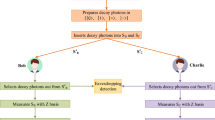
Abstract
The four-qubit cluster state has a more robust entanglement property than other four-particle states. Empowered by the 4-qubit cluster state and Bell state entanglement, two quantum secret sharing (QSS) protocols are proposed in this paper. The first protocol is with the quantum users who can perform Bell measurement. The second protocol is with classical users who only can perform Z basis measurement and is also known as semi-quantum secret sharing (SQSS). Moreover, the security analysis shows the proposed QSS and SQSS protocols can achieve full security and resist some common eavesdropping attacks, such as interception attack, measure-resend attack, entanglement-measure attack, and Trojan horse attack. Meanwhile, the efficiency comparison shows that the proposed protocols are also efficient than other similar protocols with relate to the qubit efficiency.



Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. arXiv preprint arXiv:2003.06557 (2020)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68(21), 3121 (1992)
Li, J., Li, N., Li, L.L., Wang, T.: One step quantum key distribution based on EPR entanglement. Sci. Rep. 6(1), 1–10 (2016)
Li, J., Li, H.J., Wang, N., Li, C.Y., Hou, Y.Y., Chen, X.B., Yang, Y.G.: A quantum key distribution protocol based on the EPR Pairs and its simulation. Mob. Netw. Appl. 26, 620–628 (2021)
Deng, F.G., Long, G.L.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 69(5), 052319 (2004)
Li, T., Long, G.L.: Quantum secure direct communication based on single-photon Bell-state measurement. New J. Phys. 22(6), 063017 (2020)
Yang, Y.G., Wen, Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 42(5), 055305 (2009)
Li, C., Chen, X.B., Li, H., et al.: Efficient quantum private comparison protocol based on the entanglement swapping between four-qubit cluster state and extended Bell state. Quantum Inf. Process. 18(5), 1–12 (2019)
Ye, C.Q., Li, J., Cao, Z.W.: A class of protocols for multi-party quantum private comparison based on traveling mode. Quantum Inf. Process. 20(2), 1–18 (2021)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing[J]. Phys. Rev. A 59(3), 1829 (1999)
Gottesman, D.: Theory of quantum secret sharing. Phys. Rev. A 61(4), 042311 (2000)
Zhou, N., Zeng, G., Xiong, J.: Quantum key agreement protocol. Electron. Lett. 40(18), 1149–1150 (2004)
Wang, W., Zhou, B.M., Zhang, L.: The three-party quantum key agreement protocol with quantum fourier transform. Int. J. Theor. Phys. 59, 1944–1955 (2020)
Yu, K.F., Yang, C.W., Liao, C.H., et al.: Authenticated semi-quantum key distribution protocol using Bell states. Quantum Inf. Process. 13(6), 1457–1465 (2014)
Hajji, H., El Baz, M.: Qutrit-based semi-quantum key distribution protocol. Quantum Inf. Process. 20(1), 1–25 (2021)
Gu, J., Lin, P., Hwang, T.: Double C-NOT attack and counterattack on Three-step semi-quantum secure direct communication protocol. Quantum Inf. Process. 17(7), 1–8 (2018)
Rong, Z., Qiu, D., Zou, X.: Semi-quantum secure direct communication using entanglement. Int. J. Theor. Phys. 59(6), 1807–1819 (2020)
Jiang, L.Z.: Semi-quantum private comparison based on Bell states. Quantum Inf. Process. 19(6), 1–21 (2020)
Ye, C.Q., Li, J., Chen, X.B., et al.: Efficient semi-quantum private comparison without using entanglement resource and pre-shared key. Quantum Inf. Process. 20(8), 1–19 (2021)
Zhou, N.R., Xu, Q.D., Du, N.S., et al.: Semi-quantum private comparison protocol of size relation with d-dimensional Bell states. Quantum Inf. Process. 20(3), 1–15 (2021)
Li, Q., Chan, W.H., Long, D.Y.: Semi-quantum secret sharing using entangled states. Phys. Rev. A 82(2), 022303 (2010)
