Abstract
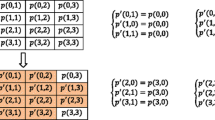
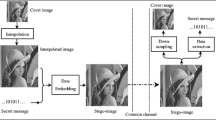
In 2012, Lee et al. proposed an interpolation technique with neighboring pixels (INP) as the base to conceal secret information in predicted pixels. Their method can effectively predict the pixel between two neighboring pixels. However, the different lengths of secret messages caused great distortion when a large secret message was concealed in the predicted value. Therefore, the proposed scheme applies the center folding strategy to fold the secret message for reducing image distortion. Furthermore, the proposed scheme references the variance of the neighboring pixel to determine the length of the secret message for controlling image quality. The parameter pair (k, F 1) is used to categorize the variance and determine the size of the secret message hidden in each category. k is the total number of thresholds which computed based on the characteristics of each image for balancing hiding payload and image quality. F 1 is the length of the secret message for the smoothest area. The experimental results show that the embedding capacity of the proposed method is 1.5 bpp higher than that of existing methods. For the same hiding payload, the image quality of the proposed method is 1.6 dB higher than that of existing methods.


























Similar content being viewed by others
References
Alattar AM (2004) Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans Image Process 13:1147–1156
Boehm B (2014)StegExpose - a steganalysis tool for detecting LSB steganography in images, [http://arxiv.org/abs/1410.6656]
Fridrich J, Golijan M, Du R (2001) Reliable detection of LSB steganography in grayscale and color images. Proc ACM Work Multimed Secur 27–30
Jung KH, Yoo KY (2009) Data hiding method using image interpolation. Comput Stand Interfaces 31(2):465–470
Lee CF, Huang YL (2012) An efficient image interpolation increasing payload in reversible data hiding. Expert Syst Appl 39(8):6712–6719
Li J, Li X, Yang B (2013) Reversible data hiding scheme for color image based on prediction-error expansion and cross-channel correlation. Signal Process 93:2748–2758
Tang MW, Hu J, Song W (2014) A high-capacity image steganography using multi-layer embedding. Optik 125:3972–3976
Tian J (2003) Reversible data hiding using a difference expansion. IEEE Trans Circ Syst Video Technol 13(8):890–896
Schaefer G, Stich M (2004) UCID - an uncompressed colour image database. Storage Retr Met Appl Multimedia 5037:472–480
Wittman T (2015) Mathematical techniques for image interpolation, www.math.ucla.edu/~wittman/thesis/Poral2.pdf
http://homepages.lboro.ac.uk/~cogs/datasets/ucid/ucid.html, 2015/5
Acknowledgments
This study was financially supported by a Research Grant, MOST, from Taiwan’s Ministry of Science and Technology (MOST 103-2221-E-324 -014 -).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lu, TC. Adaptive (k, F 1) interpolation-based hiding scheme. Multimed Tools Appl 76, 1827–1855 (2017). https://doi.org/10.1007/s11042-015-3168-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-3168-2