Abstract
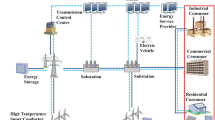
Smart Grid is a promising technology to efficiently manage the power use, transmission and production. An efficient and dependable smart power grid relies on the secure and reliable real-time data collection and transmission service provided by an underlying backbone communication network. Cognitive radio network is an emerging wireless communication technology that fits communication needs in smart grid. However, the cognitive radio is vulnerable to jamming attacks that can disturb the real time communication. The loss of the timely information from the remotely distributedly deployed sensors can cause the loss of control of the system. In this paper, we focus on the availability of the communication services provided by the cognitive radio nodes deployed over the smart grid. We consider the jamming attacks to this wireless network. We propose to defeat the jamming attacks by introducing the combined online optimization and linear programming to the smart grid to enable the system to heal automatically from the jamming attack.




Similar content being viewed by others
References
Ranganathan, R., Qiu, R., Hu, Z., Hou, S., Pazos-Revilla, M., Zheng, G., et al. (2011). Cognitive radio for smart grid: Theory, algorithms, and security. International Journal of Digital Multimedia Broadcasting, 1–14.
Qiu, M., & Sha, E. H. M. (2009). Cost minimization while satisfying hard/soft timing constraints for heterogeneous embedded systems. ACM Transactions on Design Automation of Electronic Systems (TODAES), 14(2), 1–30 Mar 2009. ACM TODAES 2011 Best Paper Award.
Qiu, M., Gao, W., Chen, M., Niu, J., & Zhang, L. (2011). Energy efficient security algorithm for power grid wide area monitoring systems. IEEE Transactions on Smart Grid, 2(4), 715–723.
Su, H., Qiu, M., & Wang, H. (2012). Secure wireless communication system for smart grid with rechargeable electric vehicles. IEEE Communication Magazine, 50(8), 62–68.
Ali-Yahiya, T., Beylot, A. L., & Pujolle, G. (2010). Downlink resource allocation strategies for OFDMA based mobile WiMAX. Telecommunication Systems, 44, 29–37.
Zhou, L., Wang, X., Tu, W., Mutean, G., & Geller, B. (2010). Distributed scheduling scheme for video streaming over multi-channel multi-radio multi-hop wireless networks. IEEE Journal on Selected Areas in Communications, 28(3), 409–419.
Zhou, L., Chao, H.-C., & Vasilakos, A. (2011). Joint forensics-scheduling strategy for delay-sensitive multimedia applications over heterogeneous networks. IEEE Journal on Selected Areas in Communications, 29(7), 1358–1367.
Zhou, L., & Chen, H.-H. (2011). On multimedia scheduling with constrained control channels. IEEE Transactions on Multimedia, 13(5), 1040–1051.
Ghassemi, A., Bavarian, S., & Lampe, L. (2010). Cognitive radio for smart grid communications. Proc. of Smart Grid Communications (SmartGridComm) (pp. 297–302), Oct. 2010.
Edison Electric Institute (2008). Renewable energy: Growth and challenges in the electric industry. Edison Electric Institute Technique Report, 2008.
Office of the National Coordinator for Smart Grid Interoperability (2010). NIST framework and roadmap for smart grid interoperability standards, Release 1.0, Jan 2010.
Javidi, T., Krishnamachari, B., Zhao, Q., & Liu, M. (2008). Optimality of myopic sensing in multi-channel opportunistic access. Proc. of International Conference on Communication (pp. 2107–2112).
Zhao, Q., Krishnamachari, B., & Liu, K. (2008). On myopic sensing for multi-channel opportunistic access: structure, optimality, and performance. IEEE Transactions on Wireless Communications, 7(12–2), 5431–5440.
Ahmad, S. H. A., Liu, M., Javidi, T., Zhao, Q., & Krishnamachari, B. (2008). Optimality of myopic sensing in multi-channel opportunistic access. CoRR (vol. abs/0811.0637).
Ghosh, B. (2009). How vulnerable is the power grid? TIME, Apr 2009.
Hu, Y., Perrig, A., & Johnson, D. B. (2003). Packet leashes: A defense against wormhole attacks in wireless networks. Proc. of IEEE INFOCOM (Vol. 3, pp. 1976–1986).
Papadimitratos, P., & Haas, Z. J. (2006). Secure data communication in mobile ad hoc networks. IEEE Journal on Selected Areas in Communications, 24(2), 343–356.
Humphreys, T. E., Kintner, P. M., Psiaki, M. L., Ledvina, B., & O’ Hanlon, B. (2009). Assessing the spoofing threat. http://www.gpsworld.com/defense/security-surveillance/assessing-spoofing-threat-3171
Strasser, M., Pöpper, C., Capkun, S., & Cagalj, M. (2008). Jamming-resistant key establishment using uncoordinated frequency hopping. Proc. of IEEE Symposium on Security and Privacy (pp. 64–78).
György, A., Linder, T., Lugosi, G., & Ottucsák, G. (2007). The on-line shortest path problem under partial monitoring. Journal of Machine Learning Research, 8, 2369–2403.
Acknowledgments
This work was supported in part by CNS-1457506, CNS-1359557, and NSF CNS-1249223; State Key Laboratory of Software Development Environment Grant BUAA SKLSDE-2012ZX-17, NSFC 61170296, NSFC 60873241, NSFC 61190120, New Century Excellent Talents in University NECT-09-0028; NSFC 61170077, SZ-HK Innovation Circle proj. ZYB200907060012A, NSFC Guangdong:10351806001000000, S & T proj. of SZ JC200903120046A; NSFC 61070002 and MOE-INTEL-10-02; NSF CNS-0915762 (CSR), CCF-08452578 (CAREER), CNS-0917137 (CSR).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Niu, J., Ming, Z., Qiu, M. et al. Defending jamming attack in wide-area monitoring system for smart grid. Telecommun Syst 60, 159–167 (2015). https://doi.org/10.1007/s11235-014-9930-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-014-9930-3