Abstract
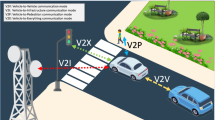
Wireless communication among vehicular ad hoc network (VANET) entities is secured through cryptography, which is used for authentication as well as to ensure the overall security of messages in this environment. Authentication protocols play a significant role and are therefore required to be free of vulnerabilities that allow entity impersonation, unauthorized entry, and general misuse of the system. A resourceful adversary can inflict serious damage to VANET systems through such vulnerabilities. We consider several VANET authentication protocols in the literature and identify vulnerabilities. In addition to the commonly considered vulnerabilities in VANETs, we observe that the often-overlooked relay attack is possible in almost all VANET authentication protocols. Relay attacks have the potential to cause damage in VANETs through misrepresentation of vehicle identity, telematic data, traffic-related warnings, and information related to overall safety in such networks. We discuss possible countermeasures to address identified vulnerabilities. We then develop an authentication protocol that uses ambient conditions to secure against relay attacks and other considered vulnerabilities. We include security proof for the proposed protocol.

















Similar content being viewed by others
References
Mohar SS, Goyal S, Kaur R (2022) Localization of sensor nodes in wireless sensor networks using bat optimization algorithm with enhanced exploration and exploitation characteristics. J Supercomput 332:22
Ahmed S, Shamshad S, Ghaffar Z, Mahmood K, Kumar N, Parizi RM, Choo K-KR (2021) Signcryption based authenticated and key exchange protocol for EI-Based V2G environment. IEEE Trans Smart Grid 12(6):5290–5298
Mahmood K, Shamshad S, Kumari S, Khan MK, Obaidat MS (2020) Comment on lightweight secure message broadcasting protocol for Vehicle-to-Vehicle communication. IEEE Syst J 15(1):1366–1368
Shamshad S, Saleem MA, Obaidat MS, Shamshad U, Mahmood K, Ayub MF, On the security of a lightweight privacy-preserving authentication protocol for VANETs. IEEE Int Conf Artif Intell Smart Syst (ICAIS), 1766-1770, 2021
Shamshad S, Obaidat MS, Saleem MA, Shamshad U, Mahmood K, (2021) Security analysis on an efficient and provably secure authenticated key agreement protocol for Fog-based Vehicular Ad-Hoc Networks. Int Conf Artif Intell Smart Syst (ICAIS), 1754-1759
Umar M, Islam SKH, Mahmood K, Ahmed S, Ghaffar Z, Saleem MA (2021) Provable secure identity-based anonymous and privacy-preserving inter-vehicular authentication protocol for VANETS using PUF. IEEE Trans Veh Technol 70(11):12158–12167
Krishnan PR, Kumar PAR (2021) A collaborative strategy for detection and eviction of Sybil attacker and Sybil nodes in VANET. Int J Commun Syst 34(3):4621
Haydari A, Yilmaz Y (2018) Real-time detection and mitigation of DDoS attacks in intelligent transportation systems. IEEE Int Conf Intell Trans Syst (ITSC), 157-163
Greenberg A (2015) Hackers remotely kill a Jeep on the highway-with me in it.WIRED. https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/
A. Greenberg, Securing driverless cars from hackers is hard. Ask the ex-Uber guy who protects them. https://www.wired.com/ 2017/04/ubers-former-top-hacker-securing-autonomous-cars-really-hard-problem/
Golson J (2016) Car hackers demonstrate wireless attack on Tesla Model S.http://www.theverge.com/2016/9/19/12985120/teslamodel-s-hack-vulnerability-keen-labs
Nie S, Liu L, Du Y,Free-fall: hacking tesla from wireless to CAN bus. In: Proceedings of the Black Hat USA 2017, Las Vegas, 1-16, 2017
Miller C, Valasek C, Adventures in automotive networks and control units. http://illmatics.com/car_hacking.pdf
Watchdog C (2019) Kill switch: Why connected cars can be killing machines and how to turn them off.https://www.consumerwatchdog.org/sites/default/files/2019-07/KILL
Mikavika B, Kostić-Lyubisavljević A (2021) Blockchain-based solutions for security, privacy, and trust management in vehicular networks: a survey. J Supercomput 77:9520–9575
