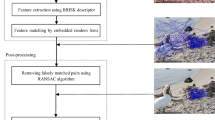
Abstract
Digital image are easy to be tampered by the photo editing software. Therefore, digital image forensics which aims at validating the authenticity of the digital image are received wide public concern. Region duplication is a commonly used operation in digital image forgeries. The main aims of the region duplication are to overemphasize or conceal some contents by duplicating some regions on the image. Most of the region duplication methods can be categorized into two main classes:block-based and keypoint-based methods. In this paper, a novel region duplication detection scheme is proposed based on hybrid feature and evaluative clustering. The proposed scheme is divided into two stages: the rough matching and the exact matching. In the rough matching, first, hybrid keypoints are extracted from the input image, and those keypoints are described by the unified descriptors. Second, those keypoints are matched by the g2NN strategy. Third, those matched keypoints are grouped by the proposed clustering based on evaluation. Fourth, affine transformations are estimated between these groups, and Bag of Word is used to filter inaccuracy affine transformations to improve the results of pixel level. When no affine transformation is obtained, in the exact matching, each suspicious region is handled separately. Experimental results indicate that the proposed scheme outperforms the state-of-the-art methods under various conditions.













Similar content being viewed by others
References
Achanta R, Shaji A, Smith K, Lucchi A, Fua P, Süsstrunk S (2012) Slic superpixels compared to state-of-the-art superpixel methods. IEEE Trans Pattern Anal Mach Intell 34(11):2274–2282
Alcantarilla PF, Bartoli A, Davison AJ (2012) Kaze features. In: European conference on computer Vision (ECCV), 214–227, Florence, Italy
Amerini I, Ballan L, Caldelli R, Bimbo AD, Serra G (2011) A SIFT-based forensic method for copy-move attack detection and transformation recovery. IEEE Trans Inform Forensics Secur 6(3):1099–1110
Amerini I, Ballan L, Caldelli R, Bimbo AD, Tongo LD, Serra G (2013) Copy-move forgery detection and localization by means of robust clustering with j-Linkage. Signal Process Image Commun 28(6):659–669
Ardizzone E, Bruno A, Mazzola G (2015) Copycmove forgery detection by matching triangles of keypoints. IEEE Trans Inform Forensics Secur 10(10):2084–2094
Avidan S, Shamir A (2007) Seam carving for content-aware image resizing. ACM Trans Graph 26(3):10
Barnes C, Shechtman E, Finkelstein A, Dan BG (2009) Patchmatch:a randomized correspondence algorithm for structural image editing. Acm Trans Graph 28(3):1–11
Bashar M, Noda K, Ohnishi N, Mori K (2010) Exploring duplicated regions in natural images. IEEE Trans Image Process PP(99):1–1
Bay H, Ess A, Tuytelaars T, Gool LV (2008) SURF: speeded Up robust features. Comput Vis Image Underst 110(3):346–359
Beis JS, Lowe DG (1997) Shape indexing using approximate nearest-neighbour search in high-dimensional spaces. In: Conference on computer vision and pattern recognition (CVPR), 1000–1006, San Juan, Puerto Rico
Bravo-Solorio S, Nandi AK (2011) Exposing duplicated regions affected by reflection, rotation and scaling. In: IEEE international conference on acoustics, speech and signal processing (ICASSP), 1880–1883, Prague, Czech Republic
Chen J, Lu W, Fang Y, Liu X, Yeung Y, Yingjie X (2018) Binary image steganalysis based on local texture pattern. J Vis Commun Image Represent 55:149–156
Chen J, Lu W, Yeung Y, Xue Y, Liu X, Lin C, Zhang Y (2018) Binary image steganalysis based on distortion level co-occurrence matrix. Comput Mater Continua 55(2):201–211
Chen L, Lu W, Ni J (2012) An image region description method based on step sector statistics and its application in image copy-rotate/flip-move forgery detection. Int J Digital Crime Forensics 4(1):49–62
Chen L, Lu W, Ni J, Sun W, Huang J (2013) Region duplication detection based on harris corner points and step sector statistics. J Vis Commun Image Represent 24(3):244–254
Chen X, Jian W, Wei L, Jiaming X (2018) Multi-gait recognition based on attribute discovery. IEEE Trans Pattern Anal Mach Intell 40(7):1697–1710
