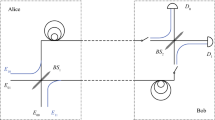
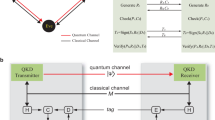
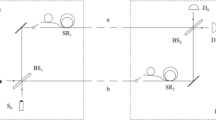
Abstract
In quantum key distribution (QKD), the information theoretically secure authentication is necessary to guarantee the integrity and authenticity of the exchanged information over the classical channel. In order to reduce the key consumption, the authentication scheme with key recycling (KR), in which a secret but fixed hash function is used for multiple messages while each tag is encrypted with a one-time pad (OTP), is preferred in QKD. Based on the assumption that the OTP key is perfect, the security of the authentication scheme has be proved. However, the OTP key of authentication in a practical QKD system is not perfect. How the imperfect OTP affects the security of authentication scheme with KR is analyzed thoroughly in this paper. In a practical QKD, the information of the OTP key resulting from QKD is partially leaked to the adversary. Although the information leakage is usually so little to be neglected, it will lead to the increasing degraded security of the authentication scheme as the system runs continuously. Both our theoretical analysis and simulation results demonstrate that the security level of authentication scheme with KR, mainly indicated by its substitution probability, degrades exponentially in the number of rounds and gradually diminishes to zero.






Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, pp. 175–179 (1984)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121–3124 (1992)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283, 2050–2056 (1999)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441–444 (2000)
Kimura, T., Nambu, Y., Hatanaka, T., Tomita, A., Kosaka, H., Nakamura, K.: Single-photon interference over 150 km transmission using silica-based integrated-optic interferometers for quantum cryptography. Jpn. J. Appl. Phys. 43, L1217 (2004)
Rosenberg, D., Harrington, J.W., Rice, P.R., Hiskett, P.A., Peterson, C.G., Hughes, R.J., Lita, A.E., Nam, S.W., Nordholt, J.E.: Long-distance decoy-state quantum key distribution in optical fiber. Phys. Rev. Lett. 98, 010503 (2007)
Walenta, N., Burg, A., Caselunghe, D., Constantin, J., Gisin, N., Guinnard, O., Houlmann, R., Junod, P., Korzh, B., Kulesza, N., Legr, M., Lim, C.C.W., Lunghi, T., Monat, L., Portmann, C., Soucarros, M., Trinkler, P., Trolliet, G., Vannel, F., Zbinden, H.: A fast and versatile QKD system with hardware key distillation and wavelength multiplexing. New J. Phys. 16, 013047 (2014)
Gilbert, E.N., Mac Williams, F.J., Sloane, N.J.A.: Codes which detect deception. Bell Syst. Tech. J. 53, 405–424 (1974)
Carter, J.L., Wegman, M.N.: Universal classes of hash functions. J. Comput. Syst. Sci. 18, 143–154 (1979)
Wegman, M.N., Carter, J.L.: New hash functions and their use in authentication and set equality. J. Comput. Syst. Sci. 22, 265–279 (1981)
Stinson, D.R.: Universal hashing and authentication codes. Des. Codes Cryptogr. 4, 369–380 (1994)
Atici, M., Stinson, D.R.: Universal hashing and multiple authentication. In: Annual International Cryptology Conference, 1109, pp. 16–30. Springer, Berlin, Heidelberg (1996)
Abidin, A.: On security of universal hash function based multiple authentication. In: International Conference on Information and Communications Security, 7618, pp. 303–310. Springer, Berlin, Heidelberg (2012)
Portmann, C.: Key recycling in authentication. IEEE Trans. Inf. Theory 60, 4383–4396 (2014)
Abidin, A., Larsson, J. Å.: Security of authentication with a fixed key in quantum key distribution. arXiv preprint (2011)
Zhou, C., Bao, W.-S., et al.: Key-leakage evaluation of authentication in quantum key distribution with finite resources. Quantum Inf. Process. 13, 935–955 (2014)
Bennett, C.H., Brassard, G., Crépeau, C., Maurer, U.M.: Generalized privacy amplification. Trans. Inf. Theory 41, 1915–1923 (1995)
Ben-Or, M., Horodecki, M., Leung, D.W., et al.: The universal composable security of quantum key distribution. In: Theory of Cryptography Conference, 3378, pp. 386–406. Springer, Berlin, Heidelberg (2005)
Stinson, D.R.: Cryptography Theory and Practice, 3rd edn. CRC Press, Boca Raton (2009)
Gottesman, D., Lo, H.K., Lutkenhaus, N., et al.: Security of quantum key distribution with imperfect devices. Quantum Inf. Comput. 4, 325–360 (2004)
Acknowledgments
This work is supported by the National Natural Science Foundation of China (Grant Numbers: 61471141, 61361166006, 61301099), Fundamental Research Funds for the Central Universities (Grant Number: HIT. KISTP. 201416).
Author information
Authors and Affiliations
Corresponding author
Appendix: Estimation of the number of uncertain hash functions
Appendix: Estimation of the number of uncertain hash functions
Based on the information leakage of OTP key in the ith round of authentication, Eve can sift out a subset \({{\mathcal{H}_i}}\) of size \(n_0\) from \(\mathcal{H}\). After i rounds, the set of uncertain hash functions is decreased to \(S_i=\cap _{j = 1}^{i}{\mathcal{H}_j}\). Let \({X_i} = \left| S_i\right| - 1\), indicating the number of false hash functions. Suppose \({X_{i - 1}} = n_{i-1}\), the probability of \({X_i} = j\) satisfies the hypergeometrical distribution [15], i.e.,
According to Eq. 11, the expected value of \(X_i\) on the condition that \(X_{i-1}=n_{i-1}\) can be deducted as Eq. 12.
Let \(\frac{{{n_0} - 1}}{{\left| \mathcal{H} \right| - 1}} = \eta \), \(E({X_i}|{X_{i - 1}} = {n_{i - 1}}) = \eta \times {n_{i - 1}}\). Consequently, the value of \(X_i\) can be estimated as Eq. 13 according to the law of total probability.
Therefore, the value of \(Y_i\) can be estimated as Eq. 14
Rights and permissions
About this article
Cite this article
Li, Q., Zhao, Q., Le, D. et al. Study on the security of the authentication scheme with key recycling in QKD. Quantum Inf Process 15, 3815–3831 (2016). https://doi.org/10.1007/s11128-016-1347-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-016-1347-3