Abstract
Based on quantum asymmetric cryptosystem, a public-key quantum signature for classical messages is proposed. In our scheme, the private key is randomly chosen by signer, and the public key is generated by the trusted key generator using the quantum one-way function. The signer signs a message with the private key, while the verifier can use the public key to verify the quantum signature without the help of third party. The signer’s key pair can be reused. Hence, our scheme can simplify the key management of the quantum signature system. Security analysis results show that the proposed scheme satisfies unforgeability and non-repudiation. All the algorithms in our scheme are public. Compared to similar schemes, ours is relatively more secure and can be easily applied to practical scenarios.




Similar content being viewed by others
Data availability
All data generated or analyzed during this study are included in this submitted article.
References
Chen,T.H., Xu X.G.: Digital signature in the application of e-commerce security. In: 2010 International Conference on E-Health Networking Digital Ecosystems and Technologies, pp. 366–369. IEEE (2010)
Wang, J.H., Liu, J.W., Li, X.H., Kou, W.D.: Fair e-payment protocol based on blind signature. J. China Univ. Posts Telecommun. 16(5), 114 (2009)
Tsang, P.P., Wei, V.K.: Short linkable ring signatures for e-voting, e-cash and attestation. In: International Conference on Information Security Practice and Experience, pp. 48–60. Springer, Berlin (2005)
Shor, P.W.: Algorithms for quantum computation: discrete logarithm and factoring. In: Proceedings of the 35th Annual Symposium on the Foundations of Computer Science, pp. 124–134. IEEE Computer Society Press (1994)
Zeng, G.H., Keitel, C.H.: Arbitrated quantum-signature scheme. Phys. Rev. A. 65(4), 042312 (2002)
Lee, H., Hong, C., Kim, H., Lim, J., Yang, H.J.: Arbitrated quantum signature scheme with message recovery. Phys. Lett. A. 321(5–6), 295–300 (2004)
Li, Q., Chan, W.H., Long, D.Y.: Arbitrated quantum signature scheme using Bell states. Phys. Rev. A 79(5), 054307 (2009)
Okamoto, T., Tanaka, K., Uchiyama, S.: Quantum public-key cryptosystems. In: Bellare, M. (ed.) Advances in Cryptology-CRYPTO 2000. LNCS, pp. 147–165. Springer, Berlin (2000)
Luo, M.X., Chen, X.B., Yun, D., Yang, Y.X.: Quantum public-key cryptosystem. Int. J. Theor. Phys. 51(3), 912 (2012)
Nikolopoulos, G.M.: Applications of single-qubit rotations in quantum public-key cryptography. Phys. Rev. A. 77(3), 032348 (2008)
Seyfarth, U., Nikolopoulos, G.M., Alber, G.: Symmetries and security of a quantum-public-key encryption based on single-qubit rotations. Phys. Rev. A. 85(2), 022342 (2012)
Nikolopoulos, G.M., Ioannou, L.M.: Deterministic quantum-public-key encryption: forward search attack and randomization. Phys. Rev. A. 79(4), 042327 (2009)
Yang, L., Yang, B., Pan, J.: Quantum public-key encryption protocols with information-theoretic security. Quantum Opt. II 8440, 84400E (2012)
Petzoldt, A., Szepieniec, A., Mohamed, M.S.E.: A practical multivariate blind signature scheme. In: International Conference on Financial Cryptography and Data Security, pp. 437–454. Springer, Cham (2017)
Chen, Y., Chou, J.S., Wang, L.C., Chou, Y.Y.: A publicly verifiable quantum blind signature scheme without entanglement based on asymmetric cryptography. Cryptol. ePrint Arch (2019)
Zhou, J., Zhou, Y., Niu, X., Yang, Y.: Quantum proxy signature scheme with public verifiability. Sci. China Phys. Mech. Astron. 54(10), 1828 (2011)
Chen, J., Ling, J., Ning, J., Panaousis, E., Loukas, G., Liang, K., Chen, J.: Post quantum proxy signature scheme based on the multivariate public key cryptographic signature. Int. J. Distrib. Sens. Netw. 16(4), 1550147720914775 (2020)
Xin, X., Wang, Z., Yang, Q., Li, F.: Identity-based quantum designated verifier signature. Int. J. Theor. Phys. 59(3), 918 (2020)
Xin, X., Ding, L., Li, C., Sang, Y., Yang, Q., Li, F.: Quantum public-key designated verifier signature. Quantum Inf. Process. 21(1), 33 (2022)
Gottesman, D., Chuang, I.: Quantum Digital Signatures. arXiv:quant-ph/0105032 (2001)
Kaushik, A., Ajit, K.D., Debasish, J.: A novel approach for simple quantum digital signature based on asymmetric quantum cryptography. Int. J. Appl. Innov. Eng. Manag. 2(6), 13 (2013)
