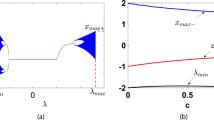
Abstract
This paper presents a multi-mode generalized modified transition chaotic map and a switched chaotic encryption scheme based on it. Eight different modes of operation can be selected based on the map graph (concave or convex), the range modification procedure (shrinking or widening) and the sign of one of its independent parameters. The generalization and modification preserve the controllability and continuous chaotic behavior properties, respectively. For the same encryption key and map equation, multi-mode operation occurs through switching between four alternatives of the dependent parameters. Switching between various modes is shown to overpass single modes in randomness by investigating the frequency distribution, autocorrelation function, histograms and 0-1 test. In addition, most bits, 75%, of the scaled and quantized chaotic output are shown to be suitable for pseudo-random number generation based on National Institute of Standards & Technology (NIST) statistical test suite. The performance of the proposed scheme is validated for several speech, grayscale and RGB images through various evaluation criteria, where good results are achieved. These criteria include basic perceptual and statistical aspects, the more advanced NIST tests, key sensitivity and robustness against brute force and differential attacks. The efficiency of the scheme is improved by up to three or six times faster than encrypting one sample or one channel of a pixel at a time for speech and image inputs, respectively. The proposed scheme demonstrates good security and efficiency with more applied evaluation criteria compared to similar recent works.









Similar content being viewed by others
References
(2018) ITU-T Test Signals for Telecommunication Systems, Test vectors associated to Rec. ITU-T P.501, accessed. https://www.itu.int/net/itu-t/sigdb/genaudio/AudioForm-g.aspx?val=10000501
(2018) We shall fight on the beaches (audio), accessed. https://www.winstonchurchill.org/resources/speeches/1940-the-finest-hour/we-shall-never-surrender/
(2018) The royer track (audio), accessed. https://www.prosoundtraining.com/2010/03/10/a-downloadable-speech-track-the-royer-track/
Abd-El-Hafiz SK, Radwan AG, AbdEl-Haleem SH (2015) Encryption applications of a generalized chaotic map. Applied Mathematics & Information Sciences 9(6):3215
Alawida M, Samsudin A, Teh JS, Alkhawaldeh RS (2019) A new hybrid digital chaotic system with applications in image encryption. Signal Process 160:45–58
Anwar S, Meghana S (2019) A pixel permutation based image encryption technique using chaotic map. Multimedia tools and applications 78(19):27569–27590
Cao C, Sun K, Liu W (2018) A novel bit-level image encryption algorithm based on 2d-LICM hyperchaotic map. Signal Process 143:122–133
Faragallah OS, AlZain MA, El-Sayed HS, Al-Amri JF, El-Shafai W, Afifi A, Naeem EA, Soh B (2020) Secure color image cryptosystem based on chaotic logistic in the frFT domain. Multimedia Tools and Applications 79(3):2495–2519
Fu C, Jj Chen, Zou H, Meng W h, Yf Zhan, Yw Y u (2012) A chaos-based digital image encryption scheme with an improved diffusion strategy. Optics express 20(3):2363–2378
Garasym O, Taralova I (2013) High-speed encryption method based on switched chaotic model with changeable parameters. In: Internet Technology and Secured Transactions (ICITST), 2013 8th International Conference for, IEEE, pp 37–42
Garofolo JS (1993) TIMIT Acoustic phonetic continuous speech corpus. Linguistic Data Consortium, 1993
Gayathri J, Subashini S (2018) A spatiotemporal chaotic image encryption scheme based on self adaptive model and dynamic keystream fetching technique. Multimedia Tools and Applications 77(19):24751–24787
