Abstract
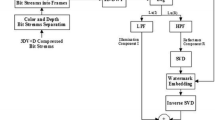
This paper presents two robust hybrid watermarking techniques for securing the Three-Dimensional High Efficiency Video Coding (3D-HEVC). The first watermarking technique is the homomorphic-transform-based Singular Value Decomposition (SVD) in Discrete Wavelet Transform (DWT) domain. The second watermarking technique is the three-level Discrete Stationary Wavelet Transform (DSWT) in Discrete Cosine Transform (DCT) domain. The objective of the two proposed hybrid watermarking techniques is to increase the immunity of the watermarked 3D-HEVC streams to attacks. Also, we propose a wavelet-based fusion technique to combine two depth watermark frames into one fused depth watermark frame. Then, the resultant fused depth watermark is encrypted using chaotic Baker map to increase the level of security. After that, the resultant chaotic encrypted fused depth watermark is embedded in the 3D-HEVC color frames using the proposed hybrid watermarking techniques to produce the watermarked 3D-HEVC streams. In addition to achieving multi-level security in the transmitted 3D-HEVC streams, the proposed hybrid techniques reduce the required bit rate for transmitting the color-plus-depth 3D-HEVC data over limited-bandwidth networks. The performance of the proposed hybrid techniques is compared with those of the state-of-the-art techniques. Extensive simulation results on standard 3D video sequences have been conducted in the presence of attacks. The obtained results confirm that the proposed hybrid fusion-encryption-watermarking techniques achieve not only a good perceptual quality with high Peak Signal-to-Noise Ratio (PSNR) values and less bit rate, but also high correlation coefficient values between the original and extracted watermarks in the presence of attacks. Furthermore, the proposed hybrid techniques improve the capacity of information embedding and the robustness without affecting the perceptual quality of the original 3D-HEVC frames. Indeed, the extraction of the encrypted, fused, primary, and secondary depth watermark frames is possible in the presence of attacks.










Similar content being viewed by others
References
Abu-Marie W, Gutub A, Abu-Mansour H (2010) Image based steganography using truth table based and determinate array on rgb indicator. Int J Signal Image Process 1(3):196–204
Al-Otaibi A, Gutub A (2014) 2-leyer security system for hiding sensitive text data on personal computers. Lect Notes Inform Theory 2:151–157
Al-Otaibi A, Gutub A (2014) Flexible stego-system for hiding text in images of personal computers based on user security priority. In: International Conference on Advanced Engineering Technologies (AET) pp 250–256
Alotaibi N, Gutub A, Khan E (2015) Stego-system for hiding text in images of personal computers. In: The 12th learning and technology conference: wearable tech/wearable learning
Bhimani J, Mi N, Leeser M, Yang Z (2017) FiM: performance prediction for parallel computation in iterative data processing applications. In: IEEE 10th International Conference on Cloud Computing (CLOUD) pp 359–366
Bhimani J, Yang Z, Leeser M, Mi N (2017) Accelerating big data applications using lightweight virtualization framework on enterprise cloud. In: IEEE High Performance Extreme Computing Conference (HPEC) pp 1–7
Campisi P (2008) Object-oriented stereo-image digital watermarking. J Electron Imaging 17(4):043024
Dutta T, Gupta P (2016) A robust watermarking framework for high efficiency video coding (HEVC)–encoded video with blind extraction process. J Vis Commun Image Represent 38:29–44
Dutta T, Sur A, Nandi S (2013) A robust compressed domain video watermarking in P-frames with controlled bit rate increase. In: National Conference on Communications (NCC) pp 1–5
Esen E, Alatan A (2011) Robust video data hiding using forbidden zone data hiding and selective embedding. IEEE Trans Circuits Syst Video Technol 21(8):1130–1138
Franco-Contreras J, Baudry S, Doërr G (2011) Virtual view invariant domain for 3D video blind watermarking. In: IEEE 18th International Conference on Image Processing (ICIP) pp 2761–2764
Gao H, Yang Z, Bhimani J, Wang T, Wang J, Sheng B, Mi N (2017) AutoPath: harnessing parallel execution paths for efficient resource allocation in multi-stage big data frameworks. In: IEEE 26th International Conference on Computer Communication and Networks (ICCCN) pp 1–9
Gutub A (2010) Pixel indicator technique for RGB image steganography. J Emerg Technol Web Intell 2(1):56–64
Gutub A, Ankeer M, Abu-Ghalioun M, Shaheen A, Alvi A (2008) Pixel indicator high capacity technique for RGB image based Steganography. In: IEEE 5th International Workshop on Signal Processing and its Applications (WoSPA)
Gutub A, Al-Juaid N, Khan E (2017) Counting-based secret sharing technique for multimedia applications. Multimed Tools Appl 1–29. https://doi.org/10.1007/s11042-017-5293-6
Hartung F, Girod B (1998) Watermarking of uncompressed and compressed video. Signal Process 66(3):283–301
HEVC Reference Software (2014) http://hevc.kw.bbc.co.uk/trac/browser/jctvc-hm/tags
