Abstract
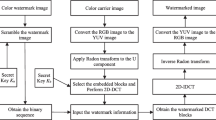
This study proposes a scheme for using modified coefficients of the DCT of an image to generate a lossless visible watermark. The major contribution of the proposed technique is the improved security against attack to remove watermarks under stricter assumption of Kerckhoffs’ principle. After the host images and watermarks are decomposed into several frequencies, the DCT coefficients of the watermark are embedded into the DCT coefficients of the host image. Integer mapping is then used to perform 2-dimensional DCT. The major advantage of the method is the improved security achieved by using a random permutation matrix to factorize the transformation matrix. That is, since the embedding stage multiplies the transformation matrix by a random permutation matrix, illicit users, even under the stricter assumption of Kerckhoffs principle that the proposed embedding method is known by illicit users, cannot properly recover the host image without the correct permutation matrix. Unlike methods that embed the watermark in quantized frequency-domain coefficients, the watermarked image remains in raw lossless image form instead of some lossy form of quantized coefficients e.g., JPEG-formatted. Maintaining the lossless format of the watermarked image provides reversibility.









Similar content being viewed by others
References
Abu-Marie W, Gutub A, Abu-Mansour H (2010) Image based steganography using truth table based and determinate array on RGB indicator. Int. J. Signal Image Process. (IJSIP) 1(3):196– 204
Al-Otaibi N, Gutub A (2014) 2-leyer security system for hiding sensitive text data on personal computers. Lect Notes Inf Theory 2(2):151–157
Al-Otaibi N, Gutub A, Khan E (2015) Stego-system for hiding text in images of personal computers, the 12th learning and technology conference: wearable tech/wearable learning. Effat University, Jeddah, Kingdom of Saudi Arabia, pp 12–13
Bender W, Gruhl D, Morimoto N, Lu A (1996) Techniques for data hiding. IBM Syst J 35:313–316
Farrugia FA (2010) A reversible visible watermarking scheme for compressed images. MELECON 2010 - 2010 15th IEEE Mediterranean Electrotechnical Conference, pp 212–217
Hao P, Shi Q (2001) Matrix factorizations for reversible integer mapping. IEEE Trans Signal Process 49(10):2314–2324
Hu Y, Jeon B (2006) Reversible visible watermarking and lossless recovery of original images. IEEE Trans Circ Syst Video Technol 16(11):1423–1429
Kerckhoffs A (1883) La cryptographie militaire. J Sci Militaires IX(5-83):161–191
Li X, Yang B, Cheng DF, Zeng TY (2009) A generalization of LSB matching. IEEE Signal Process Lett 16(2):69–72
Lin SD, Shie SC Improving robustness of visible watermarking schemes for images. the 2004 IEEE International Symposium on Consumer Electronics (ISCE2004)
Lin YK (2012) High capacity reversible data hiding scheme based upon discrete cosine transformation. J Syst Softw 85(10):2395–2404
Liu TY, Tsai WH (2010) Generic lossless visible watermarking – A new approach. IEEE Trans Image Process 19(5):1224–1235
Mohanty SP, Ramakrishnan KR, Kankanhal MS (2000) A DCT domain visible watermarking technique for images. In: Proceeding of IEEE International Conference of Multimedia and Expo, vol 2, pp 1029–1032
Rao KR, Yip P (1990) Discrete cosine transform: algorithms, advantages, applications. Academic Press, Boston
Sinduja R, Rachel RL, Sathiya RD (2012) A novice approach for lossless visible watermarking approach by pioneering the best block (LVW-PBB), Computer and Information Science, vol 270. Springer,
Tsai HM, Chang LW (2007) A high secure reversible visible watermarking scheme. In: Proceeding of IEEE International Conference of Multimedia and Expo, Beijing, China, pp 2106–2109
Wu MH, Hsu FH, Yang CH, Wang SJ (2011) Reversible watermarking scheme with visibility using randomize distance. ICGEC,
Yang Y, Sun X, Yang H, Li C (2008) Removable visible image watermarking algorithm in the discrete cosine transform domain. J Electron Imaging 17(3):1–11
Yang Y, Sun X, Yang H, Li C, Xiao R (2009) A contrast-sensitive reversible visible image watermarking technique. IEEE Trans Circ Syst Video Technol 19(5)
Yip SK, Au OC, Ho CW, Wong HM (2006) Lossless visible watermarking. In: Proceeding of International Conference of Multimedia and Expo, pp 2106–2109
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lin, YK., Yang, CH. & Tsai, JT. More secure lossless visible watermarking by DCT. Multimed Tools Appl 77, 8579–8601 (2018). https://doi.org/10.1007/s11042-017-4753-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4753-3