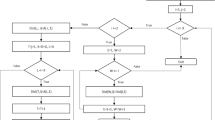
Abstract
The secret sharing scheme is a data security tool that provides reliability and robustness for multi-user authentication systems. This work focus on improving the counting-based secret sharing technique for higher shares security as well as simple and fast computation. The research considers resolving some originally published defects in the shares reconstruction phase by proposing a new distribution model. This distribution model has been optimized practical and efficient. Also, the shares reconstruction model reflects increasing the security of the system by shares authenticity via steganography. We have employed multimedia image-based steganography methods to store the optimized shares that is presenting comparisons for proofed remarks. The paper experimentations tests the work of the enhancements by assuming different secret sharing key sizes of 64-bit, 128-bit, and 256-bit to make sure of practical variations within the security study. The shares usability has been further optimized by testing embedding each generated share using five different techniques of image-based steganography. The results showed a significant attractive impact making the optimized counting-based secret sharing scheme considered a promising solution for multi-user authentication security applications. This optimized system has been analyzed according to the distortion security and capacity parameters showing attractive contributions opening the research direction for further research to come.






















Similar content being viewed by others
References
Abu-Marie W, Gutub A, Abu-Mansour H (2010) Image based steganography using truth table based and determinate Array on RGB Indicator. International Journal of Signal and Image Processing 1(3):196–204
Alaseri K, Gutub A (2018) Merging secret sharing within Arabic text steganography for practical retrieval. International Journal of Research & Development Organisation (IJRDO)-Journal of Computer Science and Engineering 4:1–17
AlAssaf N, AlKazemi B, Gutub A (2017) Applicable light-weight cryptography to secure medical data in IoT systems. Journal of Research in Engineering and Applied Sciences (JREAS) 2(2):50–58
Al-Ghamdi M, Al-Ghamdi M, Gutub A (2018) Security enhancement of shares generation process for multimedia counting-based secret-sharing technique. Multimedia Tools and Applications: An International Journal – Springer, ISSN 1380–7501, DOI: 10.1007/s11042-018-6977-2, Published online: 15 December 2018
Al-Juaid N, Gutub A (2019) Combining RSA and audio steganography on personal computers for enhancing security. SN Applied Sciences - Springer, ISSN: 2523–3963, DOI: 10.1007/s42452-019-0875-8, available online 4 July 2019
Al-Nofaie S, Gutub A, Al-Ghamdi M (2019) Enhancing Arabic Text Steganography for Personal Usage Utilizing Pseudo-Spaces", Journal of King Saud University - Computer and Information Sciences, ISSN: 1319–1578, DOI: 10.1016/j.jksuci.2019.06.010, Published by Elsevier, Available online: 29 June 2019
Alotaibi M, Al-hendi D, Alroithy B, Al-Ghamdi M, Gutub A (2019) Secure Mobile Computing Authentication Utilizing Hash, Cryptography and Steganography Combination. Journal of Information Security and Cybercrimes Research (JISCR), Vol. 2, No. 1, Pages: 9–20, Published by Naif Arab University for Security Sciences (NAUSS)
Al-Otaibi N, Gutub A (2014) 2-Leyer Security System for Hiding Sensitive Text Data on Personal Computers. Lecture Notes on Information Theory, Vol. 2, No. 2, Pages: 151–157, Engineering and Technology Publishing
Al-Qurashi A, Gutub A (2018) Reliable Secret Key Generation for Counting-Based Secret Sharing. Journal of Computer Science & Computational Mathematics 8(4):87–101. https://doi.org/10.20967/jcscm.2018.04.006
Alsmirat MA, Al-Alem F, Al-Ayyoub M, Jararweh Y, Gupta B (2018) Impact of digital fingerprint image quality on the fingerprint recognition accuracy. Multimed Tools Appl:1–40
Arbogast JK, Sumner IB, Lam MO (2018) Parallelizing Shamir’s secret sharing algorithm. J Comput Sci Coll 33(3):12–18
Atawneh S, Almomani A, Al Bazar H, Sumari P, Gupta B (2017) Secure and imperceptible digital image steganographic algorithm based on diamond encoding in DWT domain. Multimed Tools Appl 76(18):18451–18472
Benaloh JC (1986) Secret sharing homomorphisms: keeping shares of a secret. Conference on the Theory and Application of Cryptographic Techniques, Springer, Pages: 251–260
Blakley G (1979) Safeguarding cryptographic keys. International Workshop on Managing Requirements Knowledge
Chang C-C, Chen Y-H, Wang H-C (2011) Meaningful secret sharing technique with authentication and remedy abilities. Inf Sci 181(14):3073–3084
Chang C-C, Hsieh Y-P, Lin C-H (2008) Sharing secrets in stego images with authentication. Pattern Recogn 41(10):3130–3137
Das SK, Dhara BC (2015) A new secret image sharing with arithmetic coding. IEEE International Conference on Research in Computational Intelligence and Communication Networks (ICRCICN), Pages: 395–399
Farooqi N, Gutub A, Khozium MO (2019) Smart Community Challenges: Enabling IoT/M2M Technology Case Study. Life Science Journal, ISSN:1097–8135 16(7)
Gupta BB (2018) Computer and cyber security: principles, algorithm, applications, and perspectives. CRC Press, Boca Raton
Gupta B, Agrawal DP, Yamaguchi S (eds) (2017) Handbook of research on modern cryptographic solutions for computer and cyber security. IGI global, Hershey
Gutub A (2010) Pixel Indicator technique for RGB image steganography. Journal of Emerging Technologies in Web Intelligence (JETWI) 2(1):56–64
Gutub A, Alaseri K (2019) Hiding Shares of Counting-Based Secret Sharing via Arabic Text Steganography for Personal Usage. Arabian Journal for Science and Engineering, ISSN: 2193-567X, DOI: 10.1007/s13369-019-04010-6, available online 4 July 2019
Gutub A, Alaseri K (2019) Refining Arabic Text Stego-Techniques for Shares Memorization of Counting-Based Secret Sharing. Journal of King Saud University - Computer and Information Sciences, ISSN: 1319–1578, DOI: 10.1016/j.jksuci.2019.06.014, Published by Elsevier, Available online: 28 June 2019.
