Abstract
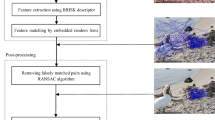
Region duplication or copy–move forgery is an attack in which a region of an image is copied and pasted onto another location of the same image. In the recent state–of–the–art, a number of key–point based methods have been proposed for copy–move forgery detection in digital images. Though the problems of re–scaling and rotation in region duplication, have been sufficiently investigated using key–point based methods, post-processing based attacks such as flip, blur, brightness and noise, remain an open challenge in this field. In this paper, we address the problem of copy–move forgery detection in images, plus aim to identify copied regions, having undergone different geometric (such as rotation, re–scale), and post–processing attacks (such as Gaussian noise, blurring and brightness adjustment). In the proposed algorithm we introduce a region based key–point selection concept, which is considerably more discriminative than single SIFT key–point extraction. In this work, we apply Centroid Linkage Clustering, to identify duplicated regions in an image, from matched key-points. Also, we introduce a Graph Similarity Matching algorithm, to optimize false matches. Our experimental results demonstrate the efficiency of the proposed method in terms of forgery detection and localization efficiency, for a wide range of geometric and post-processing based attacks in region duplication.













Similar content being viewed by others
References
Amerini I, Ballan L, Caldelli R, Del Bimbo A, Serra G (2011) A SIFT-based forensic method for copy–move attack detection and transformation recovery. IEEE Trans Inf Forensics Secur 6(3):1099–1110
Amerini I, Ballan L, Caldelli R, Bimbo AD, Tongo LD, Serra G (2013) Copy-move forgery detection and localization by means of robust clustering with J-Linkage. Signal Process Image Commun 28(6):659–669
Andrea B, Parmiggian F (1996) Single linkage region growing algorithms based on the vector degree of match. IEEE Trans Geosci Remote Sens 34(1):137–148
Ardizzone E, Bruno A, Mazzola G (2015) Copy–move forgery detection by matching triangles of keypoints. IEEE Trans Inf Forensics Secur 10(10):2084–94
Bayram S, Sencar HT, Memon TN (2009) An efficient and robust method for detecting copy–move forgery. In: IEEE international conference on acoustics, speech and signal processing, ICASSP 2009, pp 1053–1056
Blashfield RK (1976) Mixture model tests of cluster analysis: accuracy of four agglomerative hierarchical methods. Psychol Bull 88(3):377
Bo X, Junwen W, Guangjie L, Yuewei D (2010) Image copy-move forgery detection based on SURF. In: International conference on multimedia information networking and security, pp 889–892
Caldelli R, Amerini I, Ballan L, Serra G, Barni M, Costanzo A (2012) On the effectiveness of local warping against SIFT–based copy-move detection. In: Communications control and signal processing (ISCCSP), pp 1–5
Coeurjolly D, Klette R (2004) A comparative evaluation of length estimators of digital curves. IEEE Trans Pattern Anal Mach Intell 26(2):252–258
Danielsson PE (1980) Euclidean distance mapping. Comput Graphics Image Process 3:227–248
Dimitriadou E, Barth M, Windischberger C, Hornik K, Moser E (2004) A quantitative comparison of functional MRI cluster analysis. Artif Intell Med 31(1):57–71
Ding C, He X (2003) Cluster merging and splitting in hierarchical clustering algorithms. In: IEEE international conference on data mining ICDM, pp 139–146
Farid AP, Popescu AC (2004) Exposing digital forgeries by detecting duplicated image region. [Technical Report]. Hanover, Department of Computer Science, Dartmouth College
Fridrich AJ, Soukal BD, Lukáá AJ (2003) Detection of copy–move forgery in digital images. In: Proceedings of digital forensic research workshop
Harris C, Mike S (1988) A combined corner and edge detector. In: Alvey vision conference, vol 15, pp 10–5244
Huang H, Guo W, Zhang Y (2008) Detection of copy-move forgery in digital images using SIFT algorithm. In: Computational intelligence and industrial application, vol 2, pp 272–276
Huang Y, Lu W, Sun W, Long D (2011) Improved DCT–based detection of copy–move forgery in images. Forensic Sci Int 206(1):178–184
Kang X, Wei S (2009) Identifying tampered regions using singular value decomposition in digital image forensics. In: Proceeding of international conference on computer science and software engineering, vol 3, pp 926–930
Kokare M, Biswas PK, Chatterji BN (2005) Texture image retrieval using new rotated complex wavelet filters. IEEE Trans Syst Man Cybern B (Cybern) 35 (6):1168–1178
Lakemond R, Sridharan S, Fookes C (2012) Hessian-based affine adaptation of salient local image features. J Math Imaging Vis 44(2):150–167
Li Y (2013) Image copy-move forgery detection based on polar cosine transform and approximate nearest neighbor searching. Forensic Sci Int 224(1):59–67
