Abstract
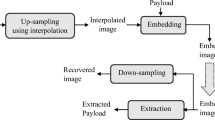
Data hiding in multimedia objects such as text, images, audio and video clips is a technique that has been widely used to achieve security for applications requiring copyright protection, covert communication, and tampering detection. Data hiding can be irreversible or reversible, where the latter is used to ensure exact recovery of the media object after extracting the hidden data. Different approaches to achieve reversible data hiding have been proposed. One of the approaches is the interpolation-based data hiding which has been proposed to achieve high data hiding capacity. This paper presents a new computationally simple interpolation-based data hiding technique that increases data hiding capacity and limits the cover image distortion that is caused by the two major steps of interpolation-based techniques; the downscaling/expansion step and the data hiding step . Image distortion reduction in the downscaling/expansion step is achieved by using a new image interpolation algorithm, whereas the image distortion in the data hiding step is reduced utilizing a new adjustable data hiding algorithm, which adaptively adjusts the level of tradeoff between data hiding capacity and image quality. The performance of the proposed technique has been evaluated for data hiding capacity and image quality using three metrics: peak signal to noise ratio (PSNR), weighted PSNR (WPSNR), and structural similarity index (SSIM). The data hiding capacity achieved by the proposed technique can be as high as 1.7bpp, which is higher by 8.5 to 72% as compared to similar techniques. Moreover, for the data hiding step, the proposed algorithm achieved high quality images as reflected by values up to 54 dB for PSNR, 78 dB for WPSNR, and 0.9998 for SSIM.








Similar content being viewed by others
References
Adi P, Astuti Y, Subhiyakto E (2017) Feature image watermarking based on Bicubic interpolation of wavelet coefficients using CRT. Communication and Information Technology 11:93–99
Alsmirat M, Jararweh Y, Al-Ayyoub M, Shehab M, Gupta B (2016) Accelerating compute intensive medical imaging segmentation algorithms using hybrid CPU-GPU implementations. Multimedia Tools and Applications 76:3537–3555
Atawneh S, Almomani M, Al-Bazar H, Sumari P, Gupta B (2016) Secure and imperceptible digital image steganographic algorithm based on diamond encoding in DWT domain. Multimedia tools and applications. Multimedia Tools and Applications 76:18451–18472
Atawneh S, Almomani A, Al-Bazar H, Sumari P, Gupta B (2017) Homomorphic encryption as a Service for Outsourced Images in mobile cloud computing environment. International Journal of Cloud Applications and Computing 7:27–40
Chauhan D, Singh AK, Kumar B, Saini J (2017) Quantization based multiple medical information watermarking for secure e-health. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-017-4886-4
Chen M, Chen Z, Zeng X and Xiong Z (2009) Reversible data hiding using additive prediction error expansion. Proceedings of the 11th ACM workshop on Multimedia and security, September 7–8, 2009, Princeton, New Jersey, USA, pp 19–24
Coatrieux G, Pan W, Cuppens-Boulahia N, Cuppens F, Roux C (2013) Reversible watermarking based on invariant image classification and dynamic histogram shifting. IEEE Transactions on Information Forensics and Security 8:111–118
Coltuc D (2011) Improved embedding for prediction-based reversible watermarking. IEEE Transactions on Information Forensics and Security 6:873–882
Franco-Contreras J, Coatrieux G, Cuppens F, Cuppens-Boulahia N, Roux C (2014) Robust lossless watermarking of relational databases based on circular histogram modulation. IEEE Transactions on Information Forensics and Security 9:397–410
Gupta S, Gupta B (2016) XSS-secure as a service for the platforms of online social network-based multimedia web applications in cloud. Multimedia Tools and Applications 77:4829–4861
Gupta B, Agrawal D and Yamaguchi S (2016) Handbook of research on modern cryptographic solutions for computer and cyber security. IGI Global