Xin, X., Yang, Q., Li, F.: Quantum public-key signature scheme based on asymmetric quantum encryption with trapdoor information. Quantum Inf. Process. 19(8), 233 (2020)
Chen, F.L., Liu, W.F., Chen, S.G., Wang, Z.H.: Public-key quantum digital signature scheme with one-time pad private-key. Quantum Inf. Process. 17(1), 10 (2018)
Xin, X., Wang, Z., He, Q., Yang, Q., Li, F.: New public-key quantum signature scheme with quantum one-way function. Int. J. Theor. Phys. 58(10), 3282 (2019)
Xin, X., Wang, Z., Yang, Q.: Quantum signature scheme based on Hadamard and \(H_{\pi / 4}\) operators. Appl. Opt. 58(27), 7346 (2019)
Xin, X., Wang, Z., Yang, Q., Li, F.: Efficient identity-based public-key quantum signature scheme. Int. J. Mod. Phys. B. 34(10), 2050087 (2020)
Kashefi, E., Kerenidis, I.: Statistical zero knowledge and quantum one-way functions. Theor. Comput. Sci. 378(1), 101 (2007)
Hosoyamada, A., Yasuda, K.: Building quantum-one-way functions from block ciphers: Davies–Meyer and Merkle–Damgård constructions. In: International Conference on the Theory and Application of Cryptology and Information Security, pp. 275–304. Springer, Cham (2018)
Buhrman, H., Cleve, R., Watrous, J., De Wolf, R.: Quantum fingerprinting. Phys. Rev. Lett. 87(16), 167902 (2001)
Behera, A., Paul, G.: Quantum to classical one-way function and its applications in quantum money authentication. Quantum Inf. Process. 17(8), 200 (2018)
Shang, T., Tang, Y., Chen, R., Liu, J.: Full quantum one-way function for quantum cryptography. Quantum Eng. 2(1), e32 (2020)
Holevo, A.S.: Problems in the mathematical theory of quantum communication channels. Rep. Math. Phys. 12(2), 273 (1977)
Luo, M.X., Chen, X.B., Yun, D., Yang, Y.X.: Quantum signature scheme with weak arbitrator. Int. J. Theor. Phys. 51(7), 2135 (2012)
Bennett, C.H., Brassard, G., Breidbart, S., Wiesner, S.: Quantum cryptography, or unforgeable subway tokens. In: Advances in Cryptology, pp. 267–275. Springer, Boston (1983)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67(6), 661 (1991)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68(21), 3121 (1992)
Zhang, C.M., Zhu, Y., Chen, J.J., Wang, Q.: Practical quantum digital signature with configurable decoy states. Quantum Inf. Process. 19(5), 151 (2020)
Zheng, M., Xue, K., Li, S., Yu, N.: A practical quantum designated verifier signature scheme for E-voting applications. Quantum Inf. Process. 20(7), 230 (2021)
Curty, M., Santos, D.J., Pérez, E., García-Fernández, P.: Qubit authentication. Phys. Rev. A. 66(2), 022301 (2002)
Foulds, S., Kendon, V., Spiller, T.: The controlled SWAP test for determining quantum entanglement. Quantum Sci. Technol. 6(3), 035002 (2021)
Acknowledgements
This work is supported by National Natural Science Foundation of China (Grant Nos. 61772134, 61701553, 71874215, 71973057), National Social Science Foundation of China (21BZZ108), National Defense Science and Technology Innovation Special Zone Project (No. 18-163-11-ZT-002-045-04) and the Open Foundation of State key Laboratory of Networking and Switching Technology (Beijing University of Posts and Telecommunications) (SKLNST-2018-1-03).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: Review of Chen et al.’s public-key quantum signature scheme
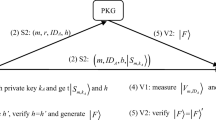
Chen et al.’s public-key quantum signature scheme [23] includes three steps.
i. Key generation phase
The signer’s public key \(k_{p u b}\) is derived from her personal public identity information and the PKG generates the private key \(k_{p r i}\) by the following steps:
(1) The signer and PKG share \(k_{A T}\) as their shared key in advance.
(2) PKG secretly selects a classical one-way function G and a random number \(k_{r}\).
(3) PKG calculates the private key \(k_{p r i}:=G\left( k_{p u b}\right) \oplus k_{r}\) and transmits \(E_{k_{A T}}\left( k_{p r i}\right) \) to the signer.
ii. Signature phase
The signer generates the quantum signature on the message \(m=(m_1, m_2, \ldots , m_n)\) by following steps:
(1) Choose two random strings \(s=\left( s_{1}, s_{2}, \ldots , s_{n}\right) \) and \(t=\left( t_{1}, t_{2}, \ldots , t_{n}\right) \).