Saravanan M, Kumar SM (2021) Improved authentication in vanets using a connected dominating set-based privacy preservation protocol. J Supercomput 77:14630–14651
Raya M, Hubaux J-P (2007) Securing vehicular ad hoc networks. J Comput Secur 15(1):39–68
Nayak RP, Sethi S, Bhoi SK, Mohapatra D, Sahoo RR, Sharma PK, Putha D (2022) TFMD-SDVN: a trust framework for misbehavior detection in the edge of software-defined vehicular network. J Supercomput 78:7948–7981
Beth T, Desmedt Y(1990) Identification tokens - or: solving the chess grandmaster problem. Advances in Cryptology-CRYPTO’90, Springer LNCS 537, 169-177
Ali I, Lawrence T, Omala AA, Li F (2020) An efficient hybrid signcryption scheme conditional privacy-preservation for heterogeneous vehicular communication in VANETs. IEEE Trans Veh Technol 69(10):11266–11280
Ali I, Chen Y, Ullah N, Kumar R, He W (2021) An efficient and provably secure ECC-based conditional privacy-preserving authentication for vehicle-to-vehicle communication in VANETs. IEEE Trans Veh Technol 70(2):1278–1291
Alladi T, Chakravarty S, Chamola V, Guizani M (2020) A lightweight authentication and attestation scheme for in-transit vehicles in IoV scenario. IEEE Trans Veh Technol 69(12):14188–14197
Asaar MR, Salmasizadeh M, Susilo W, Majidi A (2018) A secure and efficient authentication technique for vehicular ad-Hoc networks. IEEE Trans Veh Technol 67(6):5409–5423
Liu Y, Wang L, Chen H-H (2015) Message authentication using proxy vehicles in vehicular ad hoc networks. IEEE Trans Veh Technol 64(8):3697–3710
Azees M, Vijayakumar P, Deborah LJ (2017) EAAP: efficient anonymous authentication with conditional privacy-preserving scheme for vehicular ad hoc networks. IEEE Trans Intell Transp Syst 18(9):2467–2476
Feng Q, He D, Zeadally S, Liang K (2020) BPAS: blockchain-assisted privacy-preserving authentication system for vehicular ad hoc networks. IEEE Trans Industr Inf 16(6):4146–4155
Chen C-M, Deng X, Gan W, Chen J, Islam SKH (2021) A secure blockchain-based group key agreement protocol for IoT. J Supercomput 77:9046–9068
He D, Zeadally S, Xu B, Huang X (2015) An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans Inf Forensics Secur 10(12):2681–2691
Ma Z, Zhang J, Guo Y, Liu Y, Liu X, He W (2020) An efficient decentralized key management mechanism for VANET with blockchain. IEEE Trans Veh Technol 69(6):5836–5849
Singh PK, Agarwal A, Nakum G, Rawat DB, Nandi S (2020) MPFSLP: masqueraded probabilistic flooding for source-location privacy in VANETs. IEEE Trans Veh Technol 69(10):11383–11393
Tzeng S-F, Horng S-J, Li T, Wang X, Huang P-H, Khan MK (2017) Enhancing security and privacy for identity-based batch verification scheme in VANETs. IEEE Trans Veh Technol 66(4):3235–3248
Vijayakumar P, Azees M, Kannan A, Deborah LJ (2016) Dual authentication and key management techniques for secure data transmission in vehicular ad hoc networks. IEEE Trans Intell Transp Syst 17(4):1015–1028
H. Tan, D. Choi, P. Kim, S. Pan, I. Chung, “Comments on “Dual authentication and key management techniques for secure data transmission in vehicular ad hoc networks”. ” IEEE Transactions on Intelligent Transportation Systems, 19(7), 2149-2151, July 2018
Azees M (2019) Reply to comments on “Dual authentication and key management techniques for secure data transmission in vehicular ad hoc networks. IEEE Trans Intell Transp Syst 20(9):3595
Wu W-C (2017) A secret push messaging service in VANET clouds. Journal of Supercomputing 73:3085–3097
L. Gong, R. Needham, R. Yahalom, “Reasoning about belief in cryptographic protocols.” Proceedings of the IEEE Symposium on Security and Privacy, 234-248, 1990
Acknowledgements
We thank the ten anonymous reviewers for their constructive comments and suggestions that helped us improve the content and presentation of this paper.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest:
None.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Piramuthu, O.B., Caesar, M. VANET authentication protocols: security analysis and a proposal. J Supercomput 79, 2153–2179 (2023). https://doi.org/10.1007/s11227-022-04736-5
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-022-04736-5