Christlein V, Riess C, Angelopoulou E (2010) On rotation invariance in copy-move forgery detection. In: IEEE international workshop on information forensics and security (WIFS), 1-6, Seattle, WA, USA
Christlein V, Riess C, Jordan J, Riess C, Angelopoulou E (2012) An evaluation of popular copy-move forgery detection approaches. IEEE Trans Inform Forensics Secur 7(6):1841–1854
Cozzolino D, Poggi G, Verdoliva L (2015) Copy-move forgery detection based on patchmatch. In: IEEE International conference on image processing, 5312–5316, Quebec City, Canada
Cozzolino D, Poggi G, Verdoliva L (2015) Efficient dense-field copycmove forgery detection. IEEE Trans Inform Forensics Secur 10(11):2284–2297
Farid H (2009) Image forgery detection. Signal Process Magazine IEEE 26 (2):16–25
Farid H (2009) Photo fakery and forensics. Adv Comput 77:1–55
Feng B, Lu W, Sun W (2014) Secure binary image steganography based on minimizing the distortion on the texture. IEEE Trans Inform Forensics Secur 10 (2):243–255
Feng B, Weng J, Lu W, Pei B (2017) Multiple watermarking using multilevel quantization index modulation. In: International workshop on digital watermarking, 312–326, Beijing, China
Feng B, Weng J, Lu W, Pei B (2017) Steganalysis of content-adaptive binary image data hiding. J Vis Commun Image Represent 46:119–127
Ferreira A, Felipussi SC, Alfaro C, Fonseca P, Vargas-Munoz JE, Dos Santos JA, Rocha A (2016) Behavior knowledge space-based fusion for copy-move forgery detection. IEEE Trans Image Process 25(10):4729–4742
Fischler MA, Bolles RC (1981) Random sample consensus: a paradigm for model fitting with applications to image analysis and automated cartography. Commun ACM 24(6):381–395
Forssen PE (2007) Maximally stable colour regions for recognition and matching. In: IEEE Conference on Computer Vision and Pattern Recognition (CVPR), 1–8, Minneapolis, Minnesota, USA
Fridrich J, Soukal D, Lukáš J (2003) Detection of copy-move forgery in digital images. In: Proceeding of digital forensic research workshop, 19-23, Cleveland, OH, USA
Hamdi D, Iqbal F, Baker T, Shah B (2016) Multimedia file signature analysis for smartphone forensics. In: International conference on developments in esystems engineering. Liverpool, UK
Harris CG, Stephens MJ (1988) A combined corner and edge detector. In: Alvey vision conference, 147–151
Hastie T, Tibshirani R, Friedman J (2003) The elements of statistical learning. Springer, Berlin
He Z, Lu W, Sun W, Huang J (2012) Digital image splicing detection based on markov features in dct and dwt domain. Pattern Recogn 45(12):4292–4299
Hsu YN, Arsenault HH, April G (1982) Rotation-invariant digital pattern recognition using circular harmonic expansion. Appl Opt 21(22):4012–4015
Huang Y, Lu W, Sun W, Long D (2011) Improved DCT-based detection of copy-move forgery in images. Forensic Sci Int 206(1-3):178–184
Jin G, Wan X (2017) An improved method for sift-based copycmove forgery detection using non-maximum value suppression and optimized j-Linkage. Signal Process Image Commun 57:113–125
Lai Y, Huang T, Jing L, Lu H (2018) An improved block-based matching algorithm of copy-move forgery detection. Multimed Tool Appl 77(12):15,093–15,110
Li J, Li X, Yang B, Sun X (2015) Segmentation-based image copy-move forgery detection scheme. IEEE Trans Inform Forensics Secur 10(3):507–518
Li J, Lu W (2016) Blind image motion deblurring with L0-regularized priors. J Vis Commun Image Represent 40:14–23
Li J, Lu W, Weng J, Mao Y, Li G (2018) Double jpeg compression detection based on block statistics. Multimed Tool and Appl 77(24):31,895–31,910
Li J, Yang F, Lu W, Sun W (2016) Keypoint-based copy-move detection scheme by adopting mscrs and improved feature matching. Multimed Tool Appl 76 (20):1–15
Li Y (2013) Image copy-move forgery detection based on polar cosine transform and approximate nearest neighbor searching. Forensic Sci Int 224(1-3):59
Li Y, Zhou J (2018) Fast and effective image copy-move forgery detection via hierarchical feature point matching. IEEE Trans Inform Forensics Secur PP(99):1–1
Lin C, Lu W, Huang X, Liu K, Sun W, Lin H, Tan Z (2018) Copy-move forgery detection using combined features and transitive matching, Multimed Tool Appl, pp 1–16. https://doi.org/10.1007/s11042-018-6922-4
Lin C, Lu W, Sun W, Zeng J, Xu T, Lai JH (2018) Region duplication detection based on image segmentation and keypoint contexts. Multimed Tool Appl 77 (11):14,241–14,258
