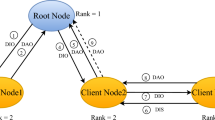
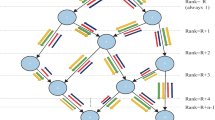
Abstract
The routing protocol for low power and lossy networks works as an effective method for communication in Contiki. However, many security attacks exist in RPL. These attacks affect the traffic or energy of the network. This paper focused on the persistent explorations of Contiki-based IoT networks to examine the effect of three well-known security attacks that exist on RPL. The RPL security attacks are named as: hello flood attack, decreased rank attack and increased version attack. The impact of these security attacks has been evaluated for scalability, energy efficiency and destination-oriented directed acyclic graph construction over simulated IoT networks in Contiki. All three aforesaid attacks are found to be responsible for affecting the DODAG construction, rising the network traffic and power consumption in one way or the other. To investigate the impact of attacks particularly on the scalability, the simulations are accomplished using eight different scenarios. It is found that the throughput of the network increases with the rise in the number of normal nodes (N) up to a critical point, at which N has optimum value. It is found that at N = 40, the critical point appears for many categories in different attacks. Like, “resdm” and “resem” categories possess this critical point through hello flood attack. Similarly, the “rdsdm” category has maximum throughput at N = 40 through increased version attack. Likewise, the decreased rank attack brought this critical point at N = 40 for categories “rdsem” and “resem”. The simulation results show that regardless of the attacks “rese” and “rdse” categories produce more throughput than “resd” and “rdsd” categories. This work also demonstrates the effect of the size of heterogenous packets on multiple throughput metrics.






















Similar content being viewed by others
References
Kocakulak M, Butun I (2017) An overview of wireless sensor networks towards internet of things. In: Computing and Communication Workshop and Conference (CCWC), 2017 IEEE 7th Annual, pp 1–6
Botta A, Donato WD, Persico V, Pescape A (2016) Integration of cloud computing and internet of things: a survey. Future Gener Comput Syst 56:684–700
Khalil N, Abid MR, Benhaddou D, Gerndt M (2014) Wireless sensors networks for internet of things. In: 2014 IEEE Ninth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), pp 1–6
Kawamoto D (2017) IoT security incidents rampant and costly”, https://www.darkreading.com/vulnerabilities---threats/iot-security-incidents-rampant-and-costly/d/d-id/1329367, pp 1–9
Abualigah L, Diabat A (2020) A comprehensive survey of the grasshopper optimization algorithm: results, variants, and applications. Neural Comput Appl 32(19):15533–15556
Tsamardinos I, Brown LE, Aliferis CF (2006) The max-min hill-climbing Bayesian network structure learning algorithm. Mach Learn 65:31–78
Gerkey BP, Thrun S, Gordon G (2005) Parallel stochastic hill climbing with small teams. In: Parker LE, Schneider FE, Schultz AC (eds) Multi-robot systems: from swarms to intelligent automata. Springer, Berlin, pp 65–77
Rizzo G, Fanizzi N, Amato CD (2020) Class expression induction as concept space exploration: from DL-Foilto DL-Focl. Future Gener Comput Syst 108(2020):256–272
Bysani LK and Turuk AK (2011) A survey on selective forwarding attack in wireless sensor networks. In: IEEE International Conference on Devices and Communications (ICDeCom). Mesra, pp 1–5
Gaddour O, Koubaa A (2012) RPL in a nutshell: a survey. Comput Netw 56(14):3163–3178
Pongle P, Chavan G (2015) A survey: attacks on RPL and 6LoWPAN in IoT. In: 2015 International Conference on Pervasive Computing (ICPC), pp 1–6
Adat V, Gupta BB (2018) Security in internet of things: issues, challenges, taxonomy, and architecture. Telecommun Syst 67(3):423–441
Javed F, Afzal MK, Sharif M, Kim BS (2018) Internet of things (IoTs) operating systems support, networking technologies, applications, and challenges: a comparative review. IEEE Commun Surv Tutor 2018:1–39
Liu X, Sheng Z, Yin C, Ali F, Roggen D (2017) Performance analysis of routing protocol for low power and lossy networks (RPL) in largescale networks. IEEE Internet Things J 4(6):2172–2185
Ghaleb B, Al-Dubai AY, Ekonomou E, Alsarhan A, Nasser Y, Mackenzie L, Boukerche A (2018) A survey of limitations and enhancements of the ipv6 routing protocol for low-power and lossy networks: a focus on core operations. IEEE Commun Surv Tutor 21(2):1607–1635
