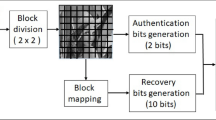
Abstract
The widely available multimedia editing tools and their large reconstruction capabilities make digital multimedia content more sensitive to malicious tampering and manipulations. Therefore, ensuring digital image integrity has become a crucial issue. Watermarking became a popular technique for image authentication. The goal of this paper is to propose a new semi-fragile watermarking scheme for image authentication, localization, and recovery, by using two different watermarks jointly. The embedded information watermark for content recovery is computed from discrete wavelet transform (DWT) approximation coefficients of second level decomposition of the original image and compressed by using Data Representation through Combination (DRC) in order to reduce watermark payload. On another hand, authentication watermark used for both authentication and localization of image tampering is computed by using the block-based watermarking algorithm. Three pseudo-random maps are generated in order to improve the security of the proposed scheme against local attack. Both watermarks are embedded into approximation sub-band of the first wavelet decomposition. Experimental results show that our proposed approach has not only an extremely high accuracy of tampering localization but also a relatively very high recovery rate. Besides, the scheme is able to detect perfectly the difference between malicious attacks and non-malicious attacks such as JPEG compression.













Similar content being viewed by others
References
Boneh D, Shoup V (2015) A graduate course in applied cryptography, version 0.2
Chamlawi R, Khan A, Usman I (2010) Authentication and recovery of images using multiple watermarks. Comput Electr Eng 36(3):578–584
Cheddad A, Condell J, Curran K, Kevitt PM (2010) Digital image steganography: Survey and analysis of current methods. Signal Process 90(3):727–752
Cox IJIJ (2008) Digital watermarking and steganography. Morgan Kaufmann, San Mateo
Di Martino F, Sessa S (2012) Fragile watermarking tamper detection with images compressed by fuzzy transform. Inform Sci 195:62–90
Haouzia A, Noumeir R (2008) Methods for image authentication: a survey. Multimed Tools Appl 39(1):1–46
He HJ, Zhang JS, Tai HM (2009) Self-recovery fragile watermarking using block-neighborhood tampering characterization. Lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics) 5806 LNCS:132–145
He H, Chen F, Tai H, Member S, Kalker T, Zhang J (2012) Performance analysis of a block-neighborhood- based self-recovery fragile watermarking scheme. IEEE Trans Inf Forensics Secur 7(1):185–196
Li C, Wang Y, Ma B, Zhang Z (2011) A novel self-recovery fragile watermarking scheme based on dual-redundant-ring structure q. Comput Electr Eng 37:927–940. [Online]. Available: http://or.nsfc.gov.cn/bitstream/00001903-5/88341/1/1000002175455.pdf
Li C, Wang Y, Ma B, Zhang Z (2012) Tamper detection and self-recovery of biometric images using salient region-based authentication watermarking scheme. Computer Standards and Interfaces 34(4):367–379
Li C, Zhang A, Liu Z, Liao L, Huang D (2015) Semi-fragile self-recoverable watermarking algorithm based on wavelet group quantization and double authentication. Multimed Tools Appl 74(23):10581–10604
Lin C-Y, Chang S-F (2000) Semi-fragile watermarking for authenticating JPEG visual content. In: Proceedings of the SPIE security and watermarking of multimedia contents II, San Jose, pp 140–151
Ling C, Ur-rehman O (2015) Robust image authentication in the presence of noise. Springer, Cham, pp 43–53
Liu C-L (2010) A tutorial of the wavelet transform Chapter 1 Overview 1.1 Introduction
Ouled Zaid A, Makhloufi A, Bouallegue A, Olivier C (2009) Improved QIM-based watermarking integrated to JPEG2000 coding scheme. SIViP 3(3):197–207
Phadikar A, Maity SP, Mandal M (2012) Novel wavelet-based QIM data hiding technique for tamper detection and correction of digital images. J Vis Commun Image Represent 23(3):454–466
Poornima R, Iswarya R (2013) And overview of digital image steganography. International Journal of Computer Science & Engineering Survey 4(1):23–31
Preda RO (2013) Semi-fragile watermarking for image authentication with sensitive tamper localization in the wavelet domain. Measurement 46(1):367–373
Qi X, Xin X (2011) A quantization-based semi-fragile watermarking scheme for image content authentication. J Vis Commun Image Represent 22:187–200
Qi X, Xin X (2015) A singular-value-based semi-fragile watermarking scheme for image content authentication with tamper localization. J Vis Commun Image Represent 30:312–327
Said J, Souissi R, Hamam H (2013) A new representation of image through numbering pixel combinations. Journal of Information Security Research 4:1
Salomon D (2007) Data compression: the complete reference. Springer, Berlin
Salomon D (2008) A concise introduction to data compression, ser. Undergraduate topics in computer science. Springer, London
Sayood K (2006) Introduction to data compression, Third edition (Morgan Kaufmann Series in multimedia information and systems)
Tong X, Liu Y, Zhang M, Chen Y (2013) A novel chaos-based fragile watermarking for image tampering detection and self-recovery. Signal Process Image Commun 28(3):301–308
Tsai T, Wu C, Fang C (2014) Design and Implementation of a joint data compression and digital watermarking system in an MPEG-2 video encoder. J Sign Process Syst 74:203
Ullah R, Khan A, Malik AS (2013) Dual-purpose semi-fragile watermark: Authentication and recovery of digital images. Comput Electr Eng 39 (7):2019–2030. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0045790613001213
Wang H, Ho AT, Zhao X (2012) A novel fast self-restoration semi-fragile watermarking algorithm for image content authentication resistant to JPEG compression. Lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics) 7128 LNCS:72–85
Wang Z, Bovik AC, Sheikh HR, Member S, Simoncelli EP, Member S (2004) Image quality assessment : from error visibility to structural similarity. IEEE Trans Image Process 13(4):1–14
Wu C-M, Shih Y-S (2013) A simple image tamper detection and recovery based on fragile watermark with one parity section and two restoration sections. Optics and Photonics Journal 03(02):103–107
Xiao D, Shih FY (2012) An improved hierarchical fragile watermarking scheme using chaotic sequence sorting and subblock post-processing. Opt Commun 285 (10–11):2596–2606. [Online]. Available: https://www.sciencedirect.com/science/article/abs/pii/S0030401812001368
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Rhayma, H., Makhloufi, A., Hamam, H. et al. Semi-fragile self-recovery watermarking scheme based on data representation through combination. Multimed Tools Appl 78, 14067–14089 (2019). https://doi.org/10.1007/s11042-019-7244-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-7244-x