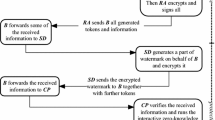
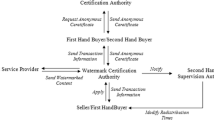
Abstract
Watermarking protocols are designed for tracing illegal distributors when unauthorized copies are found. So far, most of the proposed schemes set up two or more watermarks embedded to a copy by the seller before it was sold. The main potential concerns of multiple watermarking are the image quality would be damaged and any earlier embedded watermarks would be destroyed as well. Thanks to visual cryptography which encodes the secret image into two shares, and recovers the secret by collecting these two shares. Therefore, a new buyer-seller watermarking protocol is proposed in this paper by applying the technique of visual cryptography to Lei et al.’s scheme so as to free from the disadvantages of multiple-watermarking insertion.



Similar content being viewed by others
References
Chang CC, Chen YH, Kieu TD (2010) A watermarking technique using synonym substitution for integrity protection of XML documents. ICIC Express Lett 4(1):89–94
Chen TH, Horng G, Tsai D (2005) An anonymous buyer-reseller watermarking protocol. J Chin Inst Eng 28(3):535–538
Cheung SC, Currem H (2002) Rights protection for digital contents redistribution over the Internet. In: Proceedings of 26th Annual International Computer Software and Applications Conference, pp 105–110
Gu Q, Gao T (2009) A novel reversible watermarking algorithm based on wavelet lifting scheme. ICIC Express Lett 3(3 (A)):397–402
Horng G, Chen TH (2003) An anonymous buyer-seller watermarking protocol. Int J Comput Numer Anal Appl 4(4):423–432
Katzenbeisser S, Lemma A, Celik MU, Veen MVD, Maas M (2008) A buyer–seller watermarking protocol based on secure embedding. IEEE Trans Inf Forensics Secur 3(4):783–786
Lei CL, Yu PL, Tsai PL, Chan MH (2004) An efficient and anonymous buyer-seller watermarking protocol. IEEE Trans Image Process 13(12):1618–1626
Lin PL (2001) Digital watermarking models for resolving rightful ownership and authenticating legitimate customer. J Syst Softw 55(3):261–271
Lin PY (2014) Imperceptible visible watermarking based on postcamera histogram operation. J Syst Softw 95:194–208
Memon N, Wong PW (2001) A buyer-seller watermarking protocol. IEEE Trans Image Process 10(4):643–649
Naor M, Shamir A (1995) Visual cryptography. In: Proceedings of EUROCRYPT’94, LNCS, 950, pp 1–12
Pei SC, Guo JM, Lee H (2005) Novel robust watermarking technique dithering halftone images. IEEE Signal Process Lett 12(4):333–336
Qi X, Qi J (2007) A robust content-based digital image watermarking scheme. Signal Process 87(6):1264–1280
Qian L, Nahrstedt K (1998) Watermarking schemes and protocols for protecting rightful ownership and customer’s rights. J Vis Commun Image Represent 9(3):194–210
Qin C, Chang CC, Huang YH, Liao LT (2013) An inpainting-assisted reversible steganographic scheme using a histogram shifting mechanism. IEEE Trans Circuits Syst Video Technol 23(7):1109–1118
Qin C, Chang CC, Chen PY (2012) Self-embedding fragile watermarking with restoration capability based on adaptive bit allocation mechanism. Signal Process 92(4):1137–1150
Qin C, Chang CC, Chiu YP (2014) A novel joint data-hiding and compression scheme based on SMVQ and image inpainting. IEEE Trans Image Process 23(3):969–978
Qin C, Chang CC, Hsu TJ (2015) Reversible data hiding scheme based on exploiting modification direction with two steganographic images. Multimedia Tools Appl 74(15):5861–5872
Rivest RL, Shamir A, Adleman L (1978) A method for obtaining digital signatures and public-key cryptosystems. Commun ACM 21(2):120–126
Shieh JM, Lou DC, Chang MC (2006) A semi-blind digital watermarking scheme based on singular value decomposition. Comput Stand Interfaces 28(4):428–440
Subramanyam AV, Emmanue S, Kankanhalli MS (2012) Robust watermarking of compressed and encrypted JPEG2000 images. IEEE Trans Multimedia 14:703–716
Wu Y, Pang H (2008) A lightweight buyer-seller watermarking protocol. Adv Multimedia 2008:1–7
Yang CY, Hu WC, Hwang WY, Cheng YF (2010) A simple digital watermarking by the adaptive bit-labeling scheme. Int J Innov Comput Inf Control 6(3(B)):1401–1410
Zhang J, Kou W, Fan K (2006) Secure buyer-seller watermarking protocol. IEEE Proc Inf Secur 153(1):15–18
Acknowledgments
This work was partially supported National Science Council, Taiwan, R.O.C., under contract by NSC 102-2221-E-415-014 and NSC 102-2221-E-415-007.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Huang, JC., Jeng, FG. & Chen, TH. A new buyer-seller watermarking protocol without multiple watermarks insertion. Multimed Tools Appl 76, 9667–9679 (2017). https://doi.org/10.1007/s11042-016-3573-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3573-1