Abstract
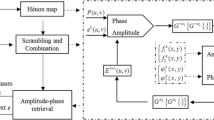
In order to increase encryption capacity and improve transmission efficiency, this paper investigates an encryption scheme for multiple-image based on cascaded gyrator transforms and high-dimensional chaos. Firstly, each plainimage is converted into a real matrix through modulation, quaternion gyrator transform and sharing. The real matrices are connected in turn by plural coding and gyrator transforms. During the process of cascade, phase truncation and preservation operations are performed. The phase of the preceding transformation is modulated by that of the latter complex matrix to enhance security. Followed by splicing and scrambling, a real-valued ciphertext can be obtained. At the receiver end, all the plaintext images can be restituted by the reverse operation of the encryption process using the authorized keys. The adoption of high-dimensioanl chaos and Kronecker product further guarantees the security of the cryptosystem. The numerical results performed on 300 color images have demonstrated that the average PSNR of correctly decrypted images is up to 303.9939 dB, the NMSE is as low as 2.8024 × 10−28 and SSIM is equal to 1.0000. The analysis of sensitivity, statistical characteristic and robustness proves the feasibility and relibility of the proposed encryption scheme.

















Similar content being viewed by others
References
Abdelfattah M, Hegazy SF, Areed NFF, Obayya SSA (2020) Compact optical asymmetric cryptosystem based on unequal modulus decomposition of multiple color images. Opt Lasers Eng 129:106063
Abuturab MR (2020) Multiple-information security system using key image phase and chaotic random phase encoding in Fresnel transform domain. Opt Lasers Eng 124:105810
Arbeláez P, Maire M, Fowlkes C, Malik J (2011) Contour detection and hierarchical image segmentation. IEEE Trans Pattern Anal Mach Intell 33(5):898–916
Bhatnagar G, Wu QMJ, Raman B (2013) Discrete fractional wavelet transform and its application to multiple encryption. Inf Sci 223:297–316
Chen H, Tanougast C, Liu Z, Blondel W, Hao B (2018) Optical hyperspectral image encryption based on improved Chirikov mapping and gyrator transform. Opt Lasers Eng 107:62–70
Chen BJ, Yu M, Tian YH, Li LD, Wang DC, Sun XM (2018) Multiple-parameter fractional quaternion Fourier transform and its application in colour image encryption. IET Image Process 12(12):2238–2249
Chidambaram N, Raj P, Thenmozhi K, Amirtharajan R (2020) Advanced framework for highly secure and cloud-based storage of colour images. IET Image Process 14:3143–3153. https://doi.org/10.1049/iet-ipr.2018.5654
Czaplewski B, Dzwonkowski M, Rykaczewski R (2014) Digital fingerprinting for color images based on the quaternion encryption scheme. Pattern Recogn Lett 46:11–19
Dasgupta T, Paral P, Bhattacharya S, (2014) Grayscale image encryption based on high-dimensional fractional order Chua’s system. In: 2nd international conference on advanced computing networking and informatics.
Dorgham O, Al-Rahamneh B, Almomani A et al (2018) Enhancing the security of exchanging and storing DICOM medical images on the cloud. Int J Cloud Appl Comput 8(1):154–172
Faragallah OS, Afifi A, El-Shafai W, El-Sayed HS, Alzain MA, Al-Amri JF, El-Samie FE (2020) Efficiently encrypting color images with few details based on RC6 and different operation modes for cybersecurity applications. IEEE Access 8:103200–103218
Fei-Fei L, Fergus R, Perona P (2004) Learning generative visual models from few examples: an incremental bayesian approach tested on 101 object categories. In: CVPR Workshop of Generative Model Based Vision
Firdous A, Aur R, Missen MMS (2019) A highly efficient color image encryption based on linear transformation using chaos theory and SHA-2. Multimed Tools Appl 78:24809–24835
Ghadirli HM, Nodehi A, Enayatifar R (2019) An overview of encryption algorithms in color images. Signal Process 164:163–185
Goléa NEH, Melkemi KE (2019) ROI-based fragile watermarking for medical image tamper detection. Int J High Performance Comput Network 13(2):199–210
Gupta B, Agrawal DP, Yamaguchi S (2016) Handbook of research on modern cryptographic solutions for computer and cyber security. IGI Global.
