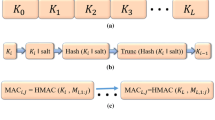
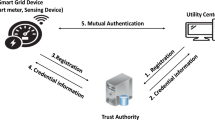
Abstract
In this paper, a new Global System of Mobile Communications (GSM) authentication protocol is proposed to improve some drawbacks of the current GSM authentication protocol for roaming users including: (a) communication overhead between VLR; (b) huge bandwidth consumption between VLR and HLR; (c) storage space overhead in VLR; (d) overloaded in HLR with authentication of mobile stations; and (e) not supporting bilateral authentication. The main contribution of this paper is that it does not only improve the drawbacks listed above but also fits the needs of roaming users. In addition, the proposed protocol does not change the existing architecture of GSM, and the robustness of the proposed protocol is the same as that of the original GSM, which is based on security algorithms A3, A5, and A8.
Similar content being viewed by others
References
Al-tawil, K., Akrami, A., & Youssef, H. (1998). A new authentication protocol for GSM networks. In IEEE 23rd annual conference on Local Computer Networks (LCN’98) (pp. 21–30).
Ammayappan, K., Saxena, A., & Negi, A. (2006). Mutual authentication and key agreement based on elliptic curve cryptography for GSM. In International conference on advanced computing and communications, 2006 (pp. 183–186), Dec. 2006.
Chang, C. C., Lee, J. S., & Chang, Y. F. (2005). Efficient authentication protocols of GSM. Computer Communications, 28, 921–928.
Dominguez, A. P. (2006). Cryptanalysis of Parka’s authentication protocol in wireless mobile communication systems. International Journal of Network Security, 3(3), 279–282.
ETSI (1993). Recommendation GSM 02.09: Security related network functions. Tech. rep., European Telecommunications Standards Institute, ETSI, June 1993.
ETSI (1993). Recommendation GSM 03.20: Security related network functions. Tech. rep., European Telecommunications Standards Institute, ETSI, June 1993.
Falletta, V., & Ricciato, F. (2009). Detecting scanners: empirical assessment on a 3G network. International Journal of Network Security, 9(2), 143–155.
Fanian, A., Berenjkoub, M., & Gulliver, T. A. (2009). A new mutual authentication protocol for GSM networks. In Canadian conference on electrical and computer engineering (pp. 798–803), May 2009.
Hahn, G., Kwon, T., Kim, S., & Song, J. (2004). Design and analysis of improved GSM authentication protocol for roaming users. In Lecture notes of computer science (vol. 3222, pp. 451–458).
Harn, L., & Lin, H. Y. (1995). Modification to enhance the security of the GSM protocol. In Proceedings of the 5th national conference on information security (pp. 416–420), Taipei, May 1995.
Hwang, M.-S. (1999). Dynamic participation in a secure conference scheme for mobile communications. IEEE Transactions on Vehicular Technology, 48(5), 1469–1474.
Hwang, M.-S., Lee, C.-C., & Lee, J.-Z. (2004). A new anonymous channel protocol in wireless communications. International Journal on Electronics and Communications, 58(3), 218–222.
Hwang, M.-S., Lee, C.-C., Lee, J.-Z., & Yang, C.-C. (2005). A secure protocol for bluetooth piconets using elliptic curve cryptography. Telecommunication Systems, 29(3), 165–180.
Hwang, M.-S., Tang, Y.-L., & Lee, C.-C. (2000). An efficient authentication protocol for GSM networks. In AFCEA/IEEE EuroComm’2000 (pp. 326–330), Munich, Germany, May 2000.
Jain, R., & Lin, Y. B. (1995). Performance modeling of an auxiliary user location strategy in a PCS network. ACM-Baltzer Wireless Networks, 1(2), 197–210.
Kalaichelvi, V., & Chandrasekaran, R. M. (2008). Secure authentication protocol for mobile. In International conference on computing, communication and networking (pp. 1–4), Dec. 2008.
Karger, P. A., Frankel, Y., & Herzberg, A. (1995). Security issues in a CDPD wireless network. IEEE Personal Communications, 2, 16–27.
Kumar, K. P., Shailaja, G., Kavitha, A., & Saxena, A. (2006). Mutual authentication and key agreement for GSM. In International conference on mobile business (pp. 25–28), June 2006.
Lee, C. H., Hwang, M.-S., & Yang, W. P. (1999). Enhanced privacy and authentication for the global system for mobile communications. Wireless Networks, 5, 231–243.
Lee, C.-C., Hwang, M.-S., & Liao, I.-E. (2008). A new authentication protocol based on pointer forwarding for mobile communications. Wireless Communications and Mobile Computing, 8(5), 661–672.
Lee, C.-C., Hwang, M.-S., & Yang, W.-P. (2003). Extension of authentication protocol for GSM. IEE Proceedings. Communications, 150(2), 91–95.
Lee, C.-C., Liao, I.-E., & Hwang, M.-S. (2009). An extended certificate-based authentication and security protocol for mobile networks. Information Technology and Control, 38(1), 61–66.
Li, J., Zhang, P., & Sampalli, S. (2008). Improved security mechanism for mobile IPv6. International Journal of Network Security, 6(3), 291–300.
Lo, C.-C., & Chen, Y.-J. (1999). A secure communication architecture for GSM networks. In IEEE Pacific Rim conference on communications, computers and signal processing (pp. 221–224).
Lo, C.-C., & Chen, Y.-J. (1999). Secure communication mechanisms for GSM networks. IEEE Transactions on Consumer Electronics, 45(4), 1074–1080.
Mallinder, B. (1988). An overview of the GSM system. In Proc. third Nordic seminar on digital land mobile radio commun. (pp. 12–15), Copenhagen, Denmark, Sep. 1988.
Mitrokotsa, A., Komninos, N., & Douligeris, C. (2010). Protection of an intrusion detection engine with watermarking in ad hoc networks. International Journal of Network Security, 10(2), 93–106.
Molva, R., Samfat, D., & Tsudik, G. (1994). Authentication of mobile users. IEEE Network, 8(2), 26–34.
Patcha, A., & Park, J.-M. (2006). A game theoretic formulation for intrusion detection in mobile ad hoc networks. International Journal of Network Security, 2(2), 131–137.
Rahnema, M. (1993). Overview of the GSM system and protocol architecture. IEEE Communication Magazine, 31, 92–100.
Ren, W. (2007). Pulsing RoQ DDoS attacking and defense scheme in mobile ad hoc networks. International Journal of Network Security, 4(2), 227–234.
Samfat, D., Molva, R., & Tsudik, G. (1994). Authentication of mobile users. IEEE Network, 8, 26–34.
Stach, J. F., Park, E. K., & Makki, K. (1999). Performance of an enhanced GSM protocol supporting non-repudiation of service. Computer Communications, 22, 675–680.
Stallings, W. (1999). Cryptography and network security: principles and practice (2nd edn.). New York: Prentice Hall.
Xenakis, C. (2008). Security measures and weaknesses of the GPRS security architecture. International Journal of Network Security, 6(2), 158–169.
Yang, C.-Y., & Shiu, C.-Y. (2005). A secure mobile IP registration protocol. International Journal of Network Security, 1(1), 38–45.
Zwierko, A., & Kotulski, Z. (2007). Integrity of mobile agents: a new approach. International Journal of Network Security, 4(2), 201–211.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lee, CC., Liao, IE. & Hwang, MS. An efficient authentication protocol for mobile communications. Telecommun Syst 46, 31–41 (2011). https://doi.org/10.1007/s11235-009-9276-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-009-9276-4