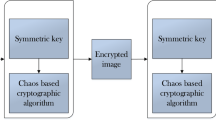
Abstract
Today, medical imaging suffers from serious issues such as malicious tampering and privacy leakage. Encryption is an effective way to protect these images from security threats. Among the available encryption algorithms, chaos-based methods have strong cryptographic properties, because chaotic systems are sensitive to initial conditions and parameters. However, traditional chaotic systems are easy to build, analyze, predict and can be re-scaled to any desired frequency. Thus, encryption schemes using traditional chaotic systems have low security levels. In this work, we propose a new simple chaotic system that utilizes a hyperbolic sine as its nonlinearity; this nonlinearity has rarely appeared in previous studies. Furthermore, the new chaotic system uses a decorrelation operation to enhance its performance. Statistical testing verifies that the chaotic sequence has good pseudorandom characteristics. In this study, we propose a scheme for medical image encryption based on this new chaotic system. The results of tests show that this encryption method can encrypt images effectively in a single round and that the proposed scheme provides sufficient security against known attacks.












Similar content being viewed by others
References
Collen MF, Ball MJ (eds) (2015) The history of medical informatics in the United States. Springer, Berlin
Cui J, Liu Y, Xu Y, Zhao H, Zha H (2013) Tracking generic human motion via fusion of low- and high-dimensional approaches. IEEE Transactions on Systems Man & Cybernetics Systems 43(4):996–1002
Gutub AAA, Tabakh AA, Al-Qahtani A, Amin A (2013) Serial vs. parallel elliptic curve crypto processor designs. In IADIS International Conference: Applied Computing, pp 67–74
Hamza R (2017) A novel pseudo random sequence generator for image-cryptographic applications. J Inf Secur Appl 35:119–127
Hamza R, Titouna F (2016) A novel sensitive image encryption algorithm based on the Zaslavsky chaotic map. Information Security Journal: A Global Perspective 25(4–6):162–179
Hamza R, Muhammad K, Lv Z, Titouna F (2017) Secure video summarization framework for personalized wireless capsule endoscopy. Pervasive Mob Comput 41:436–450
Hu HP, Liu LF, Ding ND (2013) Pseudorandom sequence generator based on the chen chaotic system. Comput Phys Commun 184(3):765–768
Jiunn-Woei L, Yen DC, Wang Y-T (2014) An exploratory study to understand the critical factors affecting the decision to adopt cloud computing in Taiwan hospital. Int J Inf Manag 34(1):28–36
Kumar S, Sharma RK (2017) Securing color images using two-square cipher associated with Arnold map. Multimed Tools Appl 76(6):8757–8779
Li C, Sprott JC (2014) Coexisting hidden attractors in a 4-D simplified Lorenz system. Int J Bifurcation Chaos 24(03):1450034
Li C, Sprott JC (2014) Finding coexisting attractors using amplitude control. Nonlinear Dynam 78(3):2059–2064
Lima JB, Madeiro F, Sales FJR (2015) Encryption of medical images based on the cosine number transform. Signal Process Image Commun 35:1–8
Liu Y, Luo Y, Song S, Cao L, Liu J, Harkin J (2017) Counteracting dynamical degradation of digital chaotic Chebyshev map via perturbation. Int J Bifurcation Chaos 27(03):1750033
Liu J, Sprott JC, Wang S, Ma Y (2018) Simplest chaotic system with a hyperbolic sine and its applications in DCSK Scheme. IET Communications. https://doi.org/10.1049/iet-com.2017.0455
Mantos PL, Maglogiannis I (2016) Sensitive patient data hiding using a ROI reversible steganography scheme for DICOM images. J Med Syst 40(6):156
Munmuangsaen B, Srisuchinwong B, Sprott JC (2011) Generalization of the simplest autonomous chaotic system. Phys Lett A 375(12):1445–1450
Pan SM, Wen RH, Zhou ZH, Zhou NR (2017) Optical multi-image encryption scheme based on discrete cosine transform and nonlinear fractional Mellin transform. Multimed Tools Appl 76(2):2933–2953
Parvees MM, Samath JA, Bose BP (2016) Secured medical images-a chaotic pixel scrambling approach. J Med Syst 40(11):232
Parvez MT, Gutub AAA (2011) Vibrant color image steganography using channel differences and secret data distribution. Kuwait J Sci Eng 38(1B):127–142
Pham VT, Volos C, Jafari S, Kapitaniak T (2017) A novel cubic–equilibrium chaotic system with coexisting hidden attractors: analysis, and circuit implementation. J Circuits Syst Comput 27(04):1850066. https://doi.org/10.1142/S0218126618500664
Piper JR, Sprott JC (2010) Simple autonomous chaotic circuits. IEEE Trans Circuits Syst II Express Briefs. 57(9):730–734
Sajjad M, Muhammad K, Baik SW, Rho S, Jan Z, Yeo SS, Mehmood I (2017) Mobile-cloud assisted framework for selective encryption of medical images with steganography for resource-constrained devices. Multimed Tools Appl 76(3):3519–3536
Sprott JC (2011) A new chaotic jerk circuit. IEEE Trans Circuits Syst II Express Briefs 58(4):240–243
Sun XH (2013) Image encryption algorithms and practices with implementations in C#. Sciencepress, Beijing
Wang X, Vaidyanathan S, Volos C, Pham VT, Kapitaniak T (2017) Dynamics, circuit realization, control and synchronization of a hyperchaotic hyperjerk system with coexisting attractors. Nonlinear Dynam 89(3):1673–1687
Weaver CA, Ball MJ, Kim GR, Kiel JM (2016) Healthcare information management systems. Springer International Publishing, Cham
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI randomness tests for image encryption. Cyber journals: multidisciplinary journals in science and technology. Journal of Selected Areas in Telecommunications (JSAT) 2:31–38
Xu Y, Wang H, Li Y, Pei B (2014) Image encryption based on synchronization of fractional chaotic systems. Commun Nonlinear Sci Numer Simul 19(10):3735–3744
Zhang YQ, Wang XY (2014) A symmetric image encryption algorithm based on mixed linear–nonlinear coupled map lattice. Inf Sci 273(8):329–351
Zhang Y, Qiu M, Tsai CW, Hassan MM, Alamri A (2015) Health-CPS: healthcare cyber-physical system assisted by cloud and big data. IEEE Syst J 11(1):88–95
Acknowledgements
The authors would like to thank Wenlong Xin for providing knowledge of the medical images. All the medical images used are from the First Hospital affiliated with Lanzhou University and the DICOM database. This study was supported by Fundamental Research Funds for the Central Universities No. lzujbky-2016-238) and the National Natural Science Foundation of China (No. 61175012).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, J., Ma, Y., Li, S. et al. A new simple chaotic system and its application in medical image encryption. Multimed Tools Appl 77, 22787–22808 (2018). https://doi.org/10.1007/s11042-017-5534-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-5534-8