Abstract
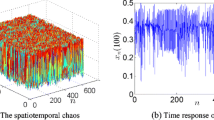
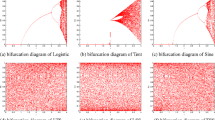
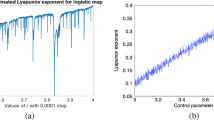
Image encryption is an efficient technique for image protection. This paper presents a double color image encryption (DCIE) scheme based on three-dimensional (3D) Brownian motion. The architecture of diffusion, confusion and diffusion is adopted. The proposed algorithm firstly decomposes two color plain images into R, G, B components and bit planes, then conducts XOR operation between every bit plane and a key bit plane generated from carrier images; next, arranges all the bit planes into a 3D bit matrix, performs block-in 3D Brownian motion confusion and block confusion on it, which can permute the elements across bit planes and across plain images; finally, a subsequent diffusion process is utilized to improve the encryption effect. Simulation results and performance analyses illustrate that the proposed encryption scheme can simultaneously encrypt two color images into noise-like ones that have strong ability of resisting various known attacks.


















Similar content being viewed by others
References
Bakshandeh A, Eslami Z (2013) An authenticated image encryption scheme based on chaotic maps and memory cellular automata. Opt Lasers Eng 51:665–673
Chai XL, Chen YR, Broyde L (2017) A novel chaos-based image encryption algorithm using DNA sequence operations. Opt Lasers Eng 88:197–213
Chai XL, Gan ZH, Lu Y, Zhang MH, Chen YR (2016) A novel color image encryption algorithm based on genetic recombination and the four-dimensional memristive hyperchaotic system. Chin Phys B 25(10):1–13
Chai XL, Gan ZH, Chen YR, Zhang YSA (2017) Visually secure image encryption scheme based on compressive sensing. Signal Process 134(5):35–51
Chai XL, Gan ZH, Yuan K, Yang L, Chen YR (2017) An image encryption scheme based on three-dimensional Brownian motion and chaotic system. Chin Phys B 26:020504
Chanil P, Huang LL (2017) A new color image encryption using combination of the 1D chaotic map. Signal Process 138:129–137
Chen JX, Zhu ZL, Liu ZJ, Fu C, Zhang LB, Yu H (2014) A novel double-image encryption scheme based on cross-image pixel scrambling in gyrator domains. Opt Express 22:7349–7361
Chen JX, Zhu ZLFC, Zhang LB, Analysis YH (2015) Improvement of a double-image encryption scheme using pixel scrambling technique in gyrator domains. Opt Lasers Eng 66:1–9
Di H, Zheng K, Zhang X, Lam EY, Kim T, Kim YS et al (2012) Multiple-image encryption by compressive holography. Appl Opt 51:1000–1009
Faraoun KM (2014) Fast encryption of RGB color digital images using a tweakable cellular automaton based schema. Opt Laser Technol 64:145–155
Gonzalez RC, Woods RE (2008) Digital image processing, 3rd edition, Pearson Prentice Hall, upper Saddle River, New Jersey, ISBN: 9780131687288
Hua ZY, Zhou YC (2016) Image encryption using 2D logistic-adjusted-sine map. Inf Sci 339:237–253
Hua ZY, Zhou YC (2017) Design of image cipher using block-based scrambling and image filtering. Inf Sci 396:97–113
Li HJ, Wang YR, Yan HT, Li LB, Li QZ, Zhao XY (2013) Double-image encryption by using chaos-based local pixel scrambling technique and gyrator transform. Opt Lasers Eng 51:1327–1331
Li JZ, Lin Q, Yu CY, Ren XC, Li P (2016) A QDCT- and SVD-based color image watermarking scheme using an optimized encrypted binary computer-generated hologram. Soft Comput 22:47–65
Li P, Li T, Yao ZA, Tang CM, Li J (2017) Privacy-preserving outsourcing of image feature extraction in cloud computing. Soft Comput 21:4349–4359
Lin C, Shen X, Tang R, Zou X (2012) Multiple images encryption based on Fourier transform hologram. Opt Commun 285:1023–1028
Liu ZJ, Zhang Y, Li S, Liu W, Liu WY, Wang YH, Liu ST (2013) Double image encryption scheme by using random phase encoding and pixel exchanging in the gyrator transform domains. Opt Laser Technol 47:152–158
Liu JM, Qu Q, Li GJ (2015) A new six-term 3-D chaotic system with fan-shaped Poincare maps. Nonlinear Dyn 82:2069–2079
Mirzaei O, Yaghoobi M, Irani H (2012) A new image encryption method: parallel sub-image encryption with hyper chaos. Nonlinear Dyn 67:557–566
del Rey AM, Pastora JLH, Sanchez GR (2016) 3D medical data security protection. Expert Syst Appl 54:379–386
Shan MG, Chang J, Zhong Z, Hao BG (2012) Double image encryption based on discrete multiple-parameter fractional Fourier transform and chaotic maps. Opt Commun 285:4227–4234
Situ GH, Zhang JJ (2005) Multiple-image encryption by wavelength multiplexing. Opt Lett 30:1306–1308
Souyah A, Faraoun KM (2016) Fast and efficient randomized encryption scheme for digital images based on Quadtree decomposition and reversible memory cellular automata. Nonlinear Dyn 84:715–732
Sui LS, Liu BQ, Wang Q, Li Y, Liang JL (2015) Double-image encryption based on Yang-Gu mixture amplitude-phase retrieval algorithm and high dimension chaotic system in gyrator domain. Opt Commun 354:184–196