Hong W, Chen TS, Shiu CW (2009) Reversible data hiding for high quality images using modification of prediction errors. J Syst Softw 82:1833–1842
Hong W, Chen TS, Lin KY, Chiang WC (2010) A modified histogram shifting based reversible data-hiding scheme for high quality images. Asian Network for Scientific Information, Information Technology Journal 9:179–183
Hong W, Chen TS, Chang YP, Shiu CW (2010) A high capacity reversible data hiding scheme using orthogonal projection and prediction error modification. Signal Process 90:2911–2922
Hong W, Chen TS, Wu HY (2012) An improved reversible data-hiding in encrypted images using side match. IEEE Signal Processing Letters 19:199–202
Hu J, Li T (2015) Reversible steganography using extended image interpolation technique. Computers & Electrical Engineering 46:447–455
Huang LC, Tseng LY, Hwang MS (2013) A reversible data-hiding method by histogram shifting in high quality medical images. J Syst Softw 86:716–727
Jana B (2016) High payload reversible data hiding scheme using weighted matrix. Optik - International Journal for Light and Electron Optics 127:3347–3358
Jararweh Y, Al-Ayyoub M, Fakirah M, Alawneh L, Gupta B (2017) Improving the performance of the needleman-wunsch algorithm using parallelization and vectorization techniques. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-017-5092-0
Jung KH (2017) A survey of interpolation-based reversible data hiding methods. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-017-4622-0
Jung KH, Yoo KY (2009) Data-hiding method using image interpolation. Computer Standards & Interfaces 31:465–470
Jung KH, Yoo KY (2015) Steganographic method based on interpolation and LSB substitution of digital images. Multimedia Tools and Applications 74:2143–2155
Kim H, Sachnev V, Shi Y, Nam J, Choo HG (2008) A novel difference expansion transform for reversible data embedding. IEEE Transactions on Information Forensics and Security 3:456–465
Kumar M, Agrawal S (2016) Reversible data hiding based on prediction error expansion using adjacent pixels. Security Comm Networks 9:3703–3712
Kumar C, Singh AK, Kumar P (2018) A recent survey on image watermarking techniques and its application in e-governance. Multimedia Tools and Applications 77:3597–3622
Li X, Yang B, Zeng T (2011) Efficient reversible watermarking based on adaptive prediction-error expansion and pixel selection. IEEE Trans Image Process 20:3524–3532
Li J et al (2014) Secure deduplication with efficient and reliable convergent key management. IEEE Transactions on Parallel and Distributed Systems 25:1615–1625
Li J, Chen X, Huang X, Tang S, Xiang Y, Hassan M, Alelaiw A (2015) Secure distributed deduplication systems with improved reliability. IEEE Trans Comput 64:3569–3579
Liu L, Chen T, Zhu S, Hong W, Si X (2014) Data-hiding method using improved neighbor mean interpolation and random-block division. Inf Technol J 13:2374–2384
Liu L, Chen T, Zhu S, Hong W, Si X (2014) A reversible data hiding method using improved neighbor mean interpolation and random-block division. Inf Technol J 13:2374–2384
Lu TC (2017) An interpolation-based lossless hiding scheme based on message recoding mechanism. Optik - International Journal for Light and Electron 130:1377–1396
Lu TC, Lin MC, Huang CH, Deng KM (2016) Reversible data hiding based on image interpolation with a secret message reduction strategy. International Journal of Computer & Software Engineering 1:102–111
Luo L, Chen Z, Chen M, Zeng X, Xiong Z (2010) Reversible image watermarking using interpolation technique. IEEE Transactions on Information Forensics and Security 5:187–193
Ma K et al (2013) Reversible data-hiding in encrypted images by reserving room before encryption. IEEE Transactions on Information Forensics and Security 8:553–562
Niels P, Peter H (2003) Hide and Seek: an introduction to steganography. IEEE Security & Privacy 99:32–44
Raj P et al (2014) A survey on reversible data-hiding in encrypted images. International Journal of Computer Science and Information Technologies 5:7748–7751
