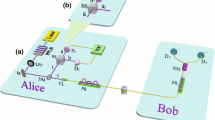
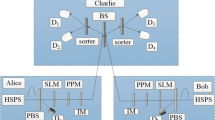
Abstract
Decoy-state method has been widely employed in the quantum key distribution (QKD), since it can not only solve photon-number-splitting attacks but also substantially improve the QKD performance. In conventional three-intensity decoy-state proposal, one not only needs to randomly modulate light sources to different intensities, but also has to prepare them into different bases, which may cost a lot of random numbers in practical applications. Here, we propose a simple decoy-state scheme with biased basis choices where the decoy pulses are only prepared in X basis. Through this way, it can save cost of random numbers and further simplify the electronic control system. Moreover, we carry out corresponding proof-of-principle demonstration. By incorporating with lower-loss asymmetric Mach–Zehnder interferometers and superconducting single-photon detectors, we can obtain a secret key rate of 1.65 kbps at 201 km and 19.5 bps at 280 km coiled optical fibers, respectively, showing very promising applications in future quantum communications.





Similar content being viewed by others
References
Ekert, A.-K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661 (1991)
Lo, H.-K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283, 2050 (1999)
Mayers, D.: Unconditional security in quantum cryptography. J. ACM 48, 351 (2001)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, pp. 175–179. IEEE, New York (1984)
Bruss, D.: Optimal eavesdropping in quantum cryptography with six states. Phys. Rev. Lett. 81, 3018 (1998)
Laing, A., Scarani, V., Rarity, J.-G., et al.: Reference-frame-independent quantum key distribution. Phys. Rev. A 82, 012304 (2010)
Lo, H.-K., Marcos, C., Bing, Q.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012)
Lucamarini, M., Dynesand, Z.-L., Shields, A.-J.: Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 557, 400 (2018)
Sasaki, T., Yamamoto, Y., Koashi, M.: Practical quantum key distribution protocol without monitoring signal disturbance. Nature 509, 475 (2014)
Peev, M., et al.: The SECOQC quantum key distribution network in Vienna. New J. Phys. 11, 075001 (2009)
Sasaki, M., et al.: Field test of quantum key distribution in the Tokyo QKD network. Opt. Express 19, 10387 (2011)
Wang, S., et al.: Field and long-term demonstration of a wide area quantum key distribution network. Opt. Express 22, 21739 (2014)
Stucki, D., et al.: Long-term performance of the SwissQuantum quantum key distribution network in a field environment. Opt. Lett. 13, 123001 (2011)
Dynes, J.-F., et al.: Stability of high bit rate quantum key distribution on installed fiber. Opt. Express 20, 16339 (2012)
Dixon, A.-R., et al.: High speed prototype quantum key distribution system and long term field trial. Opt. Express 23, 7583 (2015)
Brassard, G., Lutkenhaus, N., Mor, T., Sanders, B.-C.: Limitations on practical quantum cryptography. Phys. Rev. Lett. 85, 1330 (2000)
Lutkenhaus, N., Jahma, M.: Quantum key distribution with realistic states: photon-number statistics in the photon-number splitting attack. New J. Phys. 4, 44 (2002)
Wang, X.-B.: Beating the photon-number-splitting attack in practical quantum crytography. Phys. Rev. Lett. 94, 230503 (2005)
Lo, H.-K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005)
Frohlich, B., et al.: Long-distance quantum key distribution secure against coherent attacks. Optica 4, 163 (2017)
Boaron, A., et al.: Secure quantum key distribution over 421 km of optical fiber. Phys. Rev. Lett. 121, 190502 (2018)
Wang, Q., et al.: Experimental decoy-state quantum key distribution with a sub-poissionian heralded single-photon source. Phys. Rev. Lett. 100, 090501 (2008)
Zhang, C.-H., et al.: Proof-of-principle demonstration of parametric down-conversion source-based quantum key distribution over 40 dB channel loss. Opt. Express 26, 25921 (2008)
Zhou, Y.-H., Yu, Z.-.W., Wang, X.-B.: Tightened estimation can improve the key rate of measurement-device-independent quantum key distribution by more than 100%. Phys. Rev. A 89, 052325 (2014)
Fung, C.-H.F., Ma, X.-F., Chau, H.F.: Practical issues in quantum-key-distribution postprocessing. Phys. Rev. A 81, 012318 (2010)
Zhang, C.-H., Luo, S.-L., Guo, G.-C., Wang, Q.: Biased three-intensity decoy-state scheme on the measurement-device-independent quantum key distribution using heralded single-photon sources. Opt. Express 26, 4219 (2018)
Wang, X.-B., Yang, L., Peng, C.-Z., Pan, J.-W.: Decoy-state quantum key distribution with both source errors and statistical fluctuations. New J. Phys. 11, 075006 (2009)
Acknowledgements
The authors gratefully appreciate Hengtong Optic-Electric Co., Ltd., for providing lower-loss fibers. We gratefully acknowledge the financial support from the National Key R&D Program of China (Nos. 2018YFA0306400, 2017YFA0304100), the National Natural Science Foundation of China (Nos. 11774180, 61590932), the Leading-edge technology Program of Jiangsu Natural Science Foundation (BK20192001), and the Postgraduate Research & Practice Innovation Program of Jiangsu Province (SJCX19_0250).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
In this appendix, we will give the derivation process of Eqs. (1) and (2).
For the WCS, the probability of finding an i-photon state with intensity \(\xi \)\((\xi \in \{ \mu , \nu \})\) is given by: \(P_{\xi }(i) = \frac{\xi ^{i}}{i!}e^{-\xi }\). Then, we have
For any \(i \ge 2\), when \(\mu>\nu >0\), \(\frac{\mu }{\nu }>1\), therefore, the following inequalities hold
The Proof for Eq. (1) of the main text is done.
The gains of signal and decoy states can be written as:
With Eqs. (A3) and (A4), it is easy to get
Considering the conditions in Eq. (A2), we can get the following inequality:
It is easy to reach
The proof for Eq. (2) of the main text is finished.
Rights and permissions
About this article
Cite this article
Wu, WZ., Zhu, JR., Ji, L. et al. Proof-of-principle demonstration of decoy-state quantum key distribution with biased basis choices. Quantum Inf Process 19, 341 (2020). https://doi.org/10.1007/s11128-020-02852-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-020-02852-w