Abstract
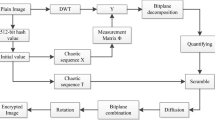
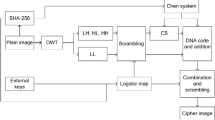
This paper presents a novel image compression-encryption scheme, which has the compression-confusion-diffusion Structure. Firstly, based on Chebyshev chaotic map, a Gauss measurement matrix is constructed and optimized, which is applied to compressive sensing. Then, an image compression-encryption algorithm is proposed by using a six-dimensional discrete chaotic map. In the proposed scheme, the original image is transformed into a sparse coefficient matrix by discrete wavelet transform, and the sparse coefficients are measured by using the optimized Gauss measurement matrix to get the measured values. Then, the measured values are quantized into integer values and the compressed image is obtained. Furtherly, the compressed image is encrypted by using a six-dimensional chaotic map. In the process of encryption, the plaintext image is divided into two parts, when encrypting the second part, the first part is used as part of the key. While encrypting the first part, the ciphertext of the second part is used as part of the key. Thus, the algorithm has strong confusion and diffusion effect and makes ciphertext sensitive to plaintext. Experimental results such as effects of compression-encryption, key space analysis, key sensitivity analysis, differential analysis, histograms analysis, information entropy analysis, and correlation coefficients analysis show that the proposed scheme is secure and has high application potential.







Similar content being viewed by others
References
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurcation Chaos 16(8):2129–2151. https://doi.org/10.1142/s0218127406015970
Belazi A, El-Latif AAA (2017) A simple yet efficient S-box method based on chaotic sine map. Optik 130:1438–1444. https://doi.org/10.1016/j.ijleo.2016.11.152
Candes EJ, Tao T (2006) Near-optimal signal recovery from random projections: universal encoding strategies? IEEE Trans Inf Theory 52(12):5406–5425. https://doi.org/10.1109/tit.2006.885507
Candes EJ, Romberg J, Tao T (2006) Robust uncertainty principles: exact signal reconstruction from highly incomplete frequency information. IEEE Trans Inf Theory 52(2):489–509. https://doi.org/10.1109/tit.2005.862083
Chai X, Fu X, Gan Z, Lu Y, Chen Y (2019) A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process 155:44–62. https://doi.org/10.1016/j.sigpro.2018.09.029
Chai X, Wu H, Gan Z, Zhang Y, Chen Y, Nixon KW (2020) An efficient visually meaningful image compression and encryption scheme based on compressive sensing and dynamic LSB embedding. Opt Lasers Eng 124:105837. https://doi.org/10.1016/j.optlaseng.2019.105837
Chen GR, Mao YB, Chui CK (2004) A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos Solitons Fractals 21(3):749–761. https://doi.org/10.1016/j.chaos.2003.12.022
Deng J, Zhao S, Wang Y, Wang L, Wang H, Sha H (2017) Image compression-encryption scheme combining 2D compressive sensing with discrete fractional random transform. Multimed Tools Appl 76(7):10097–10117. https://doi.org/10.1007/s11042-016-3600-2
Donoho DL (2006) Compressed sensing. IEEE Trans Inf Theory 52(4):1289–1306. https://doi.org/10.1109/tit.2006.871582
Fridrich J (1998) Symmetric ciphers based on two-dimensional chaotic maps. Int J Bifurcation Chaos 8(6):1259–1284
Gong L, Qiu K, Deng C, Zhou N (2019) An image compression and encryption algorithm based on chaotic system and compressive sensing. Opt Laser Technol 115:257–267. https://doi.org/10.1016/j.optlastec.2019.01.039
Hua ZY, Zhou YC (2018) One-dimensional nonlinear model for producing Chaos. IEEE Transactions on Circuits and Systems I-Regular Papers 65(1):235–246. https://doi.org/10.1109/tcsi.2017.2717943
Li J, Huang XY, Li JW, Chen XF, Xiang Y (2014) Securely outsourcing attribute-based encryption with Checkability. IEEE Transactions on Parallel and Distributed Systems 25(8):2201–2210. https://doi.org/10.1109/tpds.2013.271
Li J, Li YK, Chen XF, Lee PPC, Lou WJ (2015) A hybrid cloud approach for secure authorized Deduplication. IEEE Transactions on Parallel and Distributed Systems 26(5):1206–1216. https://doi.org/10.1109/tpds.2014.2318320
Li C, Zhang Y, Xie EY (2019) When an attacker meets a cipher-image in 2018: a year in review. Journal of Information Security and Applications 48:1–9. https://doi.org/10.1016/j.jisa.2019.102361
Lian SG, Sun JS, Wang ZQ (2005) A block cipher based on a suitable use of the chaotic standard map. Chaos Solitons Fractals 26(1):117–129. https://doi.org/10.1016/j.chaos.2004.11.096
Lu Q, Zhu C, Wang G (2019) A novel S-box design algorithm based on a new compound chaotic system. Entropy 21(10). https://doi.org/10.3390/e21101004
Lu Q, Zhu C, Deng X (2020) An efficient image encryption scheme based on the LSS chaotic map and single S-box. IEEE Access 8(1):25664–25678. https://doi.org/10.1109/access.2020.2970806
