Abstract
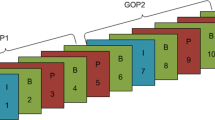
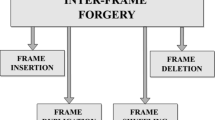
Among different types of video manipulations, video inter-frame forgery is a powerful and common tampering operation. Several forensic and anti-forensic techniques have been proposed to deal with this challenge. In this paper, we first improve an existing video frame deletion detection algorithm. The improvement is attributed to the combination of two properties resulted from video frame deletion, the periodicity and the magnitude of the fingerprint in the P-frame prediction error. We then analyze a typical anti-forensic method of video frame deletion, and prove that the fingerprint of frame deletion still can be discovered after being anti-forensically modified. We thus further propose a counter anti-forensics approach by estimating the true prediction error and comparing it with the prediction error stored in videos. We show that the detection algorithm is not only useful in detecting video frame deletion, but also useful for detecting video frame insertion. Compared with the existing counter anti-forensics, our proposed approach is robust when different motion estimation algorithms are used in the initial compression. Furthermore, the forensics and counter anti-forensics are combined to perform a two-phase test to detect video inter-frame forgery. A Video Inter-frame Forgery (VIF) game, which is zero-sum, simultaneous-move, is defined to analyze the interplay between the forger and the investigator. Mixed strategy Nash equilibrium is introduced to solve the VIF game and we can obtain the optimal strategies for both players. Experimental results show that the proposed forensic and counter anti-forensic methods not only outperform existing methods in detecting frame deletion and anti-forensics, but also outperform them in the VIF game.







Similar content being viewed by others
References
Barni M (2012) A Game theoretic approach to source identification with known statics. Proc. of ICASSP 1745-1748
Bestagini P, et al (2012) Video codec identification. Proc. of ICASSP 2257-2260
Chao J, Jiang XH, Sun TF(2012) A novel video inter-frame model deletion scheme based on optical flow consistency. Proc. of IWDW 267-281
Gironi A, Fontani M, Bianchi T, Piva A, Barni M (2014) A video forensic technique for detecting frame deletion and insertion. Proc. of ICASSP 6226-6230
Grant M, Boyd S (2008) Graph implementations for non-smooth convex programs. recent Advances in learning and control, lecture notes in control and information sciences, Springer 95–110
Hespanha J (2011) An introductory course in non-cooperative game theory. Published online, available at http://www.ece.ucsb.edu/"hespanha/
ISO (2008) Information technology - generic coding of moving pictures and associated audio information - part 2: Video. International Organization for Standardization. ISO/IEC IS 13818–2
ISO (2009) Information technology - coding of audio-visual objects-part 2: Visual. International Organization for Standardization, ISO/IEC IS 14496–2. Geneva
ISO (2010) Information technology - coding of audio-visual objects-part 10: Advanced video coding (avc). International Organization for Standardization, ISO/IEC IS 14496–10
Jiang X, Wang W, Sun T, Shi YQ, Wang S (2013) Detection of double compression in MPEG-4 videos based on Markov statistics. IEEE Signal Process Lett 20(5):447–450
Liu L, Cohen R, Sun H, Vetro A, Zhuang S (2010) New techniques for next generation video coding. Proc. of BMSB: p 1-6
Liu H, Li S, Bian S (2013) Detecting frame deletion in H.264 video. Proc. of ISPEC 262-270
Luo W, Wu M, Huang J (2008) MPEG recompression detection based on block artifacts. Proc. of SPIE 68190X 1-12
Milani S, Bestagini P, Tagliasacchi M, Tubaro S (2012) Mul-tiple compression detection for video sequences. Proc. of MMSP 112–117
Milani S et al (2012) An overview on video forensics. In APSIPA trans. Signal Inf Process 1:1–18
Osborne MJ, Rubinstein A (1994) A course in game theory. MIT Press
Pan Z, Zhang Y, Kwong S (2015) Efficient motion and disparity estimation optimization for low complexity multiview video coding. IEEE Trans Broad., 61(2):166--176.
Rocha A, Scheirer W, Boult T et al (2011) Vision of the unseen: current trends and challenges in digital image and video forensics. ACM Comput Surv 43(5):1–42
Stamm MC, Lin WS, Liu KJR (2012) Temporal forensics and anti-forensics for motion compensated video. IEEE Trans Inf Forensics Sec 7(4):1315–1329
Stamm MC, Lin WS, Liu KJR (2012) Forensics vs. anti-forensics: a decision and game theoretic framework. Proc. of ICASSP 1749-1752
Stamm MC, Liu KJR (2011) Anti-forensics for frame deletion/addition in MPEG video. Proc. of ICASSP 1876-1879
Vazquez-Padin D, Fontani M, Bianchi T, Comesana P, Piva A, Barni M(2012) Detection of video double encoding with GOP size estimation. in Proc. of WIFS 151–156
Wang W, Farid H (2006) Exposing digital forgeries in video by detecting double MPEG compression. Proc. of ACM Multimedia Secur Workshop 37–47
Wu Y, Jiang X, Sun T, Wang W (2014) Exposing video inter-frame forgery based on velocity field consistency. Proc. of ICASSP 2674-2678
Xu J, Su Y, Liu Q (2013) Detection of double MPEG-2 compression based on distributions of DCT coefficients. Int J Pattern Recognit Artif Intell 27(1):1354001
Zeng H, Kang X (2013) Camera source identification game with incomplete information. in Proc. of international workshop of digital-dorensics and watermarking. Aucland, New zealand, 2013
Zeng H, Kang X, Huang J (2013) Mixed-strategy Nash equilibrium in the camera source identification game. Proc. of IEEE Int. Conf. Image Process 4472–4476
Acknowledgments
This work was supported by the NSFC (Grant nos. 61379155, U1405254 and 61232016), the 973 Program (Grant no. 2011CB302204), the Research Fund for the Doctoral Program of Higher Education of China (Grant no. 20110171110042) and the NSF of Guangdong province (Grant no. S2013020012788).
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
The complete list of the video sequences investigated in our experiments is listed here: Akiyo, Bowing, Bridge-Close, Bridge-Far, Carphone, Claire, Coastguard, Contianer, Deadline, Football, Foreman, Galleon, Grandma, Hall, Highway (The longest sequence is divided into six portions), Husky, Mobile, Mother-Daughter, News, Pamphlet, Paris, Salesman, Sign-Irene, Silent, Stefan, Table, Tempete.
These video sequences can be downloaded from [http://trace.eas.asu.edu/yuv/, http://media.xiph.org/video/derf/].
Rights and permissions
About this article
Cite this article
Kang, X., Liu, J., Liu, H. et al. Forensics and counter anti-forensics of video inter-frame forgery. Multimed Tools Appl 75, 13833–13853 (2016). https://doi.org/10.1007/s11042-015-2762-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-2762-7