Abstract
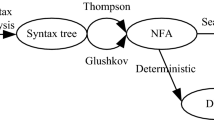
Finite state automata are widely used in firewalls, data detection and content audit systems to match complex sets of regular expressions in network packets. However, with the continuous increase in the types of network contents and network traffics in recent years, the deep packet inspection systems based on finite state automata also require regular engines for less memory consumption and higher operating speed. This paper analyzes the feature and problem of finite state automata and improves non-deterministic finite automata by reducing the conversion edge to reduce the memory usage. The experiment results which are made by real-world dataset show that the memory usage is reduced more than half.













Similar content being viewed by others
References
Yin C, Zhang S (2017) Parallel implementing improved k-means applied for image retrieval and anomaly detection. Multimed Tools Appl 76(16):16911–16927
Wang J, Zhang Z, Li B, Lee S, Sherratt RS (2014) An enhanced fall detection system for elderly person monitoring using consumer home networks. IEEE Trans Consum Electron 60(1):23–29
Yin C, Xi J, Sun R (2017) Location privacy protection based on differential privacy strategy for big data in industrial internet-of-things. IEEE Trans Ind Inf. https://doi.org/10.1109/tii.2017.2773646
Fu Z, Ren K, Shu J, Sun X, Huang F (2016) Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Trans Parallel Distrib Syst 27(9):2546–2559
Keegan N, Ji S-Y, Chaudhary A, Concolato C, Yu B, Jeong DH (2016) A survey of cloud-based network intrusion detection analysis. Human-Cent Comput Inf Sci 6(1):19
Rathod SB, Reddy VK (2017) Ndynamic framework for secure vm migration over cloud computing. J Inf Process Syst 13(3):476–490
Iuga C, Nurse JRC, Erola A (2016) Baiting the hook: factors impacting susceptibility to phishing attacks. Human-Cent Comput Inf Sci 6(1):1–20
Sherry J, Lan C, Popa RA, Ratnasamy S (2015) Blindbox: deep packet inspection over encrypted traffic. ACM SIGCOMM Comput Commun Rev 45(4):213–226
Dharmapurikar S, Krishnamurthy P, Sproull TS, Lockwood JW (2004) Deep packet inspection using parallel bloom filters. IEEE Micro 24(1):52–61
Yin C, Feng L, Ma L (2016) An improved Hoeffding-ID data-stream classification algorithm. J Supercomput 72(7):2670–2681
Gu B, Sun X, Sheng VS (2017) Structural minimax probability machine. IEEE Trans Neural Netw Learn Syst 28(7):1646–1656
Yin C, Xia L, Zhang S, Sun R, Wang J (2017) Improved clustering algorithm based on high-speed network data stream. Soft Comput 22:4185–4195
Ma T, Zhang Y, Cao J, Shen J, Tang M, Tian Y, Al-Rodhaan M (2015) KDVEM: a k-degree anonymity with vertex and edge modification algorithm. Computing 97(12):1165–1184
Gu B, Sheng VS, Tay KY, Romano W, Li S (2015) Incremental support vector learning for ordinal regression. IEEE Trans Neural Netw Learn Syst 26(7):1403–1416
Gu B, Sheng VS (2017) A robust regularization path algorithm for v-support vector classification. IEEE Trans Neural Netw Learn Syst 28(5):1241–1248
Ma J, Zhou H, Zhao J, Gao Y, Jiang J, Tian J (2015) Robust feature matching for remote sensing image registration via locally linear transforming. IEEE Trans Geosci Remote Sens 53(12):6469–6481
Zeng D, Dai Y, Li F, Sherratt RS, Wang J (2018) Adversarial learning for distant supervised relation extraction. Comput Mater Contin 55(1):121–136
Tu Y, Lin Y, Wang J, Kim JU (2018) Semi-supervised learning with generative adversarial networks on digital signal modulation classification. Comput Mater Contin 55(2):243–254
Bando M, Artan NS, Chao HJ (2012) Scalable lookahead regular expression detection system for deep packet inspection. IEEE/ACM Trans Netw 20(3):699–714
Vuppala R, Farik M (2015) Intrusion detection amp prevention systems-sourcefire snort. Int J Sci Technol Res 4(8):220–223
Paxson V (1999) Bro: a system for detecting network intruders in real-time. Comput Netw 31(23):2435–2463
Brüggemann-Klein A (1993) Regular expressions into finite automata. Theoret Comput Sci 120(2):197–213
Vespa L, Weng N (2011) Deterministic finite automata characterization and optimization for scalable pattern matching. ACM Trans Arch Code Optim 8(1):1–31
Lo CTD, Tai YG (2009) Space optimization on counters for FPGA-based perl compatible regular expressions. ACM Trans Reconfig Technol Syst 2(4):1–18
Yu F, Chen Z, Diao Y, Lakshman T, Katz RH (2006) Fast and memory-efficient regular expression matching for deep packet inspection. In: ACM/IEEE Symposium on Architecture for Networking and Communications Systems, 2006. ANCS 2006, pp 93–102
Becchi M, Crowley P (2008) Extending finite automata to efficiently match Perl-compatible regular expressions. In: ACM conference on emerging network experiment and technology, pp 1–12
Becchi M, Crowley P (2007) A hybrid finite automaton for practical deep packet inspection. In: Proceedings of the 2007 ACM CoNEXT Conference, pp 1–12
Kumar A, Verma AK (2014) A novel algorithm for the conversion of parallel regular expressions to non-deterministic finite automata. Appl Math Inf Sci 8(1):95–105
Acknowledgements
This work was funded by National Natural Science Foundation of China (61772282, 61772454, 6171101570). It was also supported by the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD), Postgraduate Research and Practice Innovation Program of Jiangsu Province (KYCX17_0901), Natural Science Foundation of Jiangsu Province (BK20150460) and Jiangsu Collaborative Innovation Center on Atmospheric Environment and Equipment Technology (CICAEET). It was also funded by the open research fund of Key Lab of Broadband Wireless Communication and Sensor Network Technology (Nanjing University of Posts and Telecommunications), Ministry of Education.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yin, C., Wang, H., Yin, X. et al. Improved deep packet inspection in data stream detection. J Supercomput 75, 4295–4308 (2019). https://doi.org/10.1007/s11227-018-2685-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-018-2685-y