Rudder A, Goodridge W, Mohammed S (2013) Using Bias optimization for reversible data hiding using image interpolation. International Journal of Network Security & Its Applications 5:65–76
Sabeen PV, Sajila MK, Bindiya MV (2016) A two stage data hiding scheme with high capacity based on interpolation and difference expansion. Procedia Technology 24:1311–1316
Sachnev V, Kim H, Nam J, Suresh S, Shi Y (2009) Reversible watermarking algorithm using sorting and prediction. IEEE Transactions on Circuits and Systems for Video Technology 19:989–999
Sanglikar H et al (2015) Reversible data-hiding in encrypted images by reserving room before encryption technique and LSB matching algorithm. International Journal of Technical Research and Applications 3:52–54
Singh A, Kumar B, Singh G, Mohan A (2017) Medical image watermarking: techniques and applications, book series on multimedia systems and applications. Springer, USA
Singh AK, Kumar B, Singh S, Ghrera S, Mohand A (2018) Multiple watermarking technique for securing online social network contents using back propagation neural network. Futur Gener Comput Syst 86:926–939
Srivastava R, Kumar B, Singh AK, Mohan A (2017) Computationally efficient joint imperceptible image watermarking and JPEG compression. A green computing approach. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-017-5214-8
Subburam S, Selvakumar S, Geetha S (2017) High performance reversible data hiding scheme through multilevel histogram modification in lifting integer wavelet transform. Multimedia Tools Applications. https://doi.org/10.1007/s11042-017-4622-0
Tsai P, Hu CH, Yeh HL (2009) Reversible image hiding scheme using predictive coding and histogram shifting. Signal Process 89:1129–1143
Tseng HW, Hsieh CP (2009) Prediction based reversible data hiding. Inf Sci 179:2460–2469
Vidya H and A. Neela A (2013) Improving security in digital images through watermarking using enhanced histogram modification. Springer, Advances in Intelligent Systems and Computing 177:175–180
Wang XT, Chang CC, Nguyen TS, Li MC (2013) Reversible data hiding for high quality images exploiting interpolation and direction order mechanism. Digital Signal Processing 23:569–577
Wang XT, Chang CH, Nguyen TS, Li MC (2013) Multi-cloud data management using Shamir's secret sharing and quantum byzantine agreement schemes. International Journal of Cloud Applications and Computing 5:35–52
Yang CH, Hsu CH (2009) A high quality reversible data-hiding method using interpolation technique. Fifth International Conference on Information Assurance and Security, China, pp 603–606
Zear A, Singh AK, Kumar P (2018) A proposed secure multiple watermarking technique based on DWT, DCT and SVD for application in medicine. Multimedia Tools and Applications 77:4863–4882
Zhang Z (2012) Separable reversible data hiding in encrypted image. IEEE Transactions on Information Forensics and Security 7:826–832
Zhang L, Wu X (2006) An edge-guided image interpolation algorithm via directional filtering and data fusion. IEEE Trans Image Process 15:2226–2238
Zhang Z, Wu L, Yan Y, Xiao S, Gao S (2017) Adaptive reversible image watermarking algorithm based on DE. KSII Transactions on Internet and Information Systems 11:1761–1784
Zhang Z, Wu L, Yan Y, Xiao S, Sun H (2017) An improved reversible image watermarking algorithm based on difference expansion. International Journal of Distributed Sensor Networks 13:1–15
Zkik K, Orhanou G, El Hajji S (2017) Secure mobile multi cloud architecture for authentication and data storage. International Journal of Cloud Applications and Computing 7:62–76
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps andinstitutional affiliations.
Rights and permissions
About this article
Cite this article
Mohammad, A.A., Al-Haj, A. & Farfoura, M. An improved capacity data hiding technique based on image interpolation. Multimed Tools Appl 78, 7181–7205 (2019). https://doi.org/10.1007/s11042-018-6465-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6465-8