Abstract
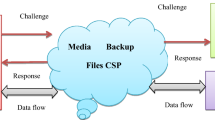
The Internet of Things (IoT) has emerged as one of the most revolutionary technological innovations with the proliferation of applications within almost all fields of the human race. A cloud environment is the main component of IoT infrastructure to make IoT devices efficient, safe, reliable, usable, and autonomous. Reduction in infrastructure cost and demand accessibility of shared resources are essential parts of cloud-based IoT (CIoT) infrastructure. Information leakage in cloud-assisted IoT devices may invite dangerous activities and phenomena. Various cloud-based systems store IoT sensor data and later on access it accordingly. Some of them are public, and some of them are private. Private cloud services must be secured from external as well as internal adversaries. Hence, there must be a robust mechanism to prevent unauthorized access to devices. This paper proposes a novel and efficient protocol based on the Elliptic Curve property known as Elliptic Curve Discrete Logarithm Problem (ECDLP) with hash and XOR functions for the authentication in cloud-based IoT devices. In comparison to the existing protocols, the proposed protocol is resistant to attacks and other security vulnerabilities. The one-way hash function and XOR function effectively ensure a reduction in computation cost. AVISPA and BAN logic have been used for formal analysis of the proposed protocol. As per the performance analysis results, it is clear that the proposed protocol is efficiently suitable for cloud-assisted IoT devices.







Similar content being viewed by others
References
Almuhaideb AM (2021) Re-AuTh: lightweight re-authentication with practical key Management for Wireless Body Area Networks. Arab J Sci Eng 46:8189–8202. https://doi.org/10.1007/s13369-021-05442-9
Alzahrani BA (2021) Secure and efficient cloud-based IoT authenticated key agreement scheme for e-health wireless sensor networks. Arab J Sci Eng 46:3017–3032. https://doi.org/10.1007/s13369-020-04905-9
Amin R, Biswas GP (2016) A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw 36:58–80. https://doi.org/10.1016/j.adhoc.2015.05.020
Amin R, Kumar N, Biswas GP, Iqbal R, Chang V (2018) A light weight authentication protocol for IoT-enabled devices in distributed cloud computing environment. Futur Gener Comput Syst 78:1005–1019. https://doi.org/10.1016/j.future.2016.12.028
Alessandro Armando, David Basin, Jorge Cuellar MR and LV (2001) The high level protocol specification language deliverable details. Avispa
Armando A, Basin D, Boichut Y, et al (2005) The AVISPA tool for the automated validation of Internet security Protocols and applications. Pp 281–285
Bae W, Kwak J (2020) Smart card-based secure authentication protocol in multi-server IoT environment. Multimed Tools Appl 79:15793–15811. https://doi.org/10.1007/s11042-017-5548-2
Banerjee S, Odelu V, Das AK, Srinivas J, Kumar N, Chattopadhyay S, Choo KKR (2019) A provably secure and lightweight anonymous user authenticated session key exchange scheme for Internet of things deployment. IEEE Internet Things J 6:8739–8752. https://doi.org/10.1109/JIOT.2019.2923373
Burrows M, Abadi M, Needham R (1990) A logic of authentication. ACM Trans Comput Syst 8:18–36. https://doi.org/10.1145/77648.77649
Challa S, Das AK, Gope P, Kumar N, Wu F, Vasilakos AV (2020) Design and analysis of authenticated key agreement scheme in cloud-assisted cyber–physical systems. Futur Gener Comput Syst 108:1267–1286. https://doi.org/10.1016/j.future.2018.04.019
Chang CC, Le HD (2016) A provably secure, efficient, and flexible authentication scheme for ad hoc wireless sensor networks. IEEE Trans Wirel Commun 15:357–366. https://doi.org/10.1109/TWC.2015.2473165
Chen F, Tang Y, Cheng X, Xie D, Wang T, Zhao C (2021) Blockchain-based efficient device authentication protocol for medical cyber-physical systems. Secur Commun Networks 2021:1–13. https://doi.org/10.1155/2021/5580939