Ye, C.Q., Ye, T.Y.: Circular semi-quantum secret sharing using single particles. Commun. Theor. Phys. 70(6), 661 (2018)
Tian, Y., Li, J., Chen, X.B., et al.: An efficient semi-quantum secret sharing protocol of specific bits. Quantum Inf. Process. 20(6), 1–11 (2021)
Yin, A., Chen, T.: Authenticated semi-quantum secret sharing based on GHZ-type states. Int. J. Theor. Phys. 60(1), 265–273 (2021)
Liu, W.J., Chen, Z.Y., Ji, S., et al.: Multi-party semi-quantum key agreement with delegating quantum computation. Int. J. Theor. Phys. 56(10), 3164–3174 (2017)
Li, H.H., Gong, L.H., Zhou, N.R.: New semi-quantum key agreement protocol based on high-dimensional single-particle states. Chinese Phys. B 29(11), 110304 (2020)
Guo, G.P., Guo, G.C.: Quantum secret sharing without entanglement. Phys. Lett. A 310(4), 247–251 (2003)
Hsieh, C.R., Tasi, C.W., Hwang, T.: Quantum secret sharing using GHZ-like state. Commun. Theor. Phys. 54(6), 1019 (2010)
Grice, W.P., Qi, B.: Quantum secret sharing using weak coherent states. Phys. Rev. A 100(2), 022339 (2019)
Liao, Q., Liu, H., Zhu, L., et al.: Quantum secret sharing using discretely modulated coherent states. Phys. Rev. A 103(3), 032410 (2021)
Lance, A.M., Symul, T., Bowen, W.P., Sanders, B.C., Lam, P.K.: Tripartite quantum state sharing. Phys. Rev. Lett. 92(17), 177903 (2004)
Cao, H., Ma, W.P.: (t, n) Threshold quantum state sharing scheme based on linear equations and unitary operation. IEEE Photonics J. 9(1), 1–7 (2017)
Qin, H., Tso, R.: Threshold quantum state sharing based on entanglement swapping. Quantum Inf. Process. 17(6), 1–11 (2018)
Lie, S.H., Choi, S., Jeong, H.: Min-entropy as a resource for one-shot private state transfer, quantum masking, and state transition. Phys. Rev. A 103(4), 042421 (2021)
Li, L., Qiu, D., Mateus, P.: Quantum secret sharing with classical Bobs. J. Phys. A Math. Theor. 46(4), 045304 (2013)
Xie, C., Li, L., Qiu, D.: A novel semi-quantum secret sharing scheme of specific bits. Int. J. Theor. Phys. 54(10), 3819–3824 (2015)
Yin, A., Wang, Z., Fu, F.: A novel semi-quantum secret sharing scheme based on Bell states. Modern Phys. Lett. B 31(13), 1750150 (2017)
Yin, A.H., Tong, Y.: A novel semi-quantum secret sharing scheme using entangled states. Modern Phys. Lett. B 32(22), 1850256 (2018)
Li, Z., Li, Q., Liu, C., et al.: Limited resource semiquantum secret sharing. Quantum Inf. Process. 17(10), 1–11 (2018)
Cao, G., Chen, C., Jiang, M.: A scalable and flexible multi-user semi-quantum secret sharing. Proceedings of the 2nd International Conference on Telecommunications and Communication Engineering. 28-32, (2018)
Tsai, C.W., Yang, C.W., Lee, N.Y.: Semi-quantum secret sharing protocol using W-state. Modern Phys. Lett. A 34(27), 1950213 (2019)
Briegel, H.J., Raussendorf, R.: Persistent entanglement in arrays of interacting particles. Phys. Rev. Lett. 86(5), 910 (2001)
Boyer, M., Kenigsberg, D., Mor, T.: Quantum key distribution with classical bob. Phys. Rev. Lett. 99(14), 140501 (2007)
Krawec, W.O.: Security proof of a semi-quantum key distribution protocol. 2015 IEEE International Symposium on Information Theory (ISIT). IEEE, 686-690 (2015)
Acknowledgements
This work was supported by the National Natural Science Foundation of China under Grant 92046001, 61962009, the Fundamental Research Funds for the Central Universities under Grant 2019XD-A02, the Doctor Scientific Research Fund of Zhengzhou University of Light Industry.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Li, C., Ye, C., Tian, Y. et al. Cluster-state-based quantum secret sharing for users with different abilities. Quantum Inf Process 20, 385 (2021). https://doi.org/10.1007/s11128-021-03327-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-021-03327-2