Li Z, Yang Y, Zhou X, Lu H (2012) Unsupervised feature selection using nonnegative spectral analysis. In: Proceedings of national conference on association for the advancement of artificial intelligence (AAAI), vol 2, pp 1026–1032
Li J, Li X, Yang B, Sun X (2015) Segmentation–based image copy-move forgery detection scheme. IEEE Trans Inf Forensics Secur 10(3):507–518
Li J, Yang F, Lu W, Sun W (2017) Keypoint-based copy-move detection scheme by adopting MSCRs and improved feature matching. Multimed Tools Appl 76 (20):20483–20497
Li Z, Tang J, He X (2018) Robust structured nonnegative matrix factorization for image representation. IEEE Trans Neural Netw Learn Syst 29(5):1947–1960
Lowe DG (2004) Distinctive image features from scale-invariant keypoints. Int J Comput Vis 60(2):91–110
Mahdian B, Saic S (2007) Detection of copy–move forgery using a method based on blur moment invariants. Forensic Sci Int 172(2):180–189
Manu V T, Babu M (2016) Detection of copy-move forgery in images using segmentation and SURF. In: Advances in signal processing and intelligent recognition systems, pp 645–654
Matas J, Chum O, Urban M, Pajdla T (2004) Robust wide-baseline stereo from maximally stable extremal regions. Image Vis Comput 22(10):761–767
Mikolajczyk K, Tuytelaars T, Schmid C, Zisserman A, Matas J, Schaffalitzky F, Van Gool L (2005) A comparison of affine region detectors. Int J Comput Vis 65(1–2):43–72
Moravec HP (1977) Towards automatic visual obstacle avoidance. In: 5th international joint conference on artificial intelligence, pp 584–594
Muhammad G, Hussain M, Bebisi G (2012) Passive copy–move image forgery detection using undecimated Dyadic wavelet transform. In: Digital investigation
[online]: Available: http://www.dicgim.unipa.it/cvip/
[online]: Image source: http://r0k.us/graphics/kodak/
Pan X, Lyu S (2010) Region duplication detection using image feature matching. IEEE Trans Inf Forensics Secur 5(4):857–67
Punj G, Stewart DW (1983) Cluster analysis in marketing research: review and suggestions for application. J Mark Res 20(2):134–148
Rosten E, Drummond T (2005) Fusing points and lines for high performance tracking. In: Tenth IEEE international conference on computer vision, vol 2, pp 1508–1515
Ryu SJ, Lee MJ, Lee HK (2010) Detection of copy-rotate-move forgery using zernike moments. In: International workshop on information hiding, vol 6. Springer, Berlin, pp 351–364
Sergio B, Nandi AK (2011) Exposing duplicated regions affected by reflection, rotation and scaling. In: Acoustics, speech and signal processing (ICASSP), pp 1880–1883
Shivakumar BL, Baboo S (2011) Detection of region duplication forgery in digital images using SURF. Int J Comput Sci Issues 8(4):199–205
Thajeel SA, Sulong G (2015) A novel approach for detection of copy move forgery using completed robust local binary pattern. J Inf Hiding Multimed Signal Process 6 (2):351–364
Tralic D, Zupancic I, Grgic S, Grgic M (2013) CoMoFoD–new database for copy-move forgery detection. In: 55th international symposium, pp 49–54
Van De Sande K, Gevers T, Snoek C (2010) Evaluating color descriptors for object and scene recognition. IEEE Trans Pattern Anal Mach Intell 32(9):1582–1596
Wang J, Liu G, Li H, Dai Y, Wang Z (2009) Detection of image region duplication forgery using model with circle block. In: Multimedia information networking and security, vol 1, pp 25–29
Wu Z, Ke Q, Isard M, Sun J (2009) Bundling features for large scale partial-duplicate web image search. Proc IEEE Conf Comput Vis Pattern Recognit 22 (10):25–32
Wu Q, Wang S, Zhang X (2011) Log-polar based scheme for revealing duplicated regions in digital images. IEEE Signal Process Lett 18(10):559–562
Xunyu P, Lyu S (2010) Region duplication detection using image feature matching. IEEE Trans Inf Forensics Secur 5(4):857–867
Yang J, Ran P, Tan J (2013) Digital image forgery forensics by using undecimated Dyadic wavelet transform and Zernike moments. J Comput Inf Syst 9 (16):6399–6408
Yang B, Sun X, Guo H, Xia Z, Chen X (2017) A copy-move forgery detection method based on CMFD–SIFT. Multimed Tools Appl 77(1):837–855
Zhang J, Feng Z, Su Y (2008) A new approach for detecting copy–move forgery in digital images. In: 11th IEEE Singapore international conference on communication systems, pp 362–366
Zheng J, Chang L (2014) Detection technology of tampering image based on Harris corner points. J Comput Inf Syst 10:1481–88
Zhu Y, Shen X, Chen H (2016) Copy-move forgery detection based on scaled ORB. Multimed Tools Appl 75(6):3221–3233
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Dixit, R., Naskar, R. Region duplication detection in digital images based on Centroid Linkage Clustering of key–points and graph similarity matching. Multimed Tools Appl 78, 13819–13840 (2019). https://doi.org/10.1007/s11042-018-6666-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6666-1