Abstract
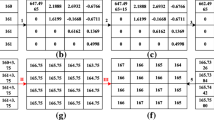
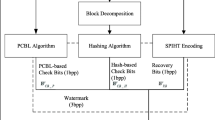
Here, we present a novel method for data protection to resolve the issue of mass-tampered regions of image watermarks. Our approach involves asymmetric cryptography and follows the nonspatial domain technique, where a codebook exists as a public key and a verification code exists as a private key. There are two major components to our study: self-recovery images and sparse approximation. Specifically, we generate self-recovery images on the basis of our previous research, and to generate verification codes, we mark data with the maximum coefficient resulting from the sparse approximation. The above approach processes 4 × 4 blocks of the given images. The results demonstrate that each block processed by the sparse approximation algorithm has its main texture feature associated with a codeword with a higher sparse coefficient value than the codebook. This provides a robust method to protect data via watermarking and to verify the copyright of the data. Our proposed method efficiently supports compression for transmission via popular communication applications. Using our method under common conditions, we confirmed an outstanding unit correction rate of approximately 90 %, especially for crop-attacked images.












Similar content being viewed by others
References
Bertalmio M, Sapiro G, Caselles V, Ballester C (2000) Image inpainting. Proc. ACM Conf. Comp. Graphics (SIGGRAPH), pp. 417–424
Breen P (2009) Algorithms for sparse approximation‖. In: Year 4 Project, School of Mathematics, University of Edinburgh
Chang C-C, Tseng H-W (2004) VQ-based image watermarking using anti-gray coding. Inst Math Inform Vilnius 15(2):147–160
Criminisi A, Perez P, Toyama K (2004) Region filling and object removal by exemplar-based image inpainting. IEEE Trans Image Process 13(9):1200–1212
Kang L-W, Lin C-W, Lin C-T, Lin Y-C (2012) Self-learning-based rain streak removal for image/video. IEEE International Symposium on Circuits and Systems (ISCAS), pp. 1871–1874
Lee T-Y, Lin SD (2008) Dual watermark for image tamper detection and recovery. Pattern Recogn 14(11):3497–3506
Lin PL, Hsieh C-K, Huang P-W (2005) A hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recogn 38(12):2519–2529
Linde Y, Buzo A, Gray RM (1980) An algorithm for vector quantizer design. IEEE Trans Commun 28(1):84–95
Qin C, Chang C-C, Chen P-Y (2012) Self-embedding fragile watermarking with restoration capability based on adaptive bit allocation mechanism. Signal Process 92(4):1137–1150
Qin C, Chang C-C, Hsu T-J (2014) Reversible data hiding scheme based on exploiting modification direction with two steganographic images. Multimed Tools Appl 74(15):5861–5872
Qin C, Zhang X (2015) Effective reversible data hiding in encrypted image with privacy protection for image content. J Vis Commun Image Represent 31:154–160
Shih TK, Chang R-C (2005) Digital inpainting - survey and multilayer image inpainting algorithms. Inf Technol Appl (ICITA) 1:15–24
Tropp JA (2004) Greed is good: algorithmic results for sparse approximation. IEEE Trans Inf Theory 50(10):2231–2242
Tropp JA, Gilbert AC (2007) Signal recovery from random measurements via orthogonal matching pursuit. IEEE Trans Inf Theory 53(12):4655–4666
Voyatzis G, Pitas I (1996) Chaotic mixing of digital images and applications to watermarking. Proc Eur Conf Multimed Appl Syst Tech (ECMAST’96) II:687–694
Wang H-C, Chen W-M, Hsieh Y-H (2014) Imperceptible watermark research based on sparse approximation. IJEE 21(3)
Wang H-C, Chen W-M, Lee P-Y (2015) Image tamper detection and recovery based on dilation and chaotic mixing. Comput Sci Inf Technol 3(4):127–132
Wei L-Y, Levoy M (2000) Fast texture synthesis using tree-structured vector quantization. Proc. ACM Conf. Comp. Graphics (SIGGRAPH), pp. 479–488
Zhang X, Wang S (2007) Statistical fragile watermarking capable of locating individual tampered pixels. IEEE Signal Process Lett 14:727–730
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, HC., Chen, IY. & Chen, WM. Image watermark protection based on self-recovery images and sparse approximation. Multimed Tools Appl 76, 9929–9941 (2017). https://doi.org/10.1007/s11042-016-3588-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3588-7