Kang XJ, Ming AL, R. Tao (2019) Reality-preserving multiple parameter discrete fractional angular transform and its application to color image encryption. IEEE Trans Circ Syst Vid 29(6): 1595–1607
Kaur M, Kumar V (2020) A comprehensive review on image encryption techniques. Arch Comput Methods in Eng 27:15–43
Kumar A (2019) Design of secure image fusion technique using cloud for privacy-preserving and copyright protection. Int J Cloud Appl Comput 9(3):22–36
Li X, Meng X, Yang X, Wang Y, Yin Y, Peng X, He W, Dong G, Chen H (2018) Multiple-image encryption via lifting wavelet transform and XOR operation based on compressive ghost imaging scheme. Opt Lasers Eng 102:106–111
Li Z, Zhao M, Jiang H, Xu Q (2019) Keyword guessing on multi-user searchable encryption. Int J High Perform Comput Netw 14(1):60–68
Liu H, Wang X (2010) Color image encryption based on one-time keys and robust chaotic maps. Comput Math Appl 59(10):3320–3327
Liu H, Wang X (2011) Color image encryption using spatial bit-level permutation and high-dimension chaotic system. Opt Commun 284(16–17):3895–3903
Liu H, Wang X, Kadir A (2012) Image encryption using DNA complementary rule and chaotic maps. Appl Soft Comput 12:1457–1466
Luan GY, Li AC, Zhang DM, Wang DX (2019) Asymmetric image encryption and authentication based on equal modulus decomposition in the Fresnel transform domain. IEEE Photonics J 11(1):6900207
Mamta, Gupta B B (2019) An efficient KP design framework of attribute-based searchable encryption for user level revocation in cloud. Concurrency and Computation: Practice and Experience
Mu Y, Zhou Z (2019) Visual vocabulary tree-based partial-duplicate image retrieval for coverless image steganography. Int J High Performance Comput Network 14(3):333–341
Premkamal PK, Pasupuleti SK, Alphonse PJA (2020) Efficient escrow-free CP-ABE with constant size ciphertext and secret key for big data storage in cloud. Int J Cloud Appl Comput 10(1):28–45
Qin C, Zhang X (2015) Effective reversible data hiding in encrypted image with privacy protection for image content. J Vis Commun Image Represent 31:154–164
Refregier P, Javidi B (1995) Optical image encryption based on input plane and Fourier plane random encoding. Opt Lett 20(7):767–769
Shao Z, Shu H, Wu J, Dong Z, Coatrieux G, Coatrieux JL (2014) Double color image encryption using iterative phase retrieval algorithm in quaternion gyrator domain. Opt Express 22(5):4932–4943
Shao Z, Shang Y, Fu X, Yuan H, Shu H (2018) Double-image cryptosystem using chaotic map and mixture amplitude-phase retrieval in gyrator domain. Multimed Tools Appl 77:1285–1298
Shao Z, Shang Y, Tong Q, Ding H, Zhao X, Fu X (2018) Multiple color image encryption and authentication based on phase retrieval and partial decryption in quaternion gyrator domain. Multimed Tools Appl 77:25821–25840
Shao Z, Liu X, Yao Q, Qi N, Shang Y, Zhang J (2020) Multiple-image encryption based on chaotic phase mask and equal modulus decomposition in quaternion gyrator domain. Signal Process Image Commun 80:115662
Sivaraman R, Rajagopalan S, Rayappan JBB, Amirtharajan R (2020) Ring oscillator as confusion–diffusion agent: a complete TRNG drove image security. IET Image Process 14:2987–2997. https://doi.org/10.1049/iet-ipr.2019.0168
Sui L, Xu M, Huang C, Adhikari A, Tian A, Asundi A (2018) Multiple-image encryption by space multiplexing based on vector quantization and interference. OSA Continuum 1(4):1370–1384
Sui L, Zhang X, Huang C, Tian A, Asundi AK (2019) Silhouette-free interference-based multiple-image encryption using cascaded fractional Fourier transforms. Opt Lasers Eng 113:29–37
Wang X, Gao S (2020) Image encryption algorithm based on the matrix semi-tensor product with a compound secret key produced by a Boolean network. Inf Sci 539:195–214
Wang X, Gao S (2020) Image encryption algorithm for synchronously updating Boolean networks based on matrix semi-tensor product theory. Inf Sci 507:16–36
Wang XY, Yang L, Liu R, Kadir A (2010) A chaotic image encryption algorithm based on perceptron model. Nonlinear Dyn 62(3):615–621
Wang X, Teng L, Qin X (2012) A novel colour image encryption algorithm based on chaos. Signal Process 92(4):1101–1108
Wang Q, Guo Q, Lei L (2014) Multiple-image encryption system using cascaded phase mask encoding and a modified Gerchberg–Saxton algorithm in gyrator domain. Opt Commun 320:12–21
Wang X, Liu L, Zhang Y (2015) A novel chaotic block image encryption algorithm based on dynamic random growth technique. Opt Lasers Eng 66:10–18
Wang X, Zhang Y, Bao X (2015) A novel chaotic image encryption scheme using DNA sequence operations. Opt Lasers Eng 73:53–61
Wang X, Feng L, Zhao H (2019) Fast image encryption algorithm based on parallel computing system. Inf Sci 486:340–358
Yao Q, Shao Z, Shang Y, Ding H, Liu X, Zeng R, Tong Q (2020) Color image encryption based on discrete trinion Fourier transform and random-multiresolution singular value decomposition. Multimed Tools Appl 79:27555–27581
Ye H, Zhou N, Gong L (2020) Multi-image compression-encryption scheme based on quaternion discrete fractional Hartley transform and improved pixel adaptive diffusion. Signal Process 175:107652
Yu Z, Gao C, Jing Z, Gupta BB, Cai Q (2018) A practical public key encryption scheme based on learning parity with noise. IEEE Access 6:31918–31923
Yu C, Li J, Li X, Ren X, GuptaBB (2018) Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimed Tools Appl 77:4585–4608
Zhang YQ, Wang XY (2014) A symmetric image encryption algorithm based on mixed linear–nonlinear coupled map lattice. Inf Sci 273:329–351
Zhang Y, Wang X (2015) A new image encryption algorithm based on non-adjacent coupled map lattices. Appl Soft Comput 26:10–20
Zhang L, Zhou Y, Huo D, Li J, Zhou X (2018) Multiple-image encryption based on double random phase encoding and compressive sensing by using a measurement array preprocessed with orthogonal-basis matrices. Opt Laser Technol 105:162–170
Zheng Q, Wang X, Khan M, Zhang W, Gupta B, Guo W (2017) A lightweight authentication encryption based on chaotic SCML for railway cloud service. IEEE Access 6:711–722
Acknowledgements
This work was supported by the National Natural Science Foundation of China (61876112, 61601311), Project of Beijing Excellent Talents (2016000020124G088) and Beijing Municipal Education Research Plan Project (SQKM201810028018).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sun, X., Shao, Z., Shang, Y. et al. Multiple-image encryption based on cascaded gyrator transforms and high-dimensional chaotic system. Multimed Tools Appl 80, 15825–15848 (2021). https://doi.org/10.1007/s11042-021-10550-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-10550-7