Gutub A, Al-Ghamdi M (2019) Image Based Steganography to Facilitate Improving Counting-Based Secret Sharing. 3D Res 10(1). https://doi.org/10.1007/s13319-019-0216-0
Gutub A, Aljuaid N, Khan E (2019) Counting-based secret sharing technique for multimedia applications. Multimedia Tools and Applications: An International Journal – Springer, ISSN 1380–7501, DOI: 101007/s11042-017-5293-6, Vol. 78, No. 5, Pages: 5591–5619
Gutub A, Al-Qahtani A, Tabakh A (2009) Triple-A: Secure RGB image steganography based on randomization. AICCSA-2009 - The 7thACS/IEEE International Conference on Computer Systems and Applications, Pages: 400–403, Rabat, Morocco
Gutub A, Al-Qurashi A (2019) Secure shares generation via M-blocks partitioning for counting-based secret sharing. Journal Of Engineering Research (JER), ISSN: 2307–1885. Accepted in 14 2019
Gutub A, Ankeer M, Abu-Ghalioun M, Shaheen A, Alvi A (2008) Pixel Indicator high capacity technique for RGB image based steganography. 5th IEEE International Workshop on Signal Processing and its Applications, University of Sharjah, U.A.E
Lin P-Y, Chan C-S (2010) Invertible secret image sharing with steganography. Pattern Recogn Lett 31
Lin C, Tsai W-H (2004) Secret image sharing withsteganography and authentication. J Syst Softw 73(3):405–414
Lin H-C, Yang C-N, Laih C-S, Lin H-T (2013) Natural language letter based visual cryptography scheme. J Vis Commun Image Represent 24(3):318–331
Naor M, Shamir A (1994) Visual cryptography. Workshop on the Theory and Application of Cryptographic Techniques, Springer, Pages: 1–12
Parvez M, Gutub A (2011) Vibrant color image steganography using channel differences and secret data distribution. Kuwait Journal of Science and Engineering (KJSE) 38(1B):127–142
Raphel RK, Ilyas HM, Panicker JR (2015) Multiple secret sharing using natural language letter based visual cryptography scheme. International Conference on Algorithms and Architectures for Parallel Processing, Springer, Pages: 476–486
Shamir A (1979) How to Share a Secret. Commun ACM 22
Shima K, Doi H (2016) (1,3,n) Hierarchical Secret Sharing Scheme Based on XOR Operations for a Small Number of Indispensable Participants. 11th Asia Joint Conference on Information Security (AsiaJCIS), Pages: 108–114
Stoyanova V, Tasheva Z (2015) Research of the characteristics of a steganography algorithm based on LSB method of embedding information in images. Technics. Technologies. Education. Safety
Tewari A, Gupta B (2017) Cryptanalysis of a novel ultra-lightweight mutual authentication protocol for IoT devices using RFID tags. J Supercomput 73(3):1085–1102
Wiese O, Weinhold C, Malchow J, Roth V (2018) I Need this Back, Later! An Exploration of Practical Secret Sharing. Proceedings of the 34th Annual Computer Security Applications Conference (ACSAC), Pages: 478–489
Yang C-N, Chen T-S, Yu KH, Wang C (2007) Improvements of image sharing with steganography andauthentication. J Syst Softw 80(7):1070–1076
Yu C, Li J, Li X, Ren X, Gupta BB (2018) Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimed Tools Appl 77(4):4585–4608
Acknowledgments
Thanks to the master program within the Computer Engineering Department at Umm Al-Qura University (UQU) for motivating this research.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gutub, A., Al-Ghamdi, M. Hiding shares by multimedia image steganography for optimized counting-based secret sharing. Multimed Tools Appl 79, 7951–7985 (2020). https://doi.org/10.1007/s11042-019-08427-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08427-x