Gottwald GA, Melbourne I (2004) A new test for chaos in deterministic systems. Proceedings of the Royal Society of London Series a: Mathematical. Phys Eng Sci 460(2042):603–611
Gottwald GA, Melbourne I (2005) Testing for chaos in deterministic systems with noise. Physica D: Nonlinear Phenomena 212(1-2):100–110
Gottwald GA, Melbourne I (2009) On the implementation of the 0–1 test for chaos. SIAM J Appl Dyn Syst 8(1):129–145
Gottwald GA, Melbourne I (2016) The 0-1 test for chaos: A review. In: Chaos detection and predictability, Springer, pp 221–247
Hou J, Xi R, Liu P, Liu T (2017) The switching fractional order chaotic system and its application to image encryption. IEEE/CAA Journal of Automatica Sinica 4(2):381–388
Hu J, Ww Tung, Gao J, Cao Y (2005) Reliability of the 0-1 test for chaos. Phys Rev E 72(5):056207
Jankowski C, Kalyanswamy A, Basson S, Spitz J (1990) Ntimit: A phonetically balanced, continuous speech, telephone bandwidth speech database. In: 1990 International Conference on Acoustics, Speech, and Signal Processing, 1990. ICASSP-90., IEEE, pp 109–112. https://catalog.ldc.upenn.edu/LDC93S2
Khan M, Masood F (2019) A novel chaotic image encryption technique based on multiple discrete dynamical maps. Multimedia Tools and Applications 78(18):26203–26222
Lee TH, Park JH, Jung HY, Lee SM (2015) Improving security in communication switched chaotic systems. In: Consumer electronics (ICCE), 2015, IEEE International Conference on, IEEE, pp 283--284
Lian S (2008) Multimedia content encryption: techniques and applications. CRC press
Liu H, Wen F, Kadir A (2019) Construction of a new 2D Chebyshev-sine map and its application to color image encryption. Multimedia Tools and Applications 78(12):15997–16010
Luo Y, Yu J, Lai W, Liu L (2019) A novel chaotic image encryption algorithm based on improved baker map and logistic map. Multimedia Tools and Applications 78(15):22023–22043
Matthews P (2020) On the implementation of the 0–1 test for chaos. 0 - 1 test for chaos, (https://www.mathworkscom/matlabcentral/fileexchange/25050-0-1-test-for-chaos), MATLAB Central File Exchange Retrieved July 24, 2020
Pak C, An K, Jang P, Kim J, Kim S (2019) A novel bit-level color image encryption using improved 1D chaotic map. Multimedia Tools and Applications 78(9):12027–12042
Pande A, Zambreno J (2013) A chaotic encryption scheme for real-time embedded systems: design and implementation. Telecommun Syst 52:551–561. https://doi.org/10.1007/s11235-011-9460-1
Radwan AG, Abd-El-Hafiz SK, AbdElHaleem SH (2014) An image encryption system based on generalized discrete maps. In: IEEE International Conference on Electronics, Circuits and Systems (ICECS), 21st, IEEE, pp 283–286
Radwan AG, AbdElHaleem SH, Abd-El-Hafiz SK (2016) Symmetric encryption algorithms using chaotic and non-chaotic generators: A review. Journal of advanced research 7(2):193–208
Rajagopalan S, Poori S, Narasimhan M, Rethinam S, Kuppusamy CV, Balasubramanian R, Annamalai VMP, Rengarajan A (2020) Chua’s diode and strange attractor: a three-layer hardware–software co-design for medical image confidentiality. IET Image Process 14(7):1354–1365
Rukhin A, Soto J, Nechvatal J, Smid M, Barker E (2001) A statistical test suite for random and pseudorandom number generators for cryptographic applications. Tech. rep., DTIC Document
Sathiyamurthi P, Ramakrishnan S (2017) Speech encryption using chaotic shift keying for secured speech communication. EURASIP Journal on Audio Speech, and Music Processing 2017(1):20
