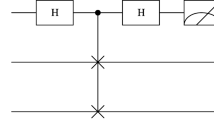
Abstract
A novel quantum private comparison protocol based on a differential phase shift scheme is presented in this paper. In our protocol, two distrustful participants can compare the equality of information with the help of a semi-honest third party. Taking advantages of differential phase shift scheme, this protocol employs weak coherent pulses instead of single photons and can be implemented without expensive and impractical quantum devices, such as entangled photon source and quantum memory. Therefore, it is simpler and more flexible than previous protocols. Moreover, in principle, nearly 100 % qubit efficiency can be achieved because all photon counts obtained by TP contribute to the comparison. The correctness and security of the protocol are also discussed.



Similar content being viewed by others
References
Yao, A.C.: Protocols for secure computations. In: Proceedings of the 23rd Annual Symposium on Foundations of Computer Science, pp. 160–164 (1982)
Boudot, F., Schoenmakers, B., Traore, J.: A fair and efficient solution to the socialist millionaires’ problem. Discrete Appl. Math. 111(1), 23–36 (2001)
Shor, P.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 41(2), 303–332 (1999). doi:10.1137/S0036144598347011
Bennett, C., Brassard, G., et al.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, vol. 175. Bangalore, India (1984)
Inoue, K., Waks, E., Yamamoto, Y.: Differential phase shift quantum key distribution. Phys. Rev. Lett. 89(3), 37902 (2002)
Noh, T.: Counterfactual quantum cryptography. Phys. Rev. Lett. 103(23), 230501 (2009)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829 (1999)
Karlsson, A., Koashi, M., Imoto, N.: Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 59, 162–168 (1999). doi:10.1103/PhysRevA.59.162
Inoue, K., Ohashi, T., Kukita, T., Watanebe, K., Hayashi, S., Honjo, T., Takesue, H.: Differential-phase-shift quantum secret sharing. Opt. Express 16(20), 15469–15476 (2008)
Long, G.L., Liu, X.S.: Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 65, 032302 (2002). doi:10.1103/PhysRevA.65.032302
Boström, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89(18), 187902 (2002)
Deng, F.G., Long, G.L.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 69, 052319 (2004). doi:10.1103/PhysRevA.69.052319
Wang, J., Zhang, Q., Tang, Cj: Quantum secure direct communication based on order rearrangement of single photons. Phys. Lett. A 358(4), 256–258 (2006). doi:10.1016/j.physleta.2006.05.035
Giovannetti, V., Lloyd, S., Maccone, L.: Quantum private queries. Phys. Rev. Lett. 100(23), 230502 (2008)
De Martini, F., Giovannetti, V., Lloyd, S., Maccone, L., Nagali, E., Sansoni, L., Sciarrino, F.: Experimental quantum private queries with linear optics. Phys. Rev. A 80(1), 010302 (2009)
Gao, F., Liu, B., Wen, Q.Y., Chen, H.: Flexible quantum private queries based on quantum key distribution (2011). arXiv:1111.1511 (arXiv, preprint)
Hillery, M., Ziman, M., Bužek, V., Bieliková, M.: Towards quantum-based privacy and voting. Phys. Lett. A 349(1), 75–81 (2006)
Vaccaro, J.A., Spring, J., Chefles, A.: Quantum protocols for anonymous voting and surveying. Phys. Rev. A 75(1), 012333 (2007)
Piotrowski, E.W., Sładkowski, J.: Quantum auctions: facts and myths. Phys. A Stat. Mech. Appl. 387(15), 3949–3953 (2008)
Hogg, T., Harsha, P., Chen, K.Y.: Quantum auctions. Int. J. Quantum Inf. 5(05), 751–780 (2007)
Patel, N.: Quantum games: states of play. Nature 445(7124), 144–146 (2007)
Jia, H.Y., Wen, Q.Y., Song, T.T., Gao, F.: Quantum protocol for millionaire problem. Opt. Commun. 284(1), 545–549 (2011)