Liu G, Wang J, Lian S, Wang Z (2011) A passive image authentication scheme for detecting region-duplication forgery with rotation. J Netw Comput Appl 34 (5):1557–1565
Liu X, Lu W, Huang T, Liu H, Xue Y, Yuileong Y (2018) Scaling factor estimation on jpeg compressed images by cyclostationarity analysis, Multimed Tool Appl, pp 1–18. https://doi.org/10.1007/s11042-018-6411-9
Liu X, Lu W, Zhang Q, Huang J, Shi YQ (2019) Downscaling factor estimation on pre-jpeg compressed images, IEEE Trans Circuit Syst Video Technol, pp 1–1. https://doi.org/10.1109/TCSVT.2019.2893353
Lowe DG (2004) Distinctive image features from scale-invariant keypoints. Int J Comput Vis 60(2):91–110
Lu W, He L, Yeung Y, Xue Y, Liu H, Feng B (2019) Secure binary image steganography based on fused distortion measurement. IEEE Trans Circuit Syst Video Technol PP(99):1–1
Lu W, Sun W, Chung FL, Lu H (2011) Revealing digital fakery using multiresolution decomposition and higher order statistics. Eng Appl Artif Intell 24 (4):666–672
Luo X, Song X, Li X, Zhang W, Lu J, Yang C, Liu F (2016) Steganalysis of hugo steganography based on parameter recognition of syndrome-trellis-codes. Multimed Tool Appl 75(21):13,557– 13,583
Ma Y, Luo X, Li X, Bao Z, Yi Z (2018) Selection of rich model steganalysis features based on decision rough set α-positive region reduction. IEEE Trans Circuit Syst Video Technol PP(99):1–1
Macdermott A, Baker T, Shi Q (2018) Iot forensics: challenges for the ioa era. In: 9th IFIP international conference on new technologies, mobility and security (NTMS), Paris, France
Mahdian B, Saic S (2007) Detection of copy-move forgery using a method based on blur moment invariants. Forensic Sci Int 171:180–189
Mclachlan GJ, Krishnan T (1997) The em algorithm and extensions. Biometrics 382(1):154–156
Mikolajczyk K, Schmid C (2002) Indexing based on scale invariant interest points. In: IEEE International Conference on Computer Vision (ICCV), 525–531, Vancouver, BC, Canada
Mikolajczyk K, Schmid C (2004) Scale and affine invariant interest point detectors. Int J Comput Vis 60(1):63–86
Mikolajczyk K, Schmid C (2005) A performance evaluation of local descriptors. IEEE Trans Pattern Anal Mach Intell 27(10):1615–1630
Muhammad K, Ahmad J, Farman H, Jan Z, Sajjad M, Baik SW (2015) A secure method for color image steganography using gray-level modification and multi-level encryption. Ksii Trans Internet Inform Syst 9(5):1938–1962
Muhammad K, Ahmad J, Rehman NU, Jan Z, Sajjad M (2017) Cisska-lsb: color image steganography using stego key-directed adaptive lsb substitution method. Multimed Tool Appl 76(6):8597– 8626
Muhammad K, Sajjad M, Baik SW (2016) Dual-level security based cyclic18 steganographic method and its application for secure transmission of keyframes during wireless capsule endoscopy. J Med Syst 40(5):1–16
Muhammad K, Sajjad M, Mehmood I, Rho S, Baik SW (2016) Image steganography using uncorrelated color space and its application for security of visual contents in online social networks. Futur Gener Comput Syst 86:951–960
Muhammad K, Sajjad M, Mehmood I, Rho S, Baik SW (2016) A novel magic lsb substitution method (m-lsb-sm) using multi-level encryption and achromatic component of an image. Multimed Tool Appl 75(22):14,867–14,893
Pan X, Lyu S (2010) Region duplication detection using image feature matching. IEEE Trans Inform Forensics Secur 5(4):857–867
Pun CM, Yuan XC, Bi XL (2015) Image forgery detection using adaptive over-segmentation and feature points matching. IEEE Trans Inform Forensics Secur 10 (8):1705–1716
Redi JA, Taktak W, Dugelay JL (2011) Digital image forensics: a booklet for beginners. Multimed Tool Appl 51(1):133–162
Rubinstein M, Shamir A, Avidan S (2008) Improved seam carving for video retargeting. ACM Trans Graph 27(3):1–9
Ryu SJ, Kirchner M, Lee MJ, Lee HK (2013) Rotation invariant localization of duplicated image regions based on Zernike moments. IEEE Trans Inform Forensics Secur 8(8):1355–1370
Ryu SJ, Lee MJ, Lee HK (2010) Detection of copy-rotate-move forgery using Zernike moments. In: IEEE International workshop on Information Hiding (IH). Springer, Berlin, pp 51–65
Sencar HT, Memon N (2008) Overview of State-of-the-Art in Digital Image Forensics. Algorithms, Architectures And Information Systems Security
