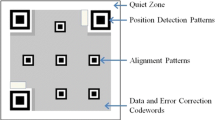
Abstract
QR code is an important means for delivering information which has been widely used in our daily life. As an ISO international standard, the QR code encoding and decoding process are disclosed publicly, thus it is easy to decode a QR code then forge a new QR code with the same QR code public message. It can lead to the problems of information forgery and ease the spreading of fake news. To overcome this weakness, we propose a simple and efficient QR code authentication mechanism to embed the authentication information in the padding region of QR code based on the characteristics of Sudoku and Reed-Solomon code. Different from the previous scheme, the proposed scheme embeds the authentication information without consuming the QR code error correction capacity and is able to achieve a higher embedding capacity. Experimental results show that the proposed scheme has high security, low power consumption and is robust to common QR code attacks.












Similar content being viewed by others
References
Black J, Halevi S, Krawczyk H, Krovetz T, Rogaway P (1999) UMAC: Fast and secure message authentication. In: Annual International Cryptology Conference, Springer, pp 216–233
Chen C (2017) QR code authentication with embedded message authentication code. Mobile Networks and Applications 22(3):383–394
Chen Y-Y, Chi K-Y, Hua K-L (2017) Design of image barcodes for future mobile advertising. EURASIP Journal on Image and Video Processing 2017(1). https://doi.org/10.1186/s13640-016-0158-x
Conde-Lagoa D, Costa-Montenegro E, González-Castaño FJ, Gil-Castiñeira F (2010) Secure eTickets based on QR-Codes with user-encrypted content. In: 2010 Digest of Technical Papers International Conference on Consumer Electronics (ICCE). IEEE, pp 257–258
Cox R (2012) Qart codes. http://research.swtch.com/qart. Accessed Dec 2012
Felgenhauer B, Jarvis F (2003) Sudoku enumeration problems. http://www.afjarvis.staff.shef.ac.uk/sudoku/. Accessed 23 Nov 2017
Inc. D-W (2003) QR code standardization. www.qrcode.com/en/about/standards.html. Accessed 24 Nov 2017
ISO B (2005) IEC 18004: 2006. Information technology Automatic identification and data capture techniques QR Code:126
Jing P, Su Y, Nie L, Bai X, Liu J, Wang M (2018) Low-rank multi-view embedding learning for micro-video popularity prediction. IEEE Trans Knowl Data Eng 30(8):1519–1532
Knuth DE (1985) Dynamic huffman coding. Journal of algorithms 6(2):163–180
Lerner A, Saxena A, Ouimet K, Turley B, Vance A, Kohno T, Roesner F (2015) Analyzing the use of quick response codes in the wild. In: Proceedings of the 13th Annual International Conference on Mobile Systems, Applications, and Services, ACM, pp 359–374
Li L, Wang R-l (2011) A digital watermarking algorithm for QR code. Journal of Hangzhou Dianzi University 31(2):46–49
Li F, Mao Q, Chang C-C (2016) A reversible data hiding scheme based on IWT and the Sudoku method. International Journal of Network Security 18(3):410–419
Liu M, Nie L, Wang X, Tian Q, Chen B (2019) Online data organizer: micro-video categorization by structure-guided multimodal dictionary learning. IEEE Trans Image Process 28(3):1235–1247
Lu J, Yang Z, Li L, Yuan W, Li L, Chang C-C (2017) Multiple schemes for mobile payment authentication using QR code and visual cryptography. Mob Inf Syst 2017(4356038):12. https://doi.org/10.1155/2017/4356038
Mazurczyk W, Caviglione L (2015) Steganography in modern smartphones and mitigation techniques. IEEE Communications Surveys & Tutorials 17(1):334–357
Motahari A, Adjouadi M (2015) Barcode modulation method for data transmission in mobile devices. IEEE Transactions on Multimedia 17(1):118–127
Nazemzadeh P, Fontanelli D, Macii D, Palopoli L (2017) Indoor localization of Mobile robots through QR code detection and dead reckoning data fusion. IEEE/ASME Transactions on Mechatronics 22(6):2588–2599
Pountain D (1987) Run-length encoding. Byte 12(6):317–319
Qian J, Du X, Zhang B, Fan B, Yang X (2017) Optimization of QR code readability in movement state using response surface methodology for implementing continuous chain traceability. Comput Electron Agric 139:56–64
Qin J, Sun R, Xiang X, Li H, Huang H (2016) Anti-fake digital watermarking algorithm based on QR codes and DWT. Journal of the Society for Industrial and Applied Mathematics 18(6):1102–1108
Reed IS, Solomon G (1960) Polynomial codes over certain finite fields. J Soc Ind Appl Math 8(2):300–304
Sun M, Si J, Zhang S (2007) Research on embedding and extracting methods for digital watermarks applied to QR code images. N Z J Agric Res 50(5):861–867
Tkachenko I, Puech W, Destruel C, Strauss O, Gaudin J-M, Guichard C (2016) Two-level QR code for private message sharing and document authentication. IEEE Transactions on Information Forensics and Security 11(3):571–583
Tkachenko I, Puech W, Strauss O, Gaudin J-M, Destruel C, Guichard C (2016) Centrality bias measure for high density QR code module recognition. Signal Process Image Commun 41:46–60
Funding
This study was funded by the NSFC (grant number 61672442 and grand number 61872436), the Fujian NSF (grant number 2016Y0079 and grand number 2016 J01327), the Quanzhou Science and Technology Plan Project (grant number 2017G030).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Huang, PC., Li, YH., Chang, CC. et al. Efficient QR code authentication mechanism based on Sudoku. Multimed Tools Appl 78, 26023–26045 (2019). https://doi.org/10.1007/s11042-019-07795-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-07795-8