Zhang, W.W., Zhang, K.J.: Cryptanalysis and improvement of the quantum private comparison protocol with semi-honest third party. Quantum Inf. Process. 12(5), 1981–1990 (2013). doi:10.1007/s11128-012-0507-3
Yang, Y.G., Wen, Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 42(5), 055,305 (2009). http://stacks.iop.org/1751-8121/42/i=5/a=055305
Yang, Y.G., Cao, W.F., Wen, Q.Y.: Secure quantum private comparison. Phys. Scr. 80(6), 065002 (2009). http://stacks.iop.org/1402-4896/80/i=6/a=065002
Chen, X.B., Xu, G., Niu, X.X., Wen, Q.Y., Yang, Y.X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 283(7), 1561–1565 (2010) doi:10.1016/j.optcom.2009.11.085, http://www.sciencedirect.com/science/article/pii/S0030401809012668
Liu, W., Wang, Y.B., Jiang, Z.T.: An efficient protocol for the quantum private comparison of equality with w state. Opt. Commun. 284(12), 3160–3163 (2011). doi:10.1016/j.optcom.2011.02.017
Liu, W., Wang, Y.B.: Quantum private comparison based on ghz entangled states. Int. J. Theor. Phys. 51(11), 3596–3604 (2012). doi:10.1007/s10773-012-1246-z
Wen, L., Yong-Bin, W., Wei, C.: Quantum private comparison protocol based on bell entangled states. Commun. Theor. Phys. 57(4), 583–588 (2012). doi:10.1088/0253-6102/57/4/11
Jia, H.Y., Wen, Q.Y., Li, Y.B., Gao, F.: Quantum private comparison using genuine four-particle entangled states. Int. J. Theor. Phys. 51(4), 1187–1194 (2012). doi:10.1007/s10773-011-0994-5
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using epr pairs. Quantum Inf. Process. 11(2), 373–384 (2012). doi:10.1007/s11128-011-0251-0
Liu, W., Wang, Y.B., Jiang, Z.T., Cao, Y.Z.: A protocol for the quantum private comparison of equality with chi-type state. Int. J. Theor. Phys. 51(1), 69–77 (2012). doi:10.1007/s10773-011-0878-8
Yang, Y.G., Xia, J., Jia, X., Shi, L., Zhang, H.: New quantum private comparison protocol without entanglement. Int. J. Quantum Inf. 10(6) (2012). doi:10.1142/S0219749912500657
Xu, G.A., Chen, X.B., Wei, Z.H., Li, M.J., Yang, Y.X.: An efficient protocol for the quantum private comparison of equality with a four-qubit cluster state. Int. J. Quantum Inf. 10(4) (2012). doi:10.1142/S0219749912500451
Liu, W., Wang, Y.B., Jiang, Z.T., Cao, Y.Z., Cui, W.: New quantum private comparison protocol using x-type state. Int. J. Theor. Phys. 51(6), 1953–1960 (2012). doi:10.1007/s10773-011-1073-7
Li, J., Jin, H., Jing, B.: Improved eavesdropping detection strategy based on four-particle cluster state in quantum direct communication protocol. Chin. Sci. Bull. 57(34), 4434–4441 (2012)
Liu, B., Gao, F., Jia, H., Huang, W., Zhang, W., Wen, Q.: Efficient quantum private comparison employing single photons and collective detection. Quantum Inf. Process. 12(2), 887–897 (2013). doi:10.1007/s11128-012-0439-y
Chang, Y.J., Tsai, C.W., Hwang, T.: Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process. 12(2), 1077–1088 (2013). doi:10.1007/s11128-012-0454-z
Sun, Z., Long, D.: Quantum private comparison protocol based on cluster states. Int. J. Theor. Phys. 52(1), 212–218 (2013). doi:10.1007/s10773-012-1321-5
Lin, S., Sun, Y., Liu, X.F., Yao, Z.Q.: Quantum private comparison protocol with d-dimensional bell states. Quantum Inf. Process. 12(1), 559–568 (2013). doi:10.1007/s11128-012-0395-6
Lo, H.K.: Insecurity of quantum secure computations. Phys. Rev. A 56(2), 1154 (1997)
Li, Y.B., Wen, Q.Y., Gao, F., Jia, H.Y., Sun, Y.: Information leak in Liu et al.’s quantum private comparison and a new protocol. Eur. Phys. J. D 66(4) (2012). doi:10.1140/epjd/e2012-30065-9
Yang, Y.G., Xia, J., Jia, X., Zhang, H.: Comment on quantum private comparison protocols with a semi-honest third party. Quantum Inf. Process. 12(2), 877–885 (2013). doi:10.1007/s11128-012-0433-4
