Abstract
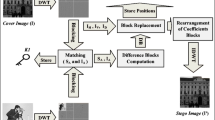
Steganography and steganalysis are the prominent research fields in information hiding paradigm. This work presents a novel framelet transform based image steganography scheme that hides a secret image into cover image. Perfect reconstruction, sparsity, and stability enables framelet transform to be considered as suitable decomposition technique to obtain transform coefficients. The scheme also benefits from bidiagonal singular value decomposition. Secret information is embedded in singular values of framelet coefficients and stego is obtained. A variety of experiments is conducted to judge the efficacy of proposed method. Simulation results prove that stego images possess better visual quality and are robust to several popular image processing operations. Security performance of proposed method is investigated using various steganalysis schemes that include Gabor filter based, wavelet based and contourlet based steganalysis. Detection accuracy is found to be poor in all cases and confirms the undetectability.








Similar content being viewed by others
References
Al-Ataby A, Al-Naima F (2011) A modified high capacity image steganography technique based on wavelet transform. Int Arab J Inf Tech 7(4):358–364
Al Ataby AA, Alnaima FM (2011) High capacity image steganography based on curvelet transform. Developments in E-Systems Engineering. https://doi.org/10.1109/DeSE.2011.13
Al-Taai HN (2008) A novel fast computing method for framelet coefficients. Am J Appl Sci 5(11):1522–1527. ISSN 1546-9239
Anderson RJ, Petitcola FA (1998) On the limits of steganography. IEEE J Sel Area Comm 16:474–481
Banoci V, Bugar G, Levick D (2011) A novel method of image steganography in DWT domain. In: 21st International Conference Radioelektronika (RADIOELEKTRONIKA), pp 1–4. https://doi.org/10.1109/RADIOELEK.2011.5936455
Borraa S, Thankib R, Deyc N, Borisagard K (2018) Secure transmission and integrity verification of color radiological images using fast discrete curvelet transform and compressive sensing. Smart Health Article in Press. https://doi.org/10.1016/j.smhl.2018.02.001
Debnath D, Ghosh E, Gupta Banik B (2019) Multiple RGB Image Steganography Using Arnold and Discrete Cosine Transformation: eHaCON 2018, Kolkata, India. https://doi.org/10.1007/978-981-13-1544-2-13
Denemark T, Fridrich J (2017) Steganography with Multiple JPEG Images of the Same Scene, IEEE Transactions on Information Forensics and Security. https://doi.org/10.1109/TIFS.2017.2705625
Duan X, Song H (2018) Coverless information hiding based on Generative Model. CoRR, vol abs/1802.03528
ElSayed A, Elleithy Ar, Thunga P, Wu Z (2015) Highly secure image steganography algorithm using curvelet transform and DCT encryption. In: IEEE Conference on Systems, Applications and Technology Conference (LISAT). https://doi.org/10.1109/LISAT.2015.7160204
Fakhredanesh M, Rahmati M, Safabakhsh R (2019) Multimed Tools Appl. https://doi.org/10.1007/s11042-019-7238-8
Ghasemi E, Shanbehzadeh J, Fassihi N (2011) High capacity image steganography using wavelet transform and genetic algorithm. In: International Multi Conference of Engineers and Computer Scientists, vol I, March 16-18 Hong Kong
Ghosh E, Debnath D, Gupta Banik B (2019) Blind RGB image steganography using discrete cosine transformation. In: Abraham A, Dutta P, Mandal J, Bhattacharya A, Dutta S (eds) Emerging Technologies in Data Mining and Information Security. Advances in Intelligent Systems and Computing, vol 814. Springer, Singapore
Gulve AK, Joshi MS An Image Steganography Method Hiding Secret Data into Coefficients of Integer Wavelet Transform Using Pixel Value Differencing Approach, Hindawi Mathematical Problems in Engineering vol 2015, Article ID 684824
Hemalatha S, Dinesh AU, Renuka A, Kamath PR (2013) A secure color image steganography in transform domain. International Journal on Cryptography and Information Security 3(1):17–24
Hermassi SM, Rhouma H (2016) A new adaptive image steganography scheme based on DCT and chaotic map. Multimed Tools Appl, pp 1–18. https://doi.org/10.1007/s11042-016-3722-6
Jia R, Shen Z (1994) Multiresolution and wavelets. Proceedings of the Edinburgh Mathematical Society 37:271–300
