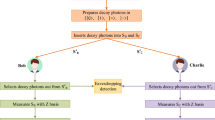
Abstract
The (k, n)-threshold quantum secret sharing scheme is an important and difficult field in quantum information processing and quantum cryptography. In this paper, the (k, n)-threshold quantum secret sharing scheme based on local operations and classical communication (LOCC-QSS) is investigated. Firstly, in order to effectively study the LOCC-QSS scheme, digital and graphical representations of judgement space are introduced creatively. These representations are simple and convenient. Secondly, an algorithm is designed to search optional states for any given k and n. For optional states, the unambiguous probability equals 0 when x participants cooperate (x < k). Thirdly, a method is proposed to decrease the guessing probability. Some schemes which are more secure than existing ones can be obtained further. Last but not least, the conditions of optimal LOCC-QSS schemes are given for the first time. Our research will be helpful for the development of LOCC-QSS scheme.





Similar content being viewed by others
References
Shamir, A.: How to share a secret. Commun. ACM 22, 612–613 (1979)
Blakley, G. R.: Safeguarding cryptographic keys. In: 1979 International Workshop on Managing Requirements Knowledge (MARK), pp. 313–317. IEEE, Montvale (1979)
Bennett, C. Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. In: Conf. on Computers, Systems and Signal Processing, pp. 175–179. IEEE, Bangalore (1984)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59, 1829 (1999)
Cleve, R., Gottesman, D., Lo, H.K.: How to share a quantum secret. Phys. Rev. Lett. 83, 648 (1999)
Singh, S.K., Srikanth, R.: Generalized quantum secret sharing. Phys. Rev. A 71, 012328 (2005)
Fortescue, B., Gour, G.: Reducing the quantum communication cost of quantum secret sharing. IEEE T. Inform. Theory 58, 6659–6666 (2012)
Pilaram, H., Eghlidos, T.: An efficient lattice based multi-stage secret sharing scheme. IEEE Trans. Depend Secure 14, 2–8 (2015)
Tavakoli, A., Herbauts, I., Żukowski, M., Bourennane, M.: Secret sharing with a single d-level quantum system. Phys. Rev. A 92, 030302 (2015)
Karimipour, V., Asoudeh, M.: Quantum secret sharing and random hopping: using single states instead of entanglement. Phys. Rev. A 92, 030301 (2015)
Markham, D., Sanders, B.C.: Graph states for quantum secret sharing. Phys. Rev. A 78, 042309 (2008)
Schmid, C., Trojek, P., Bourennane, M., Kurtsiefer, C., Żukowski, M., Weinfurter, H.: Experimental single qubit quantum secret sharing. Phys. Rev. Lett. 95, 230505 (2005)
Chen, Y.A., Zhang, A.N., Zhao, Z., Zhou, X.Q., Lu, C.Y., Peng, C.Z., Yang, T., Pan, J.W.: Experimental quantum secret sharing and third-man quantum cryptography. Phys. Rev. Lett. 95, 200502 (2005)
Lu, H., Zhang, Z., Chen, L.K., Li, Z.D., Liu, C., Li, L., Liu, L.L., Ma, X.F., Chen, Y.A., Pan, J.W.: Secret sharing of a quantum state. Phys. Rev. Lett. 117, 030501 (2016)
Lau, H.K., Weedbrook, C.: Quantum secret sharing with continuous-variable cluster states. Phys. Rev. A 88, 042313 (2013)
Kogias, I., Xiang, Y., He, Q., Adesso, G.: Unconditional security of entanglement-based continuous-variable quantum secret sharing. Phys. Rev. A 95, 012315 (2017)
Cao, H., Ma, W.P.: (t, n) threshold quantum state sharing scheme based on linear equations and unitary operation. IEEE Photonics J. 9, 1–7 (2017)
Lu, C., Miao, F., Hou, J., Meng, K.: Verifiable threshold quantum secret sharing with sequential communication. Quantum Inf. Process. 17, 310 (2018)
Song, X.L., Liu, Y.B., Deng, H.Y., Xiao, Y.G.: (t, n) threshold d-level quantum secret sharing. Sci. Rep.-UK 7, 6366 (2017)
Qin, H., Dai, Y.: An efficient (t, n) threshold quantum secret sharing without entanglement. Mod. Phys. Lett. B 30, 1650138 (2016)
Lai, H., Zhang, J., Luo, M. X., Pan, L., Pieprzyk, J., Xiao, F., Orgun, M. A.: Hybrid threshold adaptable quantum secret sharing scheme with reverse Huffman-Fibonacci-tree coding. Sci. Rep.-UK 6, 31350 (2016)
Rahaman, R., Parker, M.G.: Quantum scheme for secret sharing based on local distinguishability. Phys. Rev. A 91, 022330 (2015)
Yang, Y.H., Gao, F., Wu, X., Qin, S.J., Zuo, H.J., Wen, Q.Y.: Quantum secret sharing via local operations and classical communication. Sci. Rep.-UK 5, 16967 (2015)
Wang, J., Li, L., Peng, H., Yang, Y.: Quantum-secret-sharing scheme based on local distinguishability of orthogonal multiqudit entangled states. Phys. Rev. A 95, 022320 (2017)
Bai, C.M., Li, Z.H., Liu, C.J., Li, Y.M.: Quantum secret sharing using orthogonal multiqudit entangled states. Quantum Inf. Process. 16, 304 (2017)
Liu, C.J., Li, Z.H., Bai, C.M., Si, M.M.: Quantum-Secret-Sharing Scheme based on local distinguishability of orthogonal Seven-Qudit entangled states. Int. J. Theor. Phys. 57, 428–442 (2018)
Bae, J., Kwek, L.C.: Quantum state discrimination and its applications. J. Phys. A-Math. Theor. 48, 083001 (2015)
Hardy, G.H., Ramanujan, S.: Asymptotic formulaæ in combinatory analysis. P. Lond. Math. Soc. 2, 75–115 (1918)
Acknowledgements
This work was supported by the National Key R&D Program of China (2017YFB0802703), NSFC (Grant Nos. 61671087, 61272514, 61170272, 61003287, U1836205), the Fok Ying Tong Education Foundation (Grant No. 131067), the Major Scientific and Technological Special Project of Guizhou Province (Grant No. 20183001), the Foundation of Guizhou Provincial Key Laboratory of Public Big Data (Grant Nos. 2018BDKFJJ016, 2019BDKFJJ014), the Foundation of State Key Laboratory of Public Big Data (Grant No. 2018BDKFJJ018) and the Fundamental Research Funds for the Central Universities (Grant Nos. 2019XD-A02, 2020RC38) and sponsored by CCF-Tencent Open Fund WeBank Special Funding (CCF-WebankRAGR20180104).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix: The pseudo-code of our searching algorithm
Appendix: The pseudo-code of our searching algorithm

Rights and permissions
About this article
Cite this article
Dou, Z., Xu, G., Chen, XB. et al. Searching for optimal quantum secret sharing scheme based on local distinguishability. Quantum Inf Process 19, 368 (2020). https://doi.org/10.1007/s11128-020-02809-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-020-02809-z