Liu, X.T., Zhao, J.J., Wang, J., Tang, C.J.: Cryptanalysis of the secure quantum private comparison protocol. Phys. Scr. 87(6), 065004 (2013). http://stacks.iop.org/1402-4896/87/i=6/a=065004
Waks, E., Takesue, H., Yamamoto, Y.: Security of differential-phase-shift quantum key distribution against individual attacks. Phys. Rev. A 73(1), 012344 (2006)
Curty, M., Tamaki, K., Moroder, T.: Effect of detector dead times on the security evaluation of differential-phase-shift quantum key distribution against sequential attacks. Phys. Rev. A 77(5, Part a) (2008). doi:10.1103/PhysRevA.77.052321
Chen-Xu, F., Rong-Zhen, J., Wen-Han, Z.: Performance of differential-phase-shift keying protocol applying 1310 nm up-conversion single-photon detector. Chin. Phys. Lett. 25(9), 3135–3137 (2008)
Zhao, Y.B., Fung, C.H.F., Han, Z.F., Guo, G.C.: Security proof of differential phase shift quantum key distribution in the noiseless case. Phys. Rev. A 78, 042330 (2008). doi:10.1103/PhysRevA.78.042330
Gomez-Sousa, H., Curty, M.: Upper bounds on the performance of differential-phase-shift quantum key distribution. Quantum Inf. Comput. 9(1–2), 62–80 (2009)
Rong-Zhen, J., Chen-Xu, F., Hai-Qiang, M.: Analysis of the differential-phase-shift-keying protocol in the quantum-key-distribution system. Chin. Phys. B 18(3), 915–917 (2009)
Ma, L., Nam, S., Xu, H., Baek, B., Chang, T., Slattery, O., Mink, A., Tang, X.: 1310 nm differential-phase-shift qkd system using superconducting single-photon detectors. New J. Phys. 11 (2009). doi:10.1088/1367-2630/11/4/045020
Zhang, H., Wang, J., Liu, X., Wei, Z., Liu, S.: A fiber-based differential phase shift quantum key distribution scheme with higher key creation efficiency. Opt. Commun. 282(14), 3037–3039 (2009). doi:10.1016/j.optcom.2009.03.066
Jindong, W., Xiaojuan, Q., Huani, Z., Zhengjun, W., Changjun, L., Songhao, L.: A free-space-based differential phase shift quantum key distribution scheme with higher key creation efficiency. Opt. Commun. 282(16), 3379–3381 (2009). doi:10.1016/j.optcom.2009.05.020
Wen, K., Tamaki, K., Yamamoto, Y.: Unconditional security of single-photon differential phase shift quantum key distribution. Phys. Rev. Lett. 103(17) (2009). doi:10.1103/PhysRevLett.103.170503
Kawahara, H., Inoue, K.: Differential-phase-shift quantum key distribution with segmented pulse trains. Phys. Rev. A 83(6) (2011). doi:10.1103/PhysRevA.83.062318
Kawahara, H., Oka, T., Inoue, K.: Differential-phase-shift quantum key distribution with phase modulation to combat sequential attacks. Phys. Rev. A 84(5) (2011). doi:10.1103/PhysRevA.84.052311
Namekata, N., Takesue, H., Honjo, T., Tokura, Y., Inoue, S.: High-rate quantum key distribution over 100 km using ultra-low-noise, 2-ghz sinusoidally gated ingaas/inp avalanche photodiodes. Opt. Express 19(11), 10632–10639 (2011)
Xiao-Lin, Y., Jin-Dong, W., Zheng-Jun, W., Bang-Hong, G., Song-Hao, L.: A new multi-wavelength two-way quantum key distribution system with a single optical source. Acta Phys. Sin. 61(18) (2012). doi:10.7498/aps.61.184215
Lütkenhaus, N.: Security against individual attacks for realistic quantum key distribution. Phys. Rev. A 61(5), 052304 (2000)
Acknowledgments
This work was sponsored by the National Natural Science Foundation of China (Project No. 61101073) and the Graduate Innovation Funds for the National University of Defense Technology.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, Xt., Zhang, B., Wang, J. et al. Differential phase shift quantum private comparison. Quantum Inf Process 13, 71–84 (2014). https://doi.org/10.1007/s11128-013-0708-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-013-0708-4