Joshi M, Gupta S, Girdhar M, Agarwal P, Sarker R (2017) Combined DWT–DCT-based video watermarking algorithm using Arnold transform technique. In: International conference on data engineering and communication technology. Singapore: Springer pp 455–463
Khalid A (2017) Utilization of watermarking schemes for securing digital images. Master Thesis, Department of Computer Science and Engineering, Faculty of Electronic Engineering, Menoufia University
Khan F, Gutub A (2007) Message concealment techniques using image based steganography. In: IEEEGCC
Kim D, Lee W, Oh W, Lee K (2012) Robust DT-CWT watermarking for DIBR 3D images. IEEE Trans Broadcast 58(4):533–543
Kuo Y, Lo C (2010) A hybrid scheme of robust and fragile watermarking for H.264/AVC video. In: IEEE international symposium on Broadband Multimedia Systems and Broadcasting (BMSB) pp 1–6
Lin H, Wu L (2011) A digital blind watermarking for depth-image-based rendering 3D images. IEEE Trans Broadcast 57(2):602–611
Mueller K, Vetro A (2014) Common test conditions of 3D-MVV core experiments. Joint Collaborative Team on 3D Video Coding Extensions JCT3V-G1100, 7th Meeting: San Jose, USA
Niu Y, Souidene W, Beghdadi A (2011) A visual sensitivity model based stereo image watermarking scheme. In: IEEE 3rd European Workshop on Visual Information Processing (EUVIP) pp 211–215
Noorkami M, Mersereau M (2005) Compressed-domain video watermarking for H.264. In: IEEE International Conference on Image Processing (ICIP) pp II–890
Noorkami M, Mersereau M (2007) A framework for robust watermarking of H.264-encoded video with controllable detection performance. IEEE Trans Inf Forensics Secur 2(1):14–23
Noorkami M, Mersereau M (2008) Digital video watermarking in P-frames with controlled video bit-rate increase. IEEE Trans Inf Forensics Secur 3(3):441–455
Ogawa K, Ohtake G (2015) Watermarking for HEVC/H.265 stream. In: IEEE International Conference on Consumer Electronics (ICCE) pp 102–103
Parvez T, Gutub A (2011) Vibrant color image steganography using channel differences and secret data distribution. Kuwait J Science Eng 38(1):127–142
Purica I, Mora G, Pesquet-Popescu B, Cagnazzo M, Ionescu B (2016) Multiview plus depth video coding with temporal prediction view synthesis. IEEE Trans Circuits Syst Video Technol 26(2):360–374
Qiu G, Marziliano P, Ho T, He D, Sun Q (2004) A hybrid watermarking scheme for H. 264/AVC video. In: 17th International Conference on Pattern Recognition (ICPR) pp 865–868
Singh D, Singh K (2017) DWT-SVD and DCT based robust and blind watermarking scheme for copyright protection. Multimed Tools Appl 76(11):13001–13024
Stütz T, Autrusseau F, Uhl A (2014) Non-blind structure-preserving substitution watermarking of H.264/CAVLC inter-frames. IEEE Trans Multimed 16(5):1337–1349
Su C, Wu S, Chen F, Wu Y, Wu C (2011) A practical design of digital video watermarking in H.264/AVC for content authentication. Signal Process Image Commun 26(8):413–426
Swati S, Hayat K, Shahid Z (2014) A watermarking scheme for high efficiency video coding (HEVC). PLoS One 9(8):e105613
Tew Y, Wong K (2014) An overview of information hiding in H.264/AVC compressed video. IEEE Trans Circuits Syst Video Technol 24(2):305–319
Wang S, Cui C, Niu X (2014) Watermarking for DIBR 3D images based on SIFT feature points. Measurement 48:54–62
Xu D, Wang R, Wang J (2011) A novel watermarking scheme for H.264/AVC video authentication. Signal Process Image Commun 26(6):267–279
Yan C, Zhang Y, Xu J, Dai F, Li L, Dai Q, Wu F (2014) A highly parallel framework for HEVC coding unit partitioning tree decision on many-core processors. IEEE Signal Process Lett 21(5):573–576
Yan C, Zhang Y, Xu J, Dai F, Zhang J, Dai Q, Wu F (2014) Efficient parallel framework for HEVC motion estimation on many-core processors. IEEE Trans Circuits Syst Video Technol 24(12):2077–2089
Yan C, Xie H, Liu S, Yin J, Zhang Y, Dai Q (2018) Effective Uyghur language text detection in complex background images for traffic prompt identification. IEEE Trans Intell Transp Syst 19(1):220–229
Yan C, Xie H, Yang D, Yin J, Zhang Y, Dai Q (2018) Supervised hash coding with deep neural network for environment perception of intelligent vehicles. IEEE Trans Intell Transp Syst 19(1):284–295
Yang Z, Wang J, Evans D, Mi N (2016) AutoReplica: automatic data replica manager in distributed caching and data processing systems. In: IEEE 35th International Performance Computing and Communications Conference (IPCCC) pp 1-6
Yang Z, Hoseinzadeh M, Andrews A, Mayers C, Evans T, Bolt T, Swanson S (2017) AutoTiering: automatic data placement manager in multi-tier all-flash datacenter. In: IEEE 36th International Performance Computing and Communications Conference (IPCCC)
Zhang J, Ho T (2006) Efficient video authentication for H.264/AVC. In: first International Conference on Innovative Computing, Information and Control (ICICIC) pp 46–49
Zhang J, Ho T, Qiu G, Marziliano P (2007) Robust video watermarking of H.264/AVC. IEEE Trans Circuits Syst II: Express Briefs 54(2):205–209
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
El-Shafai, W., El-Rabaie, ES.M., El-Halawany, M. et al. Efficient multi-level security for robust 3D color-plus-depth HEVC. Multimed Tools Appl 77, 30911–30937 (2018). https://doi.org/10.1007/s11042-018-6036-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6036-z