Tang ZJ, Song J, Zhang XQ, Sun RH (2016) Multiple-image encryption with bit-plane decomposition and chaotic maps. Opt Lasers Eng 80:1–11
Tang ZJ, Wang F, Zhang XQ (2017) Image encryption based on random projection partition and chaotic system. Multimed Tools Appl 76:8257–8283
Wan YH, Wu F, Yang JH, Man TL (2015) Multiple-image encryption based on compressive holography using a multiple-beam interferometer. Opt Commun 342:95–101
Wang X, Luan D (2013) A novel image encryption algorithm using chaos and reversible cellular automata. Commun Nonlinear Sci Numer Simul 18:3075–3085
Wang XY, Xu DH (2014) A novel image encryption scheme based on Brownian motion and PWLCM chaotic system. Nonlinear Dyn 75:345–353
Wang X, Teng L, Qin X (2012) A novel colour image encryption algorithm based on chaos. Signal Process 92:1101–1108
Wang Q, Guo Q, Lei L (2014) Multiple-image encryption system using cascaded phase mask encoding and a modified Gerchberg-Saxton algorithm in gyrator domain. Opt Commun 320:12–21
Wang Y, Zhang X, Zheng ZM, Qiu WJ (2015) A colour image encryption algorithm using 4-pixel Feistel structure and multiple chaotic systems. Nonlinear Dyn 81:151–168
Wang Y, Quan C, Tay CJ (2016) Asymmetric optical image encryption based on an improved amplitude-phase retrieval algorithm. Opt Lasers Eng 78:8–16
Wu JH, Luo XZ, Zhou NR (2013) Four-image encryption method based on spectrum truncation. Chaos and the MODFrFT. Opt Laser Technol 45:571–577
Wu Y, Zhou YC, George S, Sos A, Noonan Joseph P, Premkumar N (2013) Local Shannon entropy measure with statistical tests for image randomness. Inf Sci 222:323–342
Wu XJ, Bai CX, Kan HB (2014) A new color image cryptosystem via hyperchaos synchronization. Commun Nonlinear Sci Numer Simul 19:1884–1897
Wu JJ, Xie ZW, Liu ZJ, Liu W, Zhang Y, Liu ST (2016) Multiple-image encryption based on computational ghost imaging. Opt Commun 359:38–43
Wu XJ, Wang DW, Kurths J, Kan HB (2016) A novel lossless color image encryption scheme using 2D DWT and 6D hyperchaotic system. Inf Sci 349-350:137–153
Wu JH, Liao XF, Yang B (2018) Cryptanalysis and enhancements of image encryption based on three-dimensional bit matrix permutation. Signal Process 142:292–300
Xu J, Wei LW, Zhang Y, Wang AD, Zhou FC, Gao CZ (2018) Dynamic fully homomorphic encryption-based merkle tree for lightweight streaming authenticated data structures. J Netw Comput Appl 107:113–124. https://doi.org/10.1016/j.jnca.2018.01.014
Ye GD, Zhou JW (2014) A block chaotic image encryption scheme based on self-adaptive modelling. Appl Soft Comput 22:351–357
Zhang YQ, Wang XY (2014) A symmetric image encryption algorithm based on mixed linear- nonlinear coupled map lattice. Inf Sci 273:329–351
Zhang XQ, Wang XS (2017) Multiple-image encryption algorithm based on mixed image element and permutation. Opt Lasers Eng 92:6–16
Zhang YS, Xiao D (2013) Double optical image encryption using discrete Chirikov standard map and chaos-based fractional random transform. Opt Lasers Eng 51:472–480
Zhang YS, Xiao D (2014) Self-adaptive permutation and combined global diffusion for chaotic color image encryption. Int J Electron Commun 68:361–368
Zhang XP, Zhao ZM, Wang JY (2014) Chaotic image encryption based on circular substitution box and key stream buffer. Signal Process: Image 29:902–913
Zhang W, Yu H, Zhao YL, Zhu ZL (2016) Image encryption based on three-dimensional bit matrix permutation. Signal Process 118:36–50
Zhou YC, Panetta K, Agaian S, Chen CLP (2012) Image encryption using p-Fibonacci transform and decomposition. Opt Commun 285:594–608
Zhou Y, Bao L, Chen CP (2014) A new 1D chaotic system for image encryption. Signal Process 97:172–182
Zhou NR, Yang JP, Tan CF, Pan SM, Zhou ZH (2015) Double-image encryption scheme combining DWT-based compressive sensing with discrete fractional random transform. Opt Commun 354:112–121
Zhou NR, Pan SM, Cheng S, Efficient ZZH (2016) Image compression-encryption scheme based on hyper-chaotic system and 2D compressive sensing. Opt Laser Technol 82:121–133
Acknowledgements
All the authors are deeply grateful to the editors for smooth and fast handling of the manuscript. The authors would also like to thank the anonymous referees for their valuable suggestions to improve the quality of this paper. This work is supported by the National Natural Science Foundation of China (Grant No. 41571417, U1604145 and U1404618), National Science Foundation of the United States (Grant No. CNS-1253424 and ECCS-1202225), Science and Technology Foundation of Henan Province of China (Grant No. 182102210027, 182102210238, and 172102210186), China Postdoctoral Science Foundation (Grant No. 2016M602235 and 2015M582182) and the Research Foundation of Henan University (Grant No. xxjc20140006).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Gan, Z., Chai, X., Zhang, M. et al. A double color image encryption scheme based on three-dimensional brownian motion. Multimed Tools Appl 77, 27919–27953 (2018). https://doi.org/10.1007/s11042-018-5974-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-5974-9