei Y, Ke M (2016) Evolution of wireless sensor network security. In: Proc IEEE World Automat Congr, pp 1–5
Perrig A (2002) SPINS: security Protocols for sensor networks. ACM Wireless Networks 8(5):521–534
Chan H, Perrig A, Song D (2003) Random key predistribution schemes for sensor networks. In: Proc IEEE Symp Security and Privacy, May 2003, pp 197–213
Liu D, Ning P, Li R (2005) Establishing pairwise keys in distributed sensor networks. ACM Trans Info and System Security 8(1):41–77
Zhu J, Zou Y, Zheng B (2016) Physical-layer security and reliability challenges for industrial wireless sensor networks. IEEE Access 5:5313–5320
Ha D-B, Tran D-D, Truong T-V, Vo N-V (2016) Physical layer secrecy performance of energy harvesting networks with power transfer station selection. In: Proc IEEE Int Conf Commun Electron, pp 451–456
Qian M, Liu C, Zou Y (2016) Cooperative beamforming for physical layer security in power-constrained wireless sensor networks with partial relay selection. Int J Distrib Sens Netw 12(3):1–7
Hyadi A, Rezki Z, Alouini M (2016) An overview of physical layer security in wireless communication systems with csit uncertainty. IEEE Access 4:6121–6132
Choi J, Ha J, Jeon H (2013) Physical layer security for wireless sensor networks. In: Proc IEEE Int Symp on Personal Indoor and Mobile Radio Comm, pp 1–6
Zou Y, Wang G (2016) Intercept behavior analysis of industrial wireless sensor networks in the presence of eavesdropping attack. IEEE Trans Ind Informat 12(2):780–787
Jameel F, Wyne S, Krikidis I (2017) Secrecy outage for wireless sensor networks. IEEE Commun Lett 21(7):1565–1568
Tran H, Akerberg J, Bjorkman M, Tran H-V (2017) RF energy harvesting: an analysis of wireless sensor networks for reliable communication. https://doi.org/10.1007/s11276-017-1546-6
Vo VN, Nguyen TG, So-In C, Ha D-B (2017) Secrecy performance analysis of energy harvesting wireless sensor networks with a friendly jammer. IEEE Access 5:25196–25206
Diamantoulakis PD, Pappi KN, Ding Z, Karagiannidis GK (2016) Wireless-powered communications with non-orthogonal multiple access. IEEE Trans Wireless Commun 15(12):8422– 8436
Ha D-B, Nguyen SQ Outage performance of energy harvesting DF relaying NOMA networks. Mobile Networks and Applicat pp. 1–14, Oct. 2017. [Online]. Available: https://doi.org/10.1007/s11036-017-0922-x
Wang N, Song X, Cheng J, Leung VCM (2014) Enhancing the security of free-space optical communications with secret sharing and key agreement. J Opt Commun Netw 6(12):1072–1081
Wan Y, Li Q, Zhang Q, Qin J (2015) Optimal and suboptimal full-duplex secure beamforming designs for MISO two-way communications. IEEE Wireless Commun Lett 4(5):493–496
Shaikh FK, Zeadally S (2016) Energy harvesting in wireless sensor networks: a comprehensive review. Renew Sustain Energy Rev 55:1041–1054
Miridakis NI, Vergados DD (2013) A survey on the successive interference cancellation performance for single-antenna and multiple-antenna OFDM systems. IEEE Commun Surv Tutorials 15(1):313–335
Naderi MY, Chowdhury KR, Basagni S (2015) Wireless sensor networks with RF energy harvesting: energy models and analysis. In: Proc IEEE Wireless Commun and Networking Conf, pp 1494–1499
Tran H, Quach TX, Tran H, Uhlemann E (2017) Optimal energy harvesting time and transmit power in cognitive radio network under joint constraints of primary users and eavesdroppers. In: Proc Int Symp on Personal Indoor and Mobile Radio Commun
Kim J-B, Lee I-H (2015) Capacity analysis of cooperative relaying systems using non-orthogonal multiple access. IEEE Commun Lett 19(11):1949–1952
Lu F, Xu M, Cheng L, Wang J, Zhang J, Chang GK (2016) Non-orthogonal multiple access with successive interference cancellation in millimeter-wave radio-over-fiber systems. J Lightwave Technol 34(17):4178–4185
Ding Z, Adachi F, Poor HV (2016) The application of MIMO to non-orthogonal multiple access. IEEE Trans Wireless Commun 15(1):537–552
Gradshteyn I, Ryzhik I (2007). In: Jeffrey A, Zwillinger D (eds) Table of integrals, series, and Products. Academic Press , USA
Barros J, Rodrigues MRD (2006) Secrecy capacity of wireless channels. In: Proc IEEE Int Symp Inf Theory, pp 356–360
Vo VN, Nguyen TG, So-In C, Baig ZA, Sanguanpong S (2018) Secrecy outage performance analysis for energy harvesting sensor networks with a jammer using relay selection strategy. IEEE Access 6:23406–23419
Do NT, Costa DB, Duong TQ, Bao VNQ (2017) Exploiting direct links in multiuser multirelay SWIPT cooperative networks with opportunistic scheduling. IEEE Trans Wireless Commun 16(8):5410–5427
Toan HV, Bao VNQ, Le HN (2017) Cognitive two-way relay systems with multiple primary receivers: exact and asymptotic outage formulation. IET Commun 11(16):2490–2497
Acknowledgements
This work was supported by grants from Khon Kaen University via ASEAN and the GMS Countries’ Personnel programs 2017-2020 and an interdisciplinary grant (CSKKU2560) from the Department of Computer Science, Khon Kaen University.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix A: Proof of Lemma 1
Now, we prove Lemma 1 by considering the following integral:
Using some simplified transformations, we can rewrite Eq. 78 as follows:
where \({{\Gamma }_{1}}\left (z \right )\), \({{\Gamma }_{2}}\left (z \right )\), and \({{\Gamma }_{3}}\left (z \right )\) are defined as follows:
Using (3.352.4) and (3.353.2) in [58] to solve these integrals, \({\Gamma } \left (z \right )\) is obtained as in Eq. 50. The proof is completed.
Appendix B: Proof of Lemma 2
Similar to the approach of Lemma 1, we have
where \({{\Omega }_{1}}\left (z \right )\) and \({{\Omega }_{2}}\left (z \right )\) are defined as
Using (3.352.4) and (3.353.2) in [58] to calculate these integrals, the function \({\Omega } \left (z \right )\) can be obtained as in Eq. 54. The proof is completed.
Rights and permissions
About this article
Cite this article
Vo, V.N., Nguyen, T.G., So-In, C. et al. Outage Performance Analysis of Energy Harvesting Wireless Sensor Networks for NOMA Transmissions. Mobile Netw Appl 25, 23–41 (2020). https://doi.org/10.1007/s11036-018-1188-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-018-1188-7