Abstract
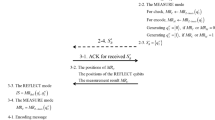
Zhang et al. (Quantum Inf Process 16:117, 2017. https://doi.org/10.1007/s11128-017-1573-3) proposed a semiquantum secure direct communication (SQSDC) using Einstein–Podolsky–Rosen pairs. However, as shown in this study, an eavesdropper can reveal the sender’s secret message by performing an intercept-and-resend attack. Furthermore, an eavesdropper can also launch a modification attack to modify the sender’s secret message without being detected. Without considering these security issues, the SQSDC protocol could fail at providing the secret message. Thus, an improvement is proposed to circumvent these problems and to improve the qubit efficiency from 10 to 17%.
Similar content being viewed by others
References
Long, G., Liu, X.: Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 65(3), 032302 (2002)
Beige, A., Englert, B.G., Kurtsiefer, C., Weinfurter, H.: Secure communication with a publicly known key. Acta Phys. Pol. A 101(3), 357–368 (2002)
Boström, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89(18), 187902 (2002)
Deng, F.-G., Long, G., Liu, X.-S.: Two-step quantum direct communication protocol using the Einstein–Podolsky–Rosen pair block. Phys. Rev. A 68(4), 042317 (2003)
Zhang, Z.J., Man, Z.X., Li, Y.: Improving Wojcik’s eavesdropping attack on the ping-pong protocol. Phys. Lett. A 333(1–2), 46–50 (2004)
Zhang, Z.J., Li, Y., Man, Z.X.: Improved Wojcik’s eavesdropping attack on ping-pong protocol without eavesdropping-induced channel loss. Phys. Lett. A 341(5–6), 385–389 (2005)
Wang, C., Deng, F.G., Long, G.L.: Multi-step quantum secure direct communication using multi-particle Green–Horne–Zeilinger state (vol 253, pg 15, 2005). Opt. Commun. 262(1), 134 (2006)
Zhu, A.D., Xia, Y., Fan, Q.B., Zhang, S.: Secure direct communication based on secret transmitting order of particles. Phys. Rev. A 73(2), 022338 (2006)
Zhang, Z.J., Jun, L., Liu, Y.M., Cao, H.J., Shi, S.H.: Revisiting quantum secure direct communication with W state. Chin. Phys. Lett. 23(10), 2652–2655 (2006)
Deng, F.-G., Li, X.-H., Li, C.-Y., Zhou, P., Zhou, H.-Y.: Eavesdropping on the ‘ping-pong’ quantum communication protocol freely in a noise channel. Chin. Phys. 16(2), 277 (2007)
Li, X.-H., Li, C.-Y., Deng, F.-G., Zhou, P., Liang, Y.-J., Zhou, H.-Y.: Quantum secure direct communication with quantum encryption based on pure entangled states. Chin. Phys. 16(8), 2149 (2007)
Zhang, Z.J., Yuan, H., Liu, Y.M., Zhang, W.: Eavesdropping on quantum secure direct communication with W state in noisy channel. Commun. Theor. Phys. 49(1), 103–106 (2008)
Yang, C.-W., Hwang, T.: Improved QSDC protocol over a collective-dephasing noise channel. Int. J. Theor. Phys. 51(12), 3941–3950 (2012)
Yang, C.-W., Tsai, C.-W., Hwang, T.: Fault tolerant deterministic quantum communications using GHZ states over collective-noise channels. Quantum Inf. Process. 12(9), 3043–3055 (2013)
Hwang, T., Luo, Y.-P., Yang, C.-W., Lin, T.-H.: Quantum authencryption: one-step authenticated quantum secure direct communications for off-line communicants. Quantum Inf. Process. 13(4), 925–933 (2014)
Deng, F.-G., Long, G.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 69(5), 052319 (2004)
Wang, C., Deng, F.-G., Li, Y.-S., Liu, X.-S., Long, G.L.: Quantum secure direct communication with high-dimension quantum superdense coding. Phys. Rev. A 71(4), 044305 (2005)
Yang, Y., Wen, Q.: Threshold quantum secure direct communication without entanglement. Sci. China Ser. G 51(2), 176–183 (2008)
Kang, G.D., Fang, M.F.: A scheme to share information via employing discrete algorithm to quantum states. Commun. Theor. Phys. 55(2), 239–243 (2011)
Hu, J.-Y., Yu, B., Jing, M.-Y., Xiao, L.-T., Jia, S.-T., Qin, G.-Q., Long, G.-L.: Experimental quantum secure direct communication with single photons. Light Sci. Appl. 5, e16144 (2016)
Zhang, W., Ding, D.-S., Sheng, Y.-B., Zhou, L., Shi, B.-S., Guo, G.-C.: Quantum secure direct communication with quantum memory. Phys. Rev. Lett. 118(22), 220501 (2017)
Zhu, F., Zhang, W., Sheng, Y., Huang, Y.: Experimental long-distance quantum secure direct communication. Sci. Bull. 62(22), 1519–1524 (2017)
Qi, R., Sun, Z., Lin, Z., Niu, P., Hao, W., Song, L., Huang, Q., Gao, J., Yin, L., Long, G.-L.: Implementation and security analysis of practical quantum secure direct communication. Light Sci. Appl. 8(1), 22 (2019)