(2) Generate \(|\phi \rangle _{s_{l}, t_{l} \oplus m_{l}}=H^{s_{l}} U_{\frac{\pi }{4}} H^{t_{l} \oplus m_{l}}|0\rangle \) and \(|\varphi \rangle _{s_{l}, t_{l} \oplus m_{l}, m_{l}}=Y^{m_{l}}|\phi \rangle _{s_{l}, t_{l} \oplus m_{l}}, \quad \) where \(l=\) \(1,2, \ldots , n\) and
Let \(|\phi \rangle _{s, t \oplus m}=\otimes _{l=1}^{n}|\phi \rangle _{s_{l}, t_{l} \oplus m_{l}}\) and \(|\varphi \rangle _{s, t \oplus m, m}=\otimes _{l=1}^{n}|\varphi \rangle _{s_{l}, t_{l} \oplus m_{l}, m_{l}} .\)
(3) Generate signature \(|S\rangle _{k_{p r i}, m}=\otimes _{l=1}^{n}|S\rangle _{k_{p r i_{l}}, m_{l}}=\otimes _{l=1}^{n} H^{k_{p u b_{l}} \oplus k_{p r i_{l}}}|\varphi \rangle _{s_{l}, t_{l} \oplus m_{l}, m_{l}} .\)
(4) Calculate \(|P\rangle :=H^{k_{p r i}}|\phi \rangle _{s, t \oplus m} \in \{|0\rangle ,|1\rangle ,|+\rangle ,|-\rangle \}^{n}\), denote by \(B_{P}=Basis(|P\rangle )\) the basis of each qubit state in \(|P\rangle \) and denote classical \(2 \mathrm {n}\)-bit P for the n-qubit state \(|P\rangle \) by \(|0\rangle \) encoded into \(01,|1\rangle \) encoded into \(00,|+\rangle \) encoded into 10 and \(|-\rangle \) encoded into 11 .
(5) Generate uw copies of quantum digest \(|F\rangle :=|F(t\Vert m\Vert P \Vert t s)\rangle \) with the public quantum one-way function F, where u indicates the maximum number of verifiers, w is some safety parameter threshold and ts represents timestamp.
(6) Send quantum digest \(E_{k_{A T}}\left( t s, \otimes _{l=1}^{u w}|F\rangle \right) \) to PKG and signature \(\left( t s, m, B_{P},|S\rangle _{k_{\text{ pri } }, m}\right) \) to the verifier.
iii. Verification phase
The verifier verifies the quantum signature \(\left( t s, m, B_{P},|S\rangle _{k_{p r i}, m}\right) \) by the following steps.
(1) Generate \(|V\rangle _{k_{p u b, s}}:=H^{k}{ }_{p u b}|S\rangle _{k_{p r i}, m}\) and \(|V\rangle _{m, k_{p u b, s}}:=Y^{m}|V\rangle _{k_{p u b, s}}\)
(2) Measure \(|V\rangle _{m, k_{p u b}, S}\) according to \(B_{P}\) and get the result \(|Q\rangle \), which is converted to set of classical 2-bit string denoted as \(Q \in \{00,01,10,11\}^{n} .\)
(3) Infer the random t from Q and generate w copies of quantum digest \(|F\rangle ^{\prime }:=|F(t\Vert m\Vert Q \Vert \) \(t s)\rangle \) with the public quantum one-way function F.
(4) Gain \(\left( t s, \otimes _{l=1}^{w}|F\rangle \right) \) from \(\mathrm {PKG}\) and compare \(|F\rangle ^{\prime }\) with \(|F\rangle \) by SWAP test. If the number \(w^{\prime }\) of \(|F\rangle ^{\prime }=|F\rangle \) is greater than the given a security threshold \(w_{0}\), the verifier accepts the signature. Otherwise, he rejects the signature.
Appendix B: Forgery attack
In this section, we will prove that the scheme in [23] is insecure against forgery attack. That is, a malicious attacker can forge Alice’s signature by verifying the legitimate signature.
Since the signature
it follows that the attacker does not need to obtain the private key \(k_{p r i}\), as long as he/she learns about \(k_{p r i} \oplus s\) and t, he/she can learn about \(H^{k_{p u b} \oplus k_{p r i} \oplus s \oplus m} U_{\frac{\pi }{4}} H^{t}\) so as to forge a quantum signature \(|S\rangle _{k_{p r i}, m} .\)
First, the attacker can intercept \(\left( t s, m, B_{P},|S\rangle _{k_{p r i}, m}\right) \) and generate \(|V\rangle _{m, k_{p u b}, s}\),
Then, the attacker measures \(|V\rangle _{m, k_{p u b, s}}\) according to \(B_{P}\) so that he/she can infer the random \(k_{p r i} \oplus s\) and t. Hence, the attacker can forge the signature \(|S\rangle _{k_{p r i}, m}\) for the original message m.
Note that the attacker does not need to disturb the channel between the signer and PKG. According to the verification phase, it is easy to prove that the forgery can pass the verification. Therefore, the public-key quantum signature in [23] is insecure against the forgery attack.
Moreover, because a malicious attacker can forge the signer’s signature, the signer can deny his/her valid quantum signature and claim that the signature is forged by another party. Therefore, the scheme in [23] is not secure against repudiation, either.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chen, HM., Jia, HY., Wu, X. et al. Public-key quantum signature for classical messages without third-party verification. Quantum Inf Process 21, 282 (2022). https://doi.org/10.1007/s11128-022-03627-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-022-03627-1