Abstract
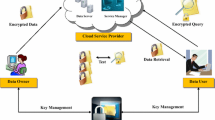
Cloud storage is one of the most important applications in our daily lives. User can store their own data into cloud storage and remotely access the saved data. Owing to the social media develops, users can share the digital files to other users, leading to the amount of data growing rapidly and searching abilities necessarily. In the some cases, servers cannot avoid data leakage even if the server provides complete access control. The encrypted data is a best way to resolve this problem but it may eliminate original structure and searching may become impossible. Applying searchable encryption for each receiver may produce messy duplication and occupy the quota of cloud storage from each receiver. User requires keeping their shared documents belonging up to date which are compared with the latest version. To this aim, we thus propose a sharable ID-based encryption with keyword search in cloud computing environment, which enables users to search in data owners’ shared storage while preserving privacy of data. For the performance analysis, we demonstrate the compared resultant with others ID-based or ID-relative encryption. In addition to that, we show the formal proof to verify the security of our proposed.


Similar content being viewed by others
References
Wang C, Ren K, Lou WJ, Li J (2010) Toward publicly auditable secure cloud data storage services. IEEE Netw 24:19–24
Cao Q, Jujita S (2014) Cost-effective replication schemes for query load balancing in DHT-based peer-to-peer file searches. J Inf Process Syst 10:628–645
Subashini S, Kavitha V (2011) A survey on seucrity issues in service delivery models of cloud computing. J Netw Comput Appl 34:1–11
Lee SH, Lee IY (2013) A secure index management scheme for providing data sharing in cloud storage. J Inf Process Syst 9:287–300
Naruse T, Mohri M, Shiraish Y (2015) Provably secure attribute-based encryption with attribute revocation and grant function using proxy re-encryption and attribute key for updaing. Hum-Cent Comput Inf Sci 5:8:1–8:13
Bringer J, Chabane H (2012) Embedding edit distance to enable private keyword search. Hum-cent Comput Inf Sci 2:2:1–2:12
Bellare M, Boldyreva A, O’Neill A (2007) Deterministic and efficiently searchable encryption. In: Proceedings of advances in cryptology—CRYPT, vol 2007, pp 535–552
Reza C, Juan G, Seny K, Rafail O (2006) Searchable symmetric encryption: improved definitions and efficient constructions, In: Proceedings of 13th ACM conference on computer and communications security (CCS), pp 79–88
Shamir A (1985) Identity-based cryptosystems and signature schemes. In: Proceedings of advances in cryptology—CRYPTO, vol 85, pp 47–53
Boneh D, Franklin M (2001) Identity-based encryption from the weil pairing. In: Proceedings of advances in cryptology—CRYPTO, vol 2001, pp 213–229
Boneh D, Boyen X (2004) Efficient selective-ID secure identity-based encryption without random oracles. In: Proceedings of advances in cryptology—EUROCRYPT, vol 2004, pp 223–238
Boneh D, Crescenzo GD, Ostrovsky R, Persiano G (2004) Public key encryption with keyword search. In: Proceedings of advances in cryptology—EUROCRYPT, vol 2004, pp 506–522
Baek J, Safavi-Naini R, Susilo W (2008) Public key encryption with keyword search revisited. In: Proceedings of computational science and its applications ICCSA, vol 2008, pp 1249–1259
Tian X, Wang Y (2008) ID-Based encryption with keyword search scheme from bilinear pairings. In: Proceedings of 4th international conference on wireless communications, networking and mobile computing (WiCOM), pp 1–4
Rhee HS, Park JH, Susilo W, Lee JH (2009) Improved searchable public key encryption with designated tester. In: proceedings of 4th international symposium on information, computer, and communications security (ASIA CCS), pp 376–379
Liu Q, Wang G, Wu J (2012) Secure and privacy preserving keyword searching for cloud storage services. J Netw Comput Appl 35:927–933
Lai J, Zhou X, Deng R, Li Y (2013) Expressive search on encrypted data. In: Proceedings of 8th ACM SIGSAC symposium on information, computer and communications security, pp 243–252
Wang P, Wang H, Pieprzyk J (2008) Keyword field-free conjunctive keyword searches on encrypted data and extension for dynamic groups. Cryptol Netw Secur 5339:178–195
Kerschbaum F (2011) Secure conjunctive keyword searches for unstructured text. In: Proceedings of 5th international conference on network and system security (NSS), pp 285–289
Boneh D, Lynn B, Shacham H (2004) Short signatures from the weil pairing. J Cryptol 14:297–319
Ding M, Gao F, Jin Z, Zhang H (2012) An efficient public key encryption with conjunctive keyword search scheme based on pairings. In: Proceedings of 3rd IEEE international conference on network infrastructure and digital content (IC-NIDC), pp 526–530
Gupta S, Satapathy SR, Mehta P, Tripathy A (2013) A secure and searchable data stroage in cloud computing. In: Proceedings of 3rd international conference on advance computing conference (IACC), pp 106–109
Ibraimi J, Nikova S, Hartel P, Jonker W (2011) Public-key encryption with delegated search. Appl Cryptograph Netw Secur 6715:532–549
Li M, Yu S, Cao N, Lou W (2011) Authorized private keyword search over encrypted data in cloud computing. In: Proceedings of 31th international conference on distributed computing systems (ICDCS), pp 383–392
Yang Y, Lu H, Weng J (2011) Multi-user private keyword search for cloud computing. In: Proceedings of 3th international conference on cloud computing technology and science (CloudCom), pp 264–271
Tang Q, Chen X (2013) Towards asymmetric searchable encryption with message recovery and flexible search authorization. In: Proceedings of 8th international symposium on information, computer, and communications security (ASIA CCS), pp 253–264
Li J, Li J, Liu Z, Jia C (2013) Enabling efficient and secure data sharing in cloud ccomputing. Concurr Comput Pract Exp 26:1052–1066
Lin MP, Hong WCh, Chen CH, Cheng CM (2013) Design and implementation of multi-user secure indices for encrypted cloud storage. In: Proceedings of 11th annual international conference on privacy, security and trust (PST), pp 177–184
Liu Q, Wang G, Wu J (2009) An efficient privacy preserving keyword search scheme in cloud computing. In: Proceedings of international conference on computational science and engineering (CSE), pp 725–720
Yoon HJ, Cheon JH, Kim YD (2005) Batch verifications with ID-based signatures. In: Proceedings of information security and cryptology ICISC, vol 2005, pp 233–248
Acknowledgments
This work was supported in part by the Ministry of Science and Technology, Taiwan, under Contract MOST 103-2221-E-007-073-MY3, MOST 104-2811-E-007-005, MOST 103-2218-E-031-001, and MOST 103-2221-E-004-009. The work of Prof. Li Xu was supported in part by the National Natural Science Foundation of China (U1405255).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Xu, L., Weng, CY., Yuan, LP. et al. A shareable keyword search over encrypted data in cloud computing. J Supercomput 74, 1001–1023 (2018). https://doi.org/10.1007/s11227-015-1515-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-015-1515-8