Orsdemir A, Altun HO, Sharma G, Bocko MF (2008) On the security and robustness of encryption via compressed sensing. In: 2008 IEEE military communications conference: Milcom 2008, vols 1-7. IEEE Military Communications Conference. IEEE, pp 1040–1046
Peng Y, He Y (2012) A reconstruction algorithm for compressed sensing noise signal. Journal of Computational Information Systems 8(14):6025–6031
Rachlin Y, Baron D (2008) The secrecy of compressed sensing measurements. Paper presented at the 2008 46th annual Allerton conference on communication, control, and computing, vols 1–3. IEEE
Rehman AU, Khan JS, Ahmad J, Hwang SO (2016) A new image encryption scheme based on dynamic S-boxes and chaotic maps. 3D Research 7(1):UNSP 7. https://doi.org/10.1007/s13319-016-0084-9
Ren Y-M, Zhang Y-N, Li Y (2014) Advances and perspective on compressed sensing and application on image processing. Acta Automat Sin 40(8):1563–1575
Wang X, Teng L, Qin X (2012) A novel colour image encryption algorithm based on chaos. Signal Process 92(4):1101–1108. https://doi.org/10.1016/j.sigpro.2011.10.023
Wong KW, Kwok BSH, Law WS (2008) A fast image encryption scheme based on chaotic standard map. Phys Lett A 372(15):2645–2652. https://doi.org/10.1016/j.physleta.2007.12.026
Xiao D, Wang L, Xiang T, Wang Y (2017) Multi-focus image fusion and robust encryption algorithm based on compressive sensing. Opt Laser Technol 91:212–225. https://doi.org/10.1016/j.optlastec.2016.12.024
Xu L, Gou X, Li Z, Li J (2017) A novel chaotic image encryption algorithm using block scrambling and dynamic index based diffusion. Opt Lasers Eng 91:41–52. https://doi.org/10.1016/j.optlaseng.2016.10.012
Xu Q, Sun K, Cao C, Zhu C (2019) A fast image encryption algorithm based on compressive sensing and hyperchaotic map. Opt Lasers Eng 121:203–214. https://doi.org/10.1016/j.optlaseng.2019.04.011
Zhang LY, Wong K-W, Zhang Y, Zhou J (2016) Bi-level protected compressive sampling. IEEE Transactions on Multimedia 18(9):1720–1732. https://doi.org/10.1109/tmm.2016.2581593
Zhou NR, Zhang AD, Zheng F, Gong LH (2014) Novel image compression-encryption hybrid algorithm based on key-controlled measurement matrix in compressive sensing. Opt Laser Technol 62:152–160. https://doi.org/10.1016/j.optlastec.2014.02.015
Zhou N, Yang J, Tan C, Pan S, Zhou Z (2015) Double-image encryption scheme combining DWT-based compressive sensing with discrete fractional random transform. Opt Commun 354:112–121. https://doi.org/10.1016/j.optcom.2015.05.043
Zhu C (2012) A novel image encryption scheme based on improved hyperchaotic sequences. Opt Commun 285(1):29–37. https://doi.org/10.1016/j.optcom.2011.08.079
Zhu C, Sun K (2018) Cryptanalyzing and improving a novel color image encryption algorithm using RT-enhanced chaotic tent maps. IEEE Access 6:18759–18770. https://doi.org/10.1109/access.2018.2817600
Zhu S, Zhu C (2018) Image encryption algorithm with an avalanche effect based on a six-dimensional discrete chaotic system. Multimed Tools Appl 77(21):29119–29142. https://doi.org/10.1007/s11042-018-6078-2
Zhu S, Zhu C (2019) Plaintext-related image encryption algorithm based on block structure and five-dimensional chaotic map. IEEE Access 7:147106–147118. https://doi.org/10.1109/access.2019.2946208
Zhu S, Zhu C (2019) A new image compression-encryption scheme based on compressive sensing and cyclic shift. Multimed Tools Appl 78(15):20855–20875. https://doi.org/10.1007/s11042-019-7405-y
Zhu S, Zhu C, Wang W (2018) A novel image compression-encryption scheme based on Chaos and compression sensing. IEEE Access 6:67095–67107. https://doi.org/10.1109/access.2018.2874336
Zhu C, Wang G, Sun K (2018) Improved cryptanalysis and enhancements of an image encryption scheme using combined 1D chaotic maps. Entropy 20(11):843. https://doi.org/10.3390/e20110843
Zhu CX, Wang GJ, Sun KH (2018) Cryptanalysis and improvement on an image encryption algorithm design using a novel Chaos based S-box. Symmetry 10(9):399. https://doi.org/10.3390/sym10090399
Zhu S, Wang G, Zhu C (2019) A secure and fast image encryption scheme based on double chaotic S-boxes. Entropy 21(8):790. https://doi.org/10.3390/e21080790
Zhu S, Zhu C, Cui H, Wang W (2019) A class of quadratic polynomial chaotic maps and its application in cryptography. IEEE Access 7:34141–34152. https://doi.org/10.1109/access.2019.2902873
Acknowledgements
This work was Supported by the Open Research Fund of Key Laboratory of Network Crime Investigation of Hunan Provincial Colleges under Grant NO. 2020WLFZZC002, in part by National innovation and entrepreneurship training program for college students under Grant NO. S201910447044 and Liaocheng University innovation and entrepreneurship training program for college students under Grant NO. cxcy2019y091.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhu, S., Zhu, C., Fu, Y. et al. A secure image encryption scheme with compression-confusion-diffusion structure. Multimed Tools Appl 79, 31957–31980 (2020). https://doi.org/10.1007/s11042-020-09699-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-09699-4