Kanan HR, Nazeri B (2014) A novel image steganography scheme with high embedding capacity and tunable visual image quality based on a genetic algorithm. Expert Syst Appl 41(14):6123–6130
Ker A (2017) The square root law of steganography: Bringing theory closer to practice. ACM Workshop on Information Hiding and Multimedia Security
Li B, He J, Huang J, Shi YQ (2011) A survey on image steganography and steganalysis. In: International Journal of Information Hiding Multimedia Signal Processing, vol 2, pp 142–172
Li Y., Xiong C., Han X et al (2018) Multimed Tools Appl. https://doi.org/10.1007/s11042-017-5557-1
Lyu S, Farid H (2003) Detecting hidden messages using higher-order statistics and support vector machines. IH2002, LNCS 2578:340–354
Mostafa H, Ali AF, El Taweal G (2015) Hybrid curvelet transform and least significant bit for image steganography. In: IEEE Seventh International Conference on Intelligent Computing and Information Systems (ICICIS), pp 300–305. https://doi.org/10.1109/IntelCIS.2015.7397238
Muhammad N, NargisBibi ZM, Kim DG (2015) Blind data hiding technique using the Fresnelet transform. SpringerPlus. https://doi.org/10.1186/s40064-015-1534-1
Ogiela MR, Koptyra K (2015) False and multi-secret steganography in digital images. Soft Comput 19(11):3331–3339
Rabie T, Baziyad M, Kamel I (2018) . Multimed Tools Appl 77:23673. https://doi.org/10.1007/s11042-018-5713-2
Rabie T, Kamel I (2016) High-capacity steganography: a global-adaptive region discrete cosine transform approach. Multimed Tools Appl, pp 1–21. https://doi.org/10.1007/s11042-016-3301-x
Raftari N, Masoud A, Moghadam E (2012) Digital image steganography based on integer wavelet transform and assignment algorithm. Sixth Asia Modelling Symposium (AMS), pp 87–92. https://doi.org/10.1109/AMS.2012.15
Sajasi S (2015) Amir - Masoud Eftekhari Moghadam. An adaptive image steganographic scheme based on noise visibility function and an optimal chaotic based encryption method. In: Applied Soft Computing, vol. 30, pp 375–389
Sajedi H, Jamzad M (2010) CBS: Contourlet-based steganalysis method. J Signal Process Syst 61:367–373
Shirafkan MH, Akhtarkavan E, Vahidi J (2015) A image steganography scheme based on discrete wavelet transform using lattice vector quantization and reed Solomon encoding. In: 2nd International Conference on Knowledge Based Engineering and Innovation
Simmons G. J. (1983) The prisoner’s problem and the subliminal channel. In: Advances in Cryptology Proceedings of crypto’83, Lecture Notes in Computer Science, pp 51–67
Song XF, Liu F, Yang C, Luo X, Zhang Y (2015) Steganalysis of adaptive JPEG steganography using 2D gabor filters. In: IH & MMSec 15 Proceedings of the 3rd ACM Workshop on Information Hiding and Multimedia Security, Portland, Oregon, pp 15–23
Subhedar MS, Mankar VH Image steganography using redundant discrete wavelet transform and QR factorization, Computers & Electrical Engineering, https://doi.org/10.1016/j.compeleceng.2016.04.017
Subhedar MS, Mankar VH (2014) Current status and key issues in image steganography: A survey. Comput Sci Rev 13-14:95–113
Subramanian M, Korah R (2018) A framework of secured embedding scheme using vector discrete wavelet transformation and lagrange interpolation. Hindawi Journal of Computer Networks and Communications, vol 2018, Article ID 8695103. https://doi.org/10.1155/2018/8695103
Thabit R, Khoo BE (2015) A new robust lossless data hiding scheme and its application to color medical images. In: Digital Signal Processing, vol. 38, pp 77–94
Thanki R, Borra S (2018) A color image steganography in hybrid FRT - DWT domain. Int J Inf Secur Appl 40:92–102
Uma Maheswari S, Jude Hemanth D (2015) Frequency domain QR code based image steganography using Fresnelet transform. AEU International Journal of Electronics and Communications 69(2):539–544
USC-SIPI (1997) http://sipi.usc.edu/database
Xiao M, He Zb (2015) High capacity image steganography method based on framelet and compressive sensing. In: Proc SPIE, Multispectral image acquisition, Processing,and Analysis, vol 9811
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Subhedar, M.S., Mankar, V.H. Secure image steganography using framelet transform and bidiagonal SVD. Multimed Tools Appl 79, 1865–1886 (2020). https://doi.org/10.1007/s11042-019-08221-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08221-9