Abstract
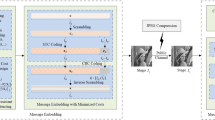
The class of stego systems based on error correcting codes is one of the alternatives to conventional steganographic systems. In the context of code based steganography, the BCH code based stego system offers a very smart solution based on the hardness of syndrome decoding. It has been shown that syndrome decoding problem is able to resist the existing steganalysis attacks. In this paper, we introduce an attack against these systems using a new syndrome decoding method. This scheme also generates a direct estimate of the secret message bit locations by exploiting the embedding patterns. This new attack notably points out that BCH code based stego system with its original parameters do not provide sufficient security.


Similar content being viewed by others
References
Anderson, R. (Ed.) (1996). Stretching the limits of steganography. In Proceedings of the first international workshop on information hiding, Cambridge, UK, May 30–June 1, 1996 (pp. 39–48). Berlin: Springer.
Anderson, R. J., & Petitcolas, F. A. (1998). On the limits of steganography. IEEE Journal on Selected Areas in Communications, 16(4), 474–481.
Augot, D., Barbier, M., & Fontaine, C. (2011). Ensuring message embedding in wet paper steganography. In L. Chen (Ed.), Proceedings of the 13th IMA international conference on cryptography and coding, Oxford, UK (pp. 244–258). Berlin: Springer.
Barg, A., Krouk, E., & Van Tilborg, H. C. (1999). On the complexity of minimum distance decoding of long linear codes. IEEE Transactions on Information Theory, 45(5), 1392–1405.
Barreto, P. S., & Misoczki, R. (2010). A new one-time signature scheme from syndrome decoding. IACR Cryptology ePrint Archive, http://eprint.iacr.org/2010/017.pdf.
Bierbrauer, J., & Fridrich, J. (2008). Constructing good covering codes for applications in steganography. In Y. Q. Shi (Ed.), Transactions on data hiding and multimedia security III (pp. 1–22). Berlin: Springer.
Canteaut, A. (1995). A new algorithm for finding minimum-weight words in large linear codes. In C. Boyd (Ed.), 5th IMA Conference, Cirencester, UK, December 18–20, 1995 (pp. 205–212). Berlin: Springer.
Cheung, K. M. (1989). The weight distribution and randomness of linear codes. Telecommunication and Data Acquisition Progress Report. Accession Number: 89N27892.
Cozzens, M., & Miller, S. J. (2013). The mathematics of encryption: An elementary introduction (Vol. 29). Providence: American Mathematical Society.
Crandall, R. (1998). Some notes on steganography. http://os.inf.tu-dresden.de/~westfeld/crandall.pdf. Accessed December 28 2013.
Filler, T., & Fridrich, J. (2009). Wet ZZW construction for steganography. InFirst IEEE international workshop on information forensics and security (pp. 6–9).
Fridrich, J., Goljan, M., Lisonek, P., & Soukal, D. (2005). Writing on wet paper. IEEE Transactions on Signal Processing, 53(10), 3923–3935.
Fridrich, J., & Soukal, D. (2006). Matrix embedding for large payloads. In Electronic imaging (pp. 60721W-60721W). International Society for Optics and Photonics.
Fridrich, J. (2009). Steganography in digital media: Principles, algorithms, and applications. Cambridge: Cambridge University Press.
Galand, F., & Kabatiansky, G. (2003). Information hiding by coverings. In IEEE proceedings of information theory workshop, 2003 (pp. 151–154). IEEE.
MacWilliams, F. J., & Sloane, N. J. A. (1977). The theory of error-correcting codes (Vol. 16). Amstedrdam: Elsevier.
McEliece, R. J. (1978). A public-key cryptosystem based on algebraic coding theory. DSN Progress Report, 42(44), 114–116.
Munuera, C. (2012). Steganography from a coding theory point of view. In E. Martinez-Moro (Ed.), Algebraic geometry modeling in information theory. Singapore: World Scientific.
Munuera, C., & León, W. O. (2013). Decoding of codes for applications to steganography. In Proceedings of the applications of computer algebra (ACA) (p. 135). Málaga.
Nagaraja, S., Houmansadr, A., Piyawongwisal, P., Singh, V., Agarwal, P., & Borisov, N. (2011). Stegobot: a covert social network botnet. In T. Filler, T. Pevný, S. Craver, & A. Ker (Eds.), 13th International conference on information hiding, Prague, Czech Republic, May 18–20, 2011 (pp. 299–313). Berlin: Springer.
Niebuhr, R. (2011). Statistical decoding of codes over \({\mathbb{F}}_q\). In B.-Y. Yang (Ed.), 4th International workshop on post-quantum cryptography, Taipei, Taiwan (pp. 217–227). Berlin: Springer.
Schönfeld, D., & Winkler, A. (2006). Embedding with syndrome coding based on BCH codes. In ACM proceedings of the 8th workshop on multimedia and security (pp. 214–223).
Schönfeld, D., & Winkler, A. (2007). Reducing the complexity of syndrome coding for embedding. In T. Furon, F. Cayre, & G. Doërr, P. Bas (Eds.), 9th International workshop on information hiding, Saint Malo, France, June 11–13, 2007 (pp. 145–158). Berlin: Springer.
Stern, J. (1989). A method for finding codewords of small weight. In G. Cohen & J. Wolfmann (Eds.), Coding theory and applications, 3rd international colloquium, Toulon, France, November 2–4, 1988 (pp. 106–113). Berlin: Springer.
Shafiq, M. Z., Khayam, S. A., & Farooq, M. (2008). Embedded malware detection using markov n-grams. In D. Zamboni (Ed.), Detection of intrusions and malware, and vulnerability assessment (pp. 88–107). Berlin: Springer.
Zhang, W., & Li, S. (2008). A coding problem in steganography. Designs, Codes and Cryptography, 46(1), 67–81.
Zhang, W., & Zhu, X. (2009). Improving the embedding efficiency of wet paper codes by paper folding. IEEE Signal Processing Letters, 16(9), 794–797.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Natarajan, V., Anitha, R. Steganalysis of BCH code based stego schemes. Telecommun Syst 69, 207–216 (2018). https://doi.org/10.1007/s11235-018-0457-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-018-0457-x