Niu, P.-H., Zhou, Z.-R., Lin, Z.-S., Sheng, Y.-B., Yin, L.-G., Long, G.-L.: Measurement-device-independent quantum communication without encryption. Sci. Bull. 63(20), 1345–1350 (2018)
Zhou, Z.-R., Sheng, Y.-B., Niu, P.-H., Yin, L.-G., Long, G.-L.: Measurement-device-independent quantum secure direct communication. arXiv:1805.07228 (2018)
Gao, Z., Li, T., Li, Z.: Long-distance measurement-device–independent quantum secure direct communication. EPL 125(4), 40004 (2019)
Lum, D.J., Howell, J.C., Allman, M.S., Gerrits, T., Verma, V.B., Nam, S.W., Lupo, C., Lloyd, S.: Quantum enigma machine: Experimentally demonstrating quantum data locking. Phys. Rev. A 94(2), 022315 (2016)
Shapiro, J.H., Boroson, D.M., Dixon, P.B., Grein, M.E., Hamilton, S.A.: Quantum low probability of intercept. J. Opt. Soc. Am. B 36(3), B41–B50 (2019)
Zou, X., Qiu, D.: Three-step semiquantum secure direct communication protocol. Sci. China Phys. Mech. 57(9), 1696–1702 (2014)
Luo, Y.-P., Hwang, T.: Authenticated semi-quantum direct communication protocols using Bell states. Quantum Inf. Process. 15(2), 947–958 (2016)
Gu, J., Lin, P.-H., Hwang, T.: Double C-NOT attack and counterattack on ‘Three-step semi-quantum secure direct communication protocol’. Quantum Inf. Process. 17(7), 182 (2018)
Yan, L., Sun, Y., Chang, Y., Zhang, S., Wan, G., Sheng, Z.: Semi-quantum protocol for deterministic secure quantum communication using Bell states. Quantum Inf. Process. 17(11), 315 (2018)
Sun, Y., Yan, L., Chang, Y., Zhang, S., Shao, T., Zhang, Y.: Two semi-quantum secure direct communication protocols based on Bell states. Mod. Phys. Lett. A 34(01), 1950004 (2018)
Zhang, M.-H., Li, H.-F., Xia, Z.-Q., Feng, X.-Y., Peng, J.-Y.: Semiquantum secure direct communication using EPR pairs. Quantum Inf. Process. 16(5), 117 (2017). https://doi.org/10.1007/s11128-017-1573-3
Deng, F.G., Li, X.H., Zhou, H.Y., Zhang, Z.J.: Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A 72(4), 044302 (2005)
Li, X.H., Deng, F.G., Zhou, H.Y.: Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A 74(5), 054302 (2006)
Cai, Q.Y.: Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A 351(1–2), 23–25 (2006)
Cai, Q.-Y.: The “ping-pong” protocol can be attacked without eavesdropping. Phys. Rev. Lett. 91(10), 109801(1) (2003)
Yang, C.-W., Hwang, T., Lin, T.-H.: Modification attack on QSDC with authentication and the improvement. Int. J. Theor. Phys. 52(7), 2230–2234 (2013)
Lin, T.-H., Yang, C.-W., Hwang, T.: Attacks and improvement on “quantum direct communication with mutual authentication”. Int. J. Theor. Phys. 53(2), 597–602 (2014)
Tsai, C.W., Hwang, T.: New deterministic quantum communication via symmetric W state. Opt. Commun. 283(21), 4397–4400 (2010)
Li, C.Y., Zhou, H.Y., Wang, Y., Deng, F.G.: Secure quantum key distribution network with Bell states and local unitary operations. Chin. Phys. Lett. 22(5), 1049–1052 (2005)
Lo, H.K.: Decoy state quantum key distribution. Int. J. Quantum Inf. 3, 143 (2005)
Lo, H.K., Ma, X.F., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94(23), 4 (2005)
Ma, X.F., Qi, B., Zhao, Y., Lo, H.K.: Practical decoy state for quantum key distribution. Phys. Rev. A 72(1), 15 (2005)
Xu, F.H., Xu, H., Lo, H.K.: Protocol choice and parameter optimization in decoy-state measurement-device-independent quantum key distribution. Phys. Rev. A 89(5), 11 (2014)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature 299(5886), 802–803 (1982)
Yang, C.-W., Hwang, T.: Quantum dialogue protocols immune to collective noise. Quantum Inf. Process. 12(6), 2131–2142 (2013)
Yang, C.-W., Hwang, T., Luo, Y.-P.: Enhancement on “quantum blind signature based on two-state vector formalism”. Quantum Inf. Process. 12(1), 109–117 (2013)
Acknowledgements
We would like to thank the anonymous reviewers and the editor for their very valuable comments, which greatly enhanced the clarity of this paper. This research was partially supported by the Ministry of Science and Technology, Taiwan, R.O.C. (Grant Nos. MOST 106-2218-E-039-002-MY3, MOST 107-2218-E-143-002-MY2, and MOST 107-2627-E-006-001) and China Medical University (Grant No. CMU107-N-11).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yang, CW., Tsai, CW. Intercept-and-resend attack and improvement of semiquantum secure direct communication using EPR pairs. Quantum Inf Process 18, 306 (2019). https://doi.org/10.1007/s11128-019-2429-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-019-2429-9