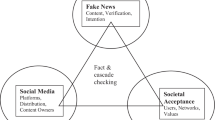
Abstract
Nowadays, information is provided through diverse network channels and, above all, its diffusion occurs in an always faster and pervasive manner. Social Media (SM) plays a crucial role in distributing, in an uncontrolled way, news, opinions, media contents and so on, and can basically contribute to spread information that sometimes are untrue and misleading. An integrated assessment of the trustworthiness of the information that is delivered is claimed from different sides: the Secure! project strictly fits in such a context. The project has been studying and developing a service oriented infrastructure which, by resorting at diverse technological tools based on image forensics, source reputation analysis, Twitter message trend analysis, web source retrieval and crawling, and so on, provides an integrated event assessment especially regarding crisis management. The aim of this paper is to present an interesting case-study which demonstrates the potentiality of the developed system to achieve a new integrated knowledge.






Similar content being viewed by others
Notes
References
Adi A, Etzion O (2004) Amit - the situation manager. VLDB J 13(2):177–203. doi:10.1007/s00778-003-0108-y
Aiello L, Petkos G, Martin C, Corney D, Papadopoulos S, Skraba R, Goker A, Kompatsiaris I, Jaimes A (2013) Sensing trending topics in twitter. IEEE Trans Multimedia 15(6):1268–1282. doi:10.1109/TMM.2013.2265080
Amerini I, Ballan L, Caldelli R, Del Bimbo A, Serra G (2011) A SIFT-based forensic method for copy move attack detection and transformation recovery. IEEE Trans Inf Forensics Secur 6(3):1099 –1110
Amerini I, Ballan L, Caldelli R, Bimbo AD, Tongo LD, Serra G (2013) Copy-move forgery detection and localization by means of robust clustering with j-linkage. Signal Process Image Commun 28(6):659–669
Amerini I, Becarelli R, Caldelli R, Casini M (2015) A feature-based forensic procedure for splicing forgeries detection Mathematical Problems in Engineering 2015. doi:10.1155/2015/653164
Boididou C, Papadopoulos S, Kompatsiaris Y, Schifferes S, Newman N (2014) Challenges of computational verification in social multimedia. In: Proceedings of the 23rd international conference on world wide web, WWW ’14 Companion. International World Wide Web Conferences Steering Committee, Republic and Canton of Geneva, Switzerland. doi:10.1145/2567948.2579323, pp 743–748
Derczynski L, Bontcheva K (2014) Pheme: veracity in digital social networks. In: Posters, demos, late-breaking results and workshop proceedings of the 22nd conference on user modeling, adaptation, and personalization co-located with the 22nd conference on user modeling, adaptation, and personalization (UMAP2014), Aalborg, Denmark, 7–11 July 2014
Derczynski L, Maynard D, Rizzo G, van Erp M, Gorrell G, Troncy R, Petrak J, Bontcheva K (2015) Analysis of named entity recognition and linking for tweets. Inf Process Manag 51(2):32–49. doi:10.1016/j.ipm.2014.10.006. http://www.sciencedirect.com/science/article/pii/S0306457314001034
Esper T, EsperTech I (2014) Esper Reference version 4.9.0. http://esper.codehaus.org
Etzion O, Niblett P (2011) Event processing in action. MANNING
Fischler MA, Bolles RC (1981) Random sample consensus: A paradigm for model fitting with applications to image analysis and automated cartography. Commun ACM 24(6):381–395. doi:10.1145/358669.358692
Gupta A, Lamba H, Kumaraguru P, Joshi A (2013) Faking sandy: characterizing and identifying fake images on twitter during hurricane sandy. In: Proceedings of the 22nd international conference on world wide web, WWW ’13 companion. International World Wide Web Conferences Steering Committee, Republic and Canton of Geneva, Switzerland, pp 729–736
Itria ML, Ceccarelli AD (2014) A complex event processing approach for crisis-management systems. In: EDCC workshop big4CIP
Jøsang A, Roslan I (2002) The beta reputation system. In: Proceedings of the 15th bled electronic commerce conference
Kumar S, Morstatter F, Liu H (2014) Twitter data analytics. Springer, Berlin Heidelberg New York
Lowe DG (2004) Distinctive image features from scale-invariant keypoints. Int J Comput Vis 60(2):91–110
