Abstract
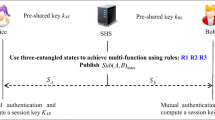
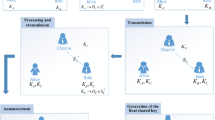
Semi-quantum cryptography was proposed to deal with the issue that some players are only able to perform classical operations, thus alleviating the cost of its implementation. For achieving the better universal setting for current environment, we propose a mutual authenticated semi-quantum-honest key agreement scheme with three-particle entangled states in cross-domain setting, which means in different realm’s client can get the session key by his/her own server helping, while anyone else cannot get the session key except for the two clients. In addition, we assume that there is no fully trusted party and that all parties are semi-honest. More important, by the third party’s helping with three-particle entangled states and the four rules, the third party, two servers and two clients can authenticate each other. The proposed scheme has the properties of completeness, information-theoretic security, non-repudiation and unforgeability. On the other hand, our scheme is more efficient than the similar schemes.



Similar content being viewed by others
References
Bennett, C.H., Brassard. G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, p. 175. IEEE, New York (1984)
Xin, X., Wang, Z., He, Q., Yang, Q., Li, F.: New public-key quantum signature scheme with quantum one-way function[J]. Int. J. Theor. Phys. 58(1), 10–21 (2019)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances[J]. Science 283(5410), 2050–2056 (1999)
Curty, M., Lewenstein, M., Lutkenhaus, N.: Entanglement as a precondition for secure quantum key distribution[J]. Phys. Rev. Lett. 92(21), 217903 (2004)
Hwang, T., Lee, K.C., Li, C.M.: Provably secure three-party authenticated quantum key distribution protocols. IEEE Trans. Dependable Secure Comput. 4(1), 71 (2007)
Guan, D.J., Wang, Y.-J., Zhuang, E.S.: A practical protocol for three-party authenticated quantum key distribution. Quantum Inf. Process. 13, 2355–2374 (2014)
Cao, G., Chen, C., Jiang, M.: A scalable and flexible multi-user semi-quantum secret sharing. In: ICTCE 2018 Proceedings of the 2nd International Conference on Telecommunications and Communication Engineering. Pp. 28–32
Clancy, T. C., McGwier, R. W.: TUTORIAL: Post-quantum cryptography and 5G security, May 15–17, 2019, ACM ISBN 978-1-4503-6726-4/19/05, https://doi.org/10.1145/3317549.3324882
Prousalis, K., Konofaos, N.: Improving the sequence alignment method by quantum multi-pattern recognition. In: Proceeding SETN ‘18, Proceedings of the 10th Hellenic Conference on Artificial Intelligence, No. 50, July 09–12, 2018
Nguyen, B.A.: Quantum dialogue. Phys. Lett. A 328(1), 6–10 (2004)
Man, Z.-X., Xia, Y.-J.: Controlled bidirectional quantum direct communication by using a GHZ state. Chin. Phys. Lett. 23(7), 1680 (2006)
Xia, Y., et al.: Controlled secure quantum dialogue using a pure entangled GHZ states. Commun. Theor. Phys. 48(5), 841 (2007)
Xia, Y.-J., Man, Z.-X.: Controlled quantum n-party simultaneous direct communication. Commun. Theor. Phys. 48(1), 79 (2007)
Ye, T.-Y., Jiang, L.-Z.: Improvement of controlled bidirectional quantum direct communication using a GHZ state. Chin. Phys. Lett. 30(4), 040305 (2013)
Chang, C.-H., et al.: Intercept-and-resend attack on controlled bidirectional quantum direct communication and its improvement. Quantum Inf. Process. 14(9), 3515–3522 (2015)
Kao, S.-H., Hwang, T.: Controlled quantum dialogue robust against conspiring users. Quantum Inf. Process. 15(10), 4313–4324 (2016)
Kao, S.-H., Hwang, T.: Controlled quantum dialogue using cluster states. Quantum Inf. Process. 16(5), 139 (2017)
Wang, M.-M., Gong, L.-M., Shao, L.-H.: Efficient semiquantum key distribution without entanglement. Quantum Inf. Process. 18, 260 (2019). https://doi.org/10.1007/s11128-019-2378-3
Jiang, W., Clifton, C.: A secure distributed framework for achieving k-anonymity. Int. J. Very Large Data Bases 15(4), 316–333 (2006)
Schwinger, J.: Unitary operator bases. Proc. Natl. Acad. Sci. U.S.A. 46(4), 570 (1960)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. of Modern Phys. 74, 145–190 (2002)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature 299, 802–803 (1992)
Li, Q., Chan, W.-H., Long, D.-Y.: Semiquantum secret sharing using entangled states. Phys. Rev. A 82(2), 022303 (2010)
Boyer, M., Gelles, R., Kenigsberg, D., Mor, T.: Semiquantum key distribution. Phys. Rev. A 79, 032341 (2009)
Yang, L., Yang, B., Pan, J.: Quantum public-key encryption protocols with information-theoretic security. In: Proceedings of SPIE-The International Society for Optical Engineering, p. 8440, IEEE, New York (2010)
Yang, L., Xiang, C., Li, B.: Quantum probabilistic encryption scheme based on conjugate coding. China Commun. 10(2), 19–26 (2013)
Acknowledgements
This work was supported by the Liaoning Provincial Natural Science Foundation of China (Grant No. 2019-MS-286), and Basic Scientific Research Project of Liaoning Provincial Department of Education (2020), and Shenyang Jianzhu University's Educational Science Research Project in 2019.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhu, D., Wang, X. & Zhu, H. Semi-quantum-honest key agreement scheme with three-particle entangled states in cross-realm setting. Quantum Inf Process 19, 376 (2020). https://doi.org/10.1007/s11128-020-02879-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-020-02879-z