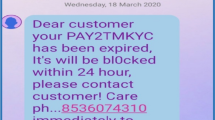
Abstract
Recently the mobile computing technology has been generally used to people with the development of the IT technology. The mobile computing environment has provided a convenient environment via the intelligent devices such as tablet PC, smartphone, etc. However, many security threats in the mobile computing environment exist. Therefore, secure elements to protect against security threats are needed. In particular, Short Message Service phishing (Smishing) damage has continued to increase with the normalization of mobile computing environment. We discuss and analyze the security considerations about Smishing in mobile computing environments. In addition, we propose an enhanced security model for detecting Smishing attack (we called “S-Detector”). The proposed model is applied to a Naive Bayes classifier to improve the Smishing attack detection in smart devices. This model distinguishes normal text message and Smishing message. And this is mainly used to filter by using statistical learning method. As a result, it is possible to analyze a text message and effectively detect SMS phishing. Finally, we demonstrate the efficiency of our model through the evaluation and analysis of our proposed model.





Similar content being viewed by others
References
Cyber Terror Response (2016). Center,“Coping with smishing”, 2013, http://www.netan.go.kr/. The National Police Agency.
Kang, J. Y., Yoon, J., & Kim, Y. (2013). Phishing/pharming examples and countermeasure analysis. The Korean Institute of Information Scientists and Engineers, 12(2), 171–180.
Lee, J., Cho, D., & Lee, J. (2011). An integrity verification method for secure application on the smartphone. The Korean Institute of Information Technology, 9(10), 223–228.
Zhou, Y., & Jiang, X. (2012). Dissecting android malware: Characterization and evolution. In IEEE Symposium on Security and Privacy (pp. 95–109).
Kang, S., & Kim, S. (2013). Study on the personal Information Retrieval of Smartphone Messenger Service. Korea Institute of Information Security and Cryptology, 23(1), 97–107.
Wu, L., Du, X., & Wu, J. (2014). MobiFish: A lightweight anti-phishing scheme for mobile phones. 2014 In 23rd International Conference on Computer Communication and Networks (ICCCN) (pp. 1–8).
Bottazzi, G., Casalicchio, E., Cingolani, D., Marturana, F., & Piu, M. (2015). MP-Shield: A framework for phishing detection in mobile devices. In 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing (CIT/IUCC/DASC/PICOM), IEEE (pp. 1977–1983).
Zhang, J., & Wang, Y. (2012). A real-time automatic detection of phishing URLs. In: 2012 2nd International Conference on Computer Science and Network Technology (ICCSNT), IEEE (pp. 1212–1216).
Foozy, C. F. M., Ahmad, R., & Abdollah, M. F. (2013). Phishing detection taxonomy for mobile device. International Journal of Computer Science Issues (IJCSI), 10(1), 338–344.
Jiayi, M., Cui, A., & Rao, J. (2013). Android mobile security–threats and protection. In International Conference on Computer, Networks and Communication Engineering (ICCNCE 2013) (pp. 683-686). Atlantis Press, Paris.
Lee, D. G., Lee, S. Z., & Rim, H. C. (2003). An efficient method for Korean noun extraction using noun patterns. Journal of KIISE: Software and Applications, 30(1), 173–183.
Yang, S. H., & Kim, Y. S. (2003). A high-speed Korean morphological analysis method based on pre-analyzed partial words. Journal of KIISE: Software and Applications, 27(3), 290–301.
Almeida, T. A., Almeida, J., & Yamakami, A. (2011). Spam filtering: How the dimensionality reduction affects the accuracy of Naive Bayes classifiers. Journal of Internet Services and Applications, 1(3), 183–200.
Kim, H., & Lee, S. (2013). The phoneme Kernel technique based on support vector machine for emotion classification of mobile texts. Journal of KIISE: Software and Applications, 40(6), 350–355.
Raveendranath, R., Rajamani, V., Babu, A. J., & Datta, S. K. (2014). Android malware attacks and countermeasures: Current and future directions. In 2014 International Conference on Control, Instrumentation, Communication and Computational Technologies (ICCICCT) (pp. 137–143).
Luo, T., Syracuse, H., Du, W., Wang, Y., & Yin, H. (2011). Attacks on WebView in the Android system. In Proceedings of the 27th Annual Computer Security Applications Conference. ACM, (pp. 343–352).
ALYac Android. http://www.alyac.com/public_android/ (2016).
Hauri, Smishing Defender. http://www.hauri.co.kr/support/hauriNews_view.html?intSeq=303&page=7&keyfield=&key. (2016).
Acknowledgements
This research was supported by the MSIP (Ministry of Science, ICT and Future Planning), Korea, under the ITRC (Information Technology Research Center) support program (IITP-2016-H8501-16-1014) supervised by the IITP (Institute for Information & Communications Technology Promotion)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Joo, J.W., Moon, S.Y., Singh, S. et al. S-Detector: an enhanced security model for detecting Smishing attack for mobile computing. Telecommun Syst 66, 29–38 (2017). https://doi.org/10.1007/s11235-016-0269-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-016-0269-9