Wallgren L, Raza S, Voigt T (2013) Routing attacks and countermeasures in the RPL-based internet of things. Int J Distrib Sens Netw 9(8):794326
Sehgal A, Mayzaud A, Badonnel R, Chrisment I, Schönwälder J (2014) Addressing DODAG inconsistency attacks in RPL networks.In: Proceeding of GIIS Conference, pp 1–8
Mayzaud A, Sehgal A, Badonnel R, Chrisment I, Schonwalder J (2014) A study of RPL DODAG version attacks, in AIMS’14. Springer, Berlin, pp 92–104
Mayzaud A, Sehgal A, Badonnel R, Chrisment I, Schönwälder J (2015) Mitigation of topological inconsistency attacks in RPL-based low-power lossy networks. Int J Netw Manag 25(5):320–339
Mayzaud A, Badonnel R, Chrisment I (2016) A taxonomy of attacks in RPL-based internet of things. Int J Netw Secur 18(3):459–473
Ahmed F, Ko YB (2016) Mitigation of black hole attacks in routing protocol for low power and lossy networks. Secur Commun Netw 9(18):5143–5154
Aris A, Oktug SF, Yalcin SBO (2016) RPL version number attacks: in-depth study. In: 2016 IEEE/IFIP Network Operations and Management Symposium (NOMS 2016), pp 776–779
Johnson MO, Siddiqui A, Karami A (2017) A wormhole attack detection and prevention technique in wireless sensor networks. Int J Comput Appl 174(1):1–8
Diro AA, Chilamkurti N (2018) Distributed attack detection scheme using deep learning approach for internet of things. Future Gener Comput Syst 82:761–768
Perazzo P, Vallati C, Varano D, Anastasi G, Dinni G (2018) Implementation of a wormhole attack against a RPL network: challenges and effects. In: 2018 14th Annual Conference on Wireless On-Demand Network Systems and Services (WONS), pp 95–102
Jyothisree MVR, Sreekanth S (2019) Attacks in RPL and detection technique used for internet of things. Int J Recent Technol Eng (IJRTE) 8(1):1876–1879
Raoof A, Matrawy A, Lung CH (2018) Routing attacks and mitigation methods for rpl-based internet of things. IEEE Commun Surv Tutor 21(2):1582–1606
Sahay R, Geethakumari G, Mitra B, Sahoo I (2020) Efficient framework for detection of version number attack in internet of things. In: Abraham A, Cherukuri A, Melin P, Gandhi N (eds) Intelligent systems design and applications (ISDA 2018). Advances in intelligent systems and computing (AISC 941). Springer, Berlin, pp 480–492
Raza S, Wallgren L, Voigt T (2013) SVELTE: real-time intrusion detection in internet of things. Ad Hoc Netw 11:2661–2674
Kasinathan P, Pastrone C, Spirito MA, Vinkovits M (2013) Denial-of-service detection in 6LoWPAN based internet of things, wireless and mobile computing, networking and communications (WiMob). In: 2013 IEEE 9th International Conference on IEEE, pp 600–607
Rghioui A, Khannous A, Bouhorma M (2014) Denial-of-service attacks on 6LoWPAN- RPL networks: threats and an intrusion detection system proposition. J Adv Comput Sci Technol 3(2):143–153
Sheikhan M, Bostani H (2016) A hybrid intrusion detection architecture for internet of things. In: 8th International Symposium on Telecommunications, IEEE, pp 601–606
Bhosale SD, Sonavane SS (2019) A real-time intrusion detection system for wormhole attack in the RPL based internet of things. In: The 12th International Conference Inter Disciplinarity in Engineering, Procedia Manufacturing 32 (2019), pp 840–847
Kfoury E, Saab J, Younes P, Achkar R (2019) A self organizing map intrusion detection system for RPL protocol attacks. Int J Interdiscip Telecommun Netw 11(1):30–43
Sharma M, Elmiligi H, Gebali F,Verma A (2019) Simulating attacks for RPL and generating multi-class dataset for supervised machine learning. In: 2019 IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), pp 20–26
Qureshi KN, Rana SS, Ahmed A, Jeon G (2020) A novel and secure attacks detection framework for smart cities industrial internet of things. Sustain Cities Soc 2020:1–33
Seeber S, Sehgal A, Stelte B, Rodosek GD, Schönwälder J (2013) Towards a trust computing architecture for RPL in cyber physical systems. In: IFIP/IEEE International Conference on Network and Service Management (CNSM-2013), pp 134–137
Fotouhi H, Moreira D, Alves M, Yomsi PM (2017) mRPL+: a mobility management framework in RPL/6LoWPAN. Comput Commun 104(2017):34–54
Ferreira HGC, Desousa RT (2017) Security analysis of a proposed internet of things middleware. Clust Comput 20(1):651–660
Khoury D, Kfoury E (2017) Generic hybrid methods for secure connections based on the integration of GBA and TLS/CA. Sens Netw Smart Emerg Technol (SENSET). https://doi.org/10.1109/SENSET.2017.8125033