Mao Z, Li N, Winsborough W. (2006) Distributed credential chain discovery in trust management with parameterized roles and constraints, vol 4307, pp 159–173
Mathioudakis M, Koudas N (2010) Twittermonitor: trend detection over the twitter stream. In: Proceedings of the 2010 ACM SIGMOD intern. conference on management of data. doi:10.1145/1807167.1807306, New York, pp 1155–1158
Middleton SE (2015) Extracting attributed verification and debunking reports from social media: mediaeval-2015 trust and credibility analysis of image and video. In: Working notes proceedings of the MediaEval 2015 workshop, Wurzen, Germany, September 14–15, CEUR-WS.org, ISSN 1613-0073. http://ceur-ws.org/Vol-1436/Paper_43.pdf
Popoola A, Krasnoshtan D, Toth AP, Naroditskiy V, Castillo C, Meier P, Rahwan I (2013) Information verification during natural disasters. In: Carr L, Laender AHF, Lscio BF, King I, Fontoura M, Vrandecic D, Aroyo L, de Oliveira JPM, Lima F, Wilde E (eds) WWW (Companion Volume). International World Wide Web Conferences Steering Committee / ACM, pp 1029–1032
Sakaki T, Okazaki M, Matsuo Y (2010) Earthquake shakes twitter users: real-time event detection by social sensors. In: Proceedings of the 19th international conference on world wide web, WWW ’10. doi:10.1145/1772690.1772777. ACM, New York, pp 851–860
Sherchan W, Nepal S, Paris C (2013) A survey of trust in social networks. ACM Comput Surv 45(4):47:1–47:33. doi:10.1145/2501654.2501661
Stamm M, Min W, Liu K (2013) Information forensics: an overview of the first decade. Access, IEEE 1:167–200. doi:10.1109/ACCESS.2013.2260814
Zubiaga A, Liakata M, Procter RN, Bontcheva K, Tolmie P (2015) Towards detecting rumours in social media. In: AAAI workshop on AI for cities
Acknowledgments
This work was partially supported by the SECURE! Project, funded by the POR CreO FESR 2007–2013 programme of the Tuscany Region (Italy).
Author information
Authors and Affiliations
Corresponding author
Appendix: Definition of terms
Appendix: Definition of terms
The term event is defined as “an occurrence within a particular system or domain; it is something that has happened, or is contemplated as having happened in that domain” [10]. In the Secure! project this definition considers those events that happen in the real world and are represented in computing systems through structured information. Hence, in the Secure! project, each event contains the texture description of the real event, the time/space (when/where it happened), the entity involved and the source that generated it. For sake of clarity we define the terms micro-event, complex-event and situation. The term micro-event refers to a simple real event involving one entity only (e.g., people, fire presence, logo recognition, weapon detection) that could be critical or not, therefore the framework needs to analyze it in detail by using other available information. On the other hand, complex-events are the aggregation, correlation and integration result of the information contained in a set of micro-events which are correlated by spatial, temporal and causal relations defined by correlation rules. A complex-event suggests a situation in progress or a part of it (e.g., people demonstration with the presence of crowd and police, vandalism smearing monuments). In the Secure! project complex-events have been classified through an event taxonomy 1. With the term situation, as defined in [1], we intend “one or more complex-event occurrence that might require a reaction”. When a critical situation happens a number of specific complex-events occur, the commixture and the correlation of them identifies the specific situation in progress requiring appropriate reactions, for example providing first aid or police intervention.
Rights and permissions
About this article
Cite this article
Amerini, I., Becarelli, R., Brancati, F. et al. Media trustworthiness verification and event assessment through an integrated framework: a case-study. Multimed Tools Appl 76, 7197–7212 (2017). https://doi.org/10.1007/s11042-016-3303-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3303-8