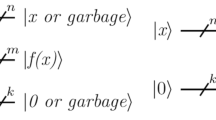Abstract
Cellular Automata (CA) have widely been studied to design cryptographic primitives such as stream ciphers and pseudorandom number generators, focusing in particular on the properties of the underlying local rules. On the other hand, there have been comparatively fewer works concerning the applications of CA to the design of S-boxes and block ciphers, a task that calls for a study of CA global rules in terms of vectorial boolean functions. The aim of this paper is to analyze some of the most basic cryptographic criteria of the global rules of CA. We start by observing that the algebraic degree of a CA global rule equals the degree of its local rule. Then, we characterize the Walsh spectrum of CA induced by permutive local rules, from which we derive a formula for the nonlinearity of such CA. Additionally, we prove that the 1-resiliency property of bipermutive local rules transfers to the corresponding global rules. This result leads us to consider CA global rules from a coding-theoretic point of view: in particular, we show that linear CA are equivalent to linear cyclic codes, observing that the syndrome computation process corresponds to the application of the CA global rule, while the error-correction capability of the code is related to the resiliency order of the global rule.




Similar content being viewed by others
References
Bertoni G, Daemen J, Peeters M, Assche GV (2013) Keccak. In: Proceedings of advances in cryptology—EUROCRYPT 2013, 32nd annual international conference on the theory and applications of cryptographic techniques, Athens, Greece, May 26–30, 2013, pp 313–314
Carlet C (2010a) Boolean functions for cryptography and error correcting codes. Boolean Models Methods Math Comput Sci Eng 2:257–397
Carlet C (2010b) Vectorial boolean functions for cryptography. Boolean Models Methods Math Comput Sci Eng 134:398–469
Daemen J, Rijmen V (2002) The design of Rijndael. Springer-Verlag, New York
Daemen J, Govaerts R, Vandewalle J (1994) An efficient nonlinear shift-invariant transformation. In: Macq B (ed) Proceedings of the 15th symposium on information theory in the Benelux, Werkgemeenschap voor Informatie-en Communicatietheorie, Citeseer, pp 108–115
Formenti E, Imai K, Martin B, Yunès J (2014) Advances on random sequence generation by uniform cellular automata. In: Computing with new resources—essays dedicated to Jozef Gruska on the occasion of his 80th birthday, pp 56–70
Kari J (2012) Basic concepts of cellular automata. In: Handbook of natural computing, pp 3–24
Koc CK, Apohan A (1997) Inversion of cellular automata iterations. IEE Proc Comput Digital Tech 144(5):279–284
Leporati A, Mariot L (2014) Cryptographic properties of bipermutive cellular automata rules. J Cell Autom 9(5–6):437–475
Mariot L, Leporati A (2015) On the periods of spatially periodic preimages in linear bipermutive cellular automata. In: Proceedings of cellular automata and discrete complex systems—21st IFIP WG 1.5 international workshop, AUTOMATA 2015, Turku, Finland, June 8–10, 2015, pp 181–195
Mariot L, Leporati A (2016) Resilient vectorial functions and cyclic codes arising from cellular automata. In: Proceedings of cellular automata—12th international conference on cellular automata for research and industry, ACRI 2016, Fez, Morocco, September 5–8, 2016, pp 34–44
Martin B (2008) A walsh exploration of elementary CA rules. J Cell Autom 3(2):145–156
McEliece R (2002) The theory of information and coding. Cambridge University Press, Cambridge
Meier W, Staffelbach O (1991) Analysis of pseudo random sequence generated by cellular automata. In: Proceedings of advances in cryptology—EUROCRYPT ’91, workshop on the theory and application of of cryptographic techniques, Brighton, UK, April 8–11, 1991, pp 186–199
Nyberg K (1994) S-boxes and round functions with controllable linearity and differential uniformity. In: Proceedings of fast software encryption: second international workshop. Leuven, Belgium, 14–16 December 1994, pp 111–130
Rijmen V, Barreto PSLM, Filho DLG (2008) Rotation symmetry in algebraically generated cryptographic substitution tables. Inf Process Lett 106(6):246–250
Shannon CE (1949) Communication theory of secrecy systems. Bell Labs Tech J 28(4):656–715
Siegenthaler T (1985) Decrypting a class of stream ciphers using ciphertext only. IEEE Trans Comput 34(1):81–85
Stinson DR (1995) Cryptography—theory and practice. Discrete mathematics and its applications series. CRC Press, Boca Raton
Stinson DR (2004) Combinatorial designs—constructions and analysis. Springer, Berlin
Ulam S (1952) Random processes and transformations. Proc Int Congr Math 2:264–275
Von Neumann J (1966) Theory of self-reproducing automata. Edited by Burks, Arthur W. University of Illinois Press, Champaign
Wolfram S (1983) Statistical mechanics of cellular automata. Rev Mod Phys 55(3):601
Wolfram S (1985) Cryptography with cellular automata. In: Proceedings of advances in cryptology—CRYPTO ’85, Santa Barbara, California, USA, August 18–22, 1985, pp 429–432
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mariot, L., Leporati, A. A cryptographic and coding-theoretic perspective on the global rules of cellular automata. Nat Comput 17, 487–498 (2018). https://doi.org/10.1007/s11047-017-9635-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11047-017-9635-0