Sathiyamurthi P, Ramakrishnan S (2020) Speech encryption algorithm using FFT and 3d-Lorenz–logistic chaotic map. Multimedia Tools and Applications, pp 1–19
Sayed WS, Fahmy HA, Rezk AA, Radwan AG (2017) Generalized smooth transition map between tent and logistic maps. International Journal of Bifurcation and Chaos 27(01):1730004
Sayed WS, Henein MM, Abd-El-Hafiz SK, Radwan AG (2017) Generalized dynamic switched synchronization between combinations of fractional-order chaotic systems. Complexity 2017
Sayed WS, Radwan AG, Fahmy HA (2015) Design of positive, negative, and alternating sign generalized logistic maps Discrete Dynamics in Nature and Society
Sayed WS, Radwan AG, Fahmy HA (2015) Design of a generalized bidirectional tent map suitable for encryption applications. In: 11Th international computer engineering conference (ICENCO), IEEE, pp 207--211
Sayed WS, Tolba MF, Radwan AG, Abd-El-Hafiz SK (2019) FPGA Realization of a speech encryption system based on a generalized modified chaotic transition map and bit permutation. Multimedia Tools and Applications 78(12):16097–16127
Sheela S, Suresh K, Tandur D (2018) Image encryption based on modified Henon map using hybrid chaotic shift transform. Multimedia Tools and Applications 77(19):25223–25251
Thakur S, Singh AK, Ghrera SP, Elhoseny M (2019) Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimedia tools and Applications 78(3):3457–3470
Weber AG (1997) The USC-SIPI image database version 5. USC-SIPI Report 315:1–24
Zhou Y, Bao L, Chen CP (2013) Image encryption using a new parametric switching chaotic system. Signal processing 93(11):3039–3052
Acknowledgements
This research was supported financially by Cairo University, Egypt, research project no. 16-120.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix: List of Abbreviations and Symbols
List of Abbreviations
- NIST:
-
National Institute of Standards & Technology
- DES:
-
Data Encryption Standard
- AES:
-
Advanced Encryption Standard
- PRNG:
-
Pseudo-Random Number Generator
- LSB:
-
Least Significant Bit
- PV:
-
P-value distribution
- PP:
-
Proportion of passing sequences
- MSB:
-
Most Significant Bit
- MSE:
-
Mean Squared Error
- NSCR:
-
Number of Samples Change Rate
- UACI:
-
Unified Average Changing Intensity
- NPCR:
-
Number of Pixels Change Rate
- FPGA:
-
Field Programmable Gate Array
List of Symbols
- x, xn:
-
Iterated map variable
- f(.):
-
Map equation
- λ :
-
Main parameter
- μ :
-
Shifting parameter
- a :
-
Scaling parameter
- c :
-
Shaping parameter
- x max+ :
-
Maximum value of x for generalized concave map
- xmax− (xmin−):
-
Maximum (Minimum) value of x for generalized convex map
- β :
-
Range modification parameter
- Rmin (Rmax):
-
Lower (Upper) bound on the map domain
- M(n):
-
Mean square displacement
- K :
-
Growth rate (0-1 test)
- z n :
-
Chaotic output after scaling and quantization
- hex2dec(.):
-
Converts a hexadecimal number to a decimal number
- K1, K2, K3, K4:
-
Sub-key values in hexadecimal format
- xfix, afix, βfix, cfix:
-
Pre-defined fixed values of the parameter that guarantee chaotic behavior
- xkey, akey, βkey, ckey:
-
Key dependent perturbations
- P s u m :
-
Input dependent perturbation
- mod(m, 10):
-
Remainder after dividing m by 10
- r x y :
-
Correlation coefficient
- P(Si):
-
Probability of the sample value Si
- p :
-
Number of bits per sample
- P(i, j):
-
Pixel value
Rights and permissions
About this article
Cite this article
Sayed, W.S., Tolba, M.F., Radwan, A.G. et al. A switched chaotic encryption scheme using multi-mode generalized modified transition map. Multimed Tools Appl 80, 5373–5402 (2021). https://doi.org/10.1007/s11042-020-09756-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-09756-y