Marques BF, Recardo MP (2014) Improving the energy efficiency of WSN by using application layer topologies to constrain RPL-defined routing trees. In: 2014 13th Annual Mediterranean Ad Hoc Networking Workshop (MED-HOC-NET), pp 126–133
Pavkovic B, Duda A, Hwang WJ, Theoleyre F (2014) Efficient topology construction for RPL over IEEE 802.15.4 in wireless sensor networks. Ad Hoc Netw 15:25–38
Glissa G, Rachedi A, Meddeb A (2016) A secure routing protocol based on RPL for internet of things. In: 2016 IEEE Global Communications Conference (GLOBECOM), pp 1–7
Kalyani S, Vydeki D (2018) Measurement and analysis of QoS parameters in RPL network. In: 2018 Tenth International Conference on Advanced Computing (ICoAC), pp 1–6
Airehrour D, Gutierrez JA, Ray SK (2018) SecTrust-RPL: a securetrust-aware RPL routing protocol for internet of things. Future Gener Comput Syst 2018:1–29
Tanganelli G, Virdis A, Mingozzi E (2019) Implementation of software-defined 6LoWPANs in Contiki OS. In: 2019 IEEE 20th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), pp. 1–6
Tutunović M, Wuttidittachotti P (2019) Discovery of suitable node number for wireless sensor networks based on energy consumption using Cooja. In: Advanced Communication Technology (ICACT) 2019 21st International Conference on, 2019, pp 168–172
Bhandari KS, Ra IH, Cho G (2020) Multi-topology based QoS-differentiation in RPL for internet of things applications. IEEE Access. https://doi.org/10.1109/ACCESS.2020.2995794
Sanila A, Mahapatra B, Turuk AK (2020) Performance evaluation of RPL protocol in a 6LoWPAN based Smart Home Environment. In: 2020 International Conference on Computer Science, Engineering and Applications (ICCSEA)
Roussel K, Song YQ, Zendra O (2016) Using Cooja for WSN Simulations: some new uses and limits, EWSN 2016–Next mote workshop, Austria, Feb 2016. ACM, Junction Publishing, pp 319-324
Uwase MP, Long NT, Tiberghien J, Steenhaut K, Dricot JM (2014) Poster abstract: outdoors range measurements with zolertia z1 motes and contiki. In: Langendoen K, Hu W, Ferrari F, Zimmerling M, Mottola L (eds) Real-world wireless sensor network. Lecture notes in electrical engineering. Springer, Berlin, pp 79–83
Kharche S, Pawar S (2016) Node level energy consumption analysis in 6lowpan network using real and emulated Zolertia Z1 motes. In: 2016 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), pp 1–5
Kharche S, Pawar S (2017) Effect of radio link and network layer parameters on performance of Zolertia Z1 motes based 6LoWPAN. In: 2017 8th International Conference on Computing, Communication and Networking Technologies (ICCCNT), pp 1–7
Hendrawan INR, Arsa IGNW (2017) Zolertia Z1 energy usage simulation with Cooja simulator, informatics and computational sciences (ICICoS). In: 2017 1st International Conference on, 2017, pp 147–152
Bandekar A, Kotian A, Javaid AY (2017) Comparitive analysis of simulation and real-world energy consumption for battery-life estimation of low-power IoT (Internet of Things) deployment in varying environmental conditions using Zolertia Z1 motes, ICST Institute for Computer Sciences, Social Informatics and Telecommunication Engineering 2017 (LNICST 205), pp 137–148
Mian AN, Alvi SA, Khan R, Zulqarnain M, Iqbal W (2016) Experimental study of link quality in IEEE 802.15.4 using Z1 Motes. In: 2016 International Wireless Communications and Mobile Computing Conference (IWCMC) pp 830–835
Hondt AD, Bahmad H, Vanhee J (2016) RPL attacks framework, mobile and embedded computing LINGI2146 Report, pp 1–14
O¨sterlind F, Dunkels A, Eriksson J, Finne N, Voigt T (2006) Cross-level sensor network simulation with Cooja In: IEEE 31st Conference on Local Computer Networks, LCN ’06, IEEE Computer Society, pp 641–648
Dunkels A, Gronvall B, Voigt T (2004) Contiki–a lightweightand flexible operating system for tiny networked sensors. In: 29th Annual IEEE International Conference on Local Computer Networks (LCN’04), IEEE Computer Society, pp 455–462
Verma VK, Ntalianis K, Moreno CM, Yang CT (2019) Next-generation Internet of things and cloud security solutions. Int J Distrib Sens Netw. https://doi.org/10.1177/1550147719835098
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sharma, S., Verma, V.K. Security explorations for routing attacks in low power networks on internet of things. J Supercomput 77, 4778–4812 (2021). https://doi.org/10.1007/s11227-020-03471-z
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-020-03471-z