Chevalier Y, Compagna L, Cuellar J, et al (2006) A High Level Protocol Specification Language for Industrial Security-Sensitive Protocols To cite this version: HAL Id: inria-00099882 A High-Level Protocol Specification Language for Industrial Security-Sensitive Protocols ∗. https://hal.inria.fr/inria-00100219
Chintala RR, Kallepalli H, Kotapati J, et al (2021) Implementing security framework for cloud based IOT network implementing security framework for cloud based IOT network
Do Xuan C, Dao MH, Nguyen HD (2020) APT attack detection based on flow network analysis techniques using deep learning. J Intell Fuzzy Syst 39:4785–4801. https://doi.org/10.3233/JIFS-200694
Dolev D, Yao AC (1983) On the security of public key Protocols. IEEE Trans Inf Theory 29:198–208. https://doi.org/10.1109/TIT.1983.1056650
Gadicha AB, Gupta VBB, Gadicha VB, et al (2021) Multimode approach of data encryption in images through quantum steganography. Pp 99–124
Haack C (2008) What is BAN logic ? Verification of security Protocols what are questions that BAN logic aims to answer ? What are limitations of BAN logic ? BAN logic ’ s model of time formulas: syntax domains formulas: basic formulas formulas: idealized messages
Hankerson D, Menezes A (2011) Elliptic curve cryptography. In: Encyclopedia of cryptography and security. Springer US, Boston, MA, pp. 397–397
Internet A, Protocols S (2006) HLPSL Tutorial. In: Society
Iqbal W, Abbas H, Daneshmand M, Rauf B, Bangash YA (2020) An in-depth analysis of IoT security requirements, challenges, and their countermeasures via software-defined security. IEEE Internet Things J 7:10250–10276. https://doi.org/10.1109/JIOT.2020.2997651
Irshad A, Ahmad HF, Ramzan MS (2016) An efficient and anonymous Chaotic Map based authenticated key agreement for multi-server architecture KSII Trans Internet Inf Syst 10. https://doi.org/10.3837/tiis.2016.12.023
Islam SKH, Biswas GP (2012) An improved pairing-free identity-based authenticated key agreement protocol based on ECC. Procedia Eng 30:499–507. https://doi.org/10.1016/j.proeng.2012.01.890
Kim H, Kim D, Yi O, Kim J (2019) Cryptanalysis of hash functions based on blockciphers suitable for IoT service platform security. Multimed Tools Appl 78:3107–3130. https://doi.org/10.1007/s11042-018-5630-4
Kocher P, Jaffe J, Jun B (1999) Differential power. Analysis pp:388–397
Koppanati RK, Kumar K (2021) P-MEC: polynomial congruence-based multimedia encryption technique over cloud. IEEE Consum Electron Mag 10:41–46. https://doi.org/10.1109/MCE.2020.3003127
Kumar K, Kurhekar M (2016) Economically efficient virtualization over cloud using Docker containers. In: 2016 IEEE international conference on cloud computing in emerging markets (CCEM). IEEE, pp 95–100
Kumari S, Karuppiah M, Das AK, Li X, Wu F, Gupta V (2018) Design of a secure anonymity-preserving authentication scheme for session initiation protocol using elliptic curve cryptography. J Ambient Intell Humaniz Comput 9:643–653. https://doi.org/10.1007/s12652-017-0460-1
Lamport L (1981) Password authentication with insecure communication. Commun ACM 24:770–772. https://doi.org/10.1145/358790.358797
Li H, Li F, Song C, Yan Y (2015) Towards smart card based mutual authentication schemes in cloud computing. KSII Trans Internet Inf Syst 9:2719–2735. https://doi.org/10.3837/tiis.2015.07.022
Manupriya P, Sinha S, Kumar K (2017) V⊕SEE: Video secret sharing encryption technique. In: 2017 Conference on information and communication technology (CICT). IEEE, pp 1–6
Messerges TS, Dabbish EA, Sloan RH (2002) Examining smart-card security under the threat of power analysis attacks. IEEE Trans Comput 51:541–552. https://doi.org/10.1109/TC.2002.1004593
Miller VS (1986) Use of elliptic curves in cryptography. In: Advances in cryptology — CRYPTO ‘85 proceedings. Springer Berlin Heidelberg, Berlin, Heidelberg, pp. 417–426
Muhammad G, Alhussein M (2021) Security, trust, and privacy for the Internet of vehicles: a deep learning approach. IEEE Consum Electron Mag 2248:1–1. https://doi.org/10.1109/MCE.2021.3089880