Sharif SA, Ali MA, Reqabi NA, Iqbal F, Baker T, Marrington A (2016) Magec: an image searching tool for detecting forged images in forensic investigation. In: 8th IFIP international conference on new technologies, mobility and security (NTMS), 1–6, Larnaca, Cyprus
Shivakumar BL, Baboo S (2011) Detection of region duplication forgery in digital images using SURF. Int J Comput Sci Issues 8(4):199–205
Silva E, Carvalho T, Ferreira A, Rocha A (2015) Going deeper into copy-move forgery detection: exploring image telltales via multi-scale analysis and voting processes. J Vis Commun Image Represent 29(C):16–32
Soni B, Das PK, Thounaojam DM (2018) Keypoints based enhanced multiple copy-move forgeries detection system using density-based spatial clustering of application with noise clustering algorithm. IET Image Process 12(11):2092–2099
Stamm MC, Min W, Liu KJR (2013) Information forensics: an overview of the first decade. IEEE Access 1:167–200
Teague MR (1980) Image analysis via the general theory of moments. J Opt Soc Am 70(8):920–930
Toldo R, Fusiello A (2008) Robust multiple structures estimation with j-Linkage. In: European conference on computer vision (ECCV), 537–547, Marseille, France
Warif NBA, Wahab AWA, Idris MYI, Salleh R, Othman F (2017) Sift-symmetry: a robust detection method for copy-move forgery with reflection attack. J Vis Commun Image Represent 46:219– 232
Xin L, Guo S, Yin J, Wang H, Xiong L, Sangaiah AK (2017) New cubic reference table based image steganography. Multimed Tool Appl 77(4):1–18
Xin L, Li K, Yin J (2016) Separable data hiding in encrypted image based on compressive sensing and discrete fourier transform. Multimed Tool Appl 76(20):1–15
Xin L, Zheng Q, Ding L (2017) Data embedding in digital images using critical functions. Signal Process Image Commun 58:146–156
Xu B, Wang J, Liu G, Dai Y (2010) Image copy-move forgery detection based on SURF. In: International conference on multimedia information networking and security (MINES), 889–892, Nanjing, China
Xue F, Ye Z, Lu W, Liu H, Li B (2017) Mse period based estimation of first quantization step in double compressed jpeg images. Signal Process Image Commun 57:76–83
Yang F, Li J, Lu W, Weng J (2017) Copy-move forgery detection based on hybrid features. Eng Appl Artif Intell 59:73–83
Yang H, Niu Y, Jiao L, Liu Y, Wang XY, Zhou Z (2018) Robust copy-move forgery detection based on multi-granularity superpixels matching. Multimed Tool Appl 77(11):13,615–13,641
Yap PT, Jiang X, Kot AC (2010) Two-dimensional polar harmonic transforms for invariant image representation. IEEE Trans Pattern Anal Mach Intell 32(7):1259–70
Yi Z, Qin C, Zhang W, Liu F, Luo X (2018) On the fault-tolerant performance for a class of robust image steganography. Signal Process 146:99–111
Zhang F, Lu W, Liu H, Xue F (2018) Natural image deblurring based on L0-regularization and kernel shape optimization. Multimed Tool Appl 77 (20):26,239–26,257
Zhang Q, Lu W, Wang R, Li G (2018) Digital image splicing detection based on markov features in block dwt domain. Multimed Tool Appl 77(23):31,239–312,601
Zhang Q, Lu W, Weng J (2016) Joint image splicing detection in dct and contourlet transform domain. J Vis Commun Image Represent 40:449–458
Zhu Y, Shen X, Chen H (2016) Copy-move forgery detection based on scaled orb. Multimed Tool Appl 75(6):3221–3233
Acknowledgements
This work is supported by the National Natural Science Foundation of China (No. U1736118), the National Key R&D Program of China (No. 2017YFB0802500), the Natural Science Foundation of Guangdong (No. 2016A030313350), the Special Funds for Science and Technology Development of Guangdong (No. 2016KZ010103), the Key Project of Scientific Research Plan of Guangzhou (No. 201804020068), the Fundamental Research Funds for the Central Universities (No. 16lgjc83 and No. 17lgjc45), the Science and Technology Planning Project of Guangdong Province (No.2017A040405051), the Alibaba Group through Alibaba Innovative Research Program.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Lin, C., Lu, W., Huang, X. et al. Region duplication detection based on hybrid feature and evaluative clustering. Multimed Tools Appl 78, 20739–20763 (2019). https://doi.org/10.1007/s11042-019-7342-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-7342-9