Nandy T, Yamani M, Bin I et al (2019) Review on security of Internet of things authentication mechanism. IEEE Access 7:151054–151089. https://doi.org/10.1109/ACCESS.2019.2947723
Naseer O, Ullah S, Anjum L (2021) Blockchain-based decentralized lightweight control access scheme for smart grids. Arab J Sci Eng 46:8233–8243. https://doi.org/10.1007/s13369-021-05446-5
Pete P, Patange K, Wankhade M et al (2018) 3E-VMC: an experimental energy efficient model for VMs scheduling over cloud. In: 2018 first international conference on secure cyber computing and communication (ICSCCC). IEEE:322–327
Rangwani D, Om H (2021) A secure user authentication protocol based on ECC for cloud computing environment. Arab J Sci Eng 46:3865–3888. https://doi.org/10.1007/s13369-020-05276-x
Ray PP (2017) A survey of IoT cloud platforms. Futur Comput Informatics J 1:35–46. https://doi.org/10.1016/j.fcij.2017.02.001
Sharma S, Kumar K (2018) GUESS: genetic uses in video encryption with secret sharing. In: Advances in Intelligent Systems and Computing. Springer Verlag, pp. 51–62
Sierra JM, Hernández JC, Alcaide A, Torres J (2004) Validating the use of BAN LOGIC. Lect Notes Comput Sci (including Subser Lect Notes Artif Intell Lect Notes Bioinformatics) 3043:851–858. https://doi.org/10.1007/978-3-540-24707-4_98
Sun H, Wen Q, Zhang H, Jin Z (2013) A novel remote user authentication and key agreement scheme for mobile client-server environment. Appl math. Inf Sci 7:1365–1374. https://doi.org/10.12785/amis/070414
Syverson P, Cervesato I (2001) The logic of authentication Protocols. Pp 63–137
Team A (2006) AVISPA v1. 1 user manual. Inf Soc Technol 1:1–88
Team A (2006) HLPSL Tutorial, A Beginner’s Guide to Modelling and Analysing Internet Security Protocols Inf Technol Solut 1–52
Tsai JL, Lo NW (2015) A privacy-aware authentication scheme for distributed Mobile cloud computing services. IEEE Syst J 9:805–815. https://doi.org/10.1109/JSYST.2014.2322973
Wazid M, Das AK, Kumari S, Li X, Wu F (2016) Provably secure biometric-based user authentication and key agreement scheme in cloud computing. Secur Commun Networks 5:422–437. https://doi.org/10.1002/sec
Wazid M, Das AK, Hussain R, Succi G, Rodrigues JJPC (2019) Authentication in cloud-driven IoT-based big data environment: survey and outlook. J Syst Archit 97:185–196. https://doi.org/10.1016/j.sysarc.2018.12.005
Wazid M, Das AK, Bhat KV, Vasilakos AV (2020) LAM-CIoT: lightweight authentication mechanism in cloud-based IoT environment. J Netw Comput Appl 150:102496. https://doi.org/10.1016/j.jnca.2019.102496
Wessels J (2001) Applications of Ban-Logic
Wu F, Li X, Xu L, Sangaiah AK, Rodrigues JJPC (2018) Authentication protocol for distributed cloud computing: an explanation of the security situations for Internet-of-things-enabled devices. IEEE Consum Electron Mag 7:38–44. https://doi.org/10.1109/MCE.2018.2851744
Wu T-Y, Lee Z, Obaidat MS, Kumari S, Kumar S, Chen CM (2020) An authenticated key exchange protocol for multi-server architecture in 5G networks. IEEE Access 8:28096–28108. https://doi.org/10.1109/ACCESS.2020.2969986
Xue K, Hong P, Ma C (2014) Journal of computer and system sciences a lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. J Comput Syst Sci 80:195–206. https://doi.org/10.1016/j.jcss.2013.07.004
Yang S, Greenberg A, Endsley M (2011) Social computing, Behavioral-Cultural Modeling and Prediction. Springer Berlin Heidelberg, Berlin, Heidelberg
Acknowledgments
We would like to thank the anonymous reviewers for their valuable comments, which helped us to improve the organization, content, and quality of this Manuscript.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Alam, I., Kumar, M. A novel protocol for efficient authentication in cloud-based IoT devices. Multimed Tools Appl 81, 13823–13843 (2022). https://doi.org/10.1007/s11042-022-11927-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-11927-y