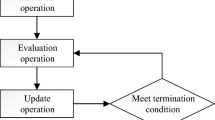
Abstract
Due to the development of computer controlled tools and expansion of integrated computing applications, more and more controller functions are turning to software implementations. A novel controlling algorithm is designed for continuous optimization tasks. However, they are used to thoroughly optimize and apply different areas. The most intelligent swarm algorithms have been designed for continuous optimization problems. However, they have been applied to discreet optimization and applications in different areas. This article gives experimental results on the control of swarm robots with the help of integrated control model (ICM), around its own axis. Such methodology is quite impressive in development of applications for surveillance, path planning, intruder and obstacle detection, model errors in communication to remove uncertainty. The ICM control design performance is based on comprehensive swarm robot model for the identification of actuators from testing data. The same ICM controllers are designed to be compared with the PID controllers in a variety of tests and collected feedback found 12.37%, 8.69% and 12.09% improved on the basis of thrust produced in the propellers for surveillance.














Similar content being viewed by others
References
Christensen, A. L., et al. (2013). Communication and control for swarms of aquatic surface drones: the HANCAD and CORATAM projects (pp. 1–6).
Cigla, C., Brockers, R., & Matthies, L. (2017). Gaussian mixture models for temporal depth fusion. In Proceedings—2017 IEEE winter conference on applications of computer vision, WACV 2017, no. October (pp. 889–897).
Saeed, N., Celik, A., Al-Naffouri, T. Y., & Alouini, M.-S. (2018). Underwater optical sensor networks localization with limited connectivity. In ICASSP, IEEE international conference on acoustics, speech and signal processing—Proceedings. February (pp. 3804–3808), 2018.
Brambilla, M., Ferrante, E., Birattari, M., & Dorigo, M. (2013). Swarm robotics: A review from the swarm engineering perspective. Swarm Intelligence, 7(1), 1–41.
Novara, C., Canuto, E., & Carlucci, D. (2016). Control of systems with sector-bounded nonlinearities: robust stability and command effort minimization by disturbance rejection. Control Theory and Technology, 14(3), 209–223.
Freidovich, L. B., & Khalil, H. K. (2006). Robust feedback linearization using extended high-gain observers. In Proceedings of the 45th IEEE conference on decision and control, no. January 2007 (pp. 983–988).
Khan, G. R., Durrani, H. R., Awan, I. I., Qadir, M., & Khan, Z. (2014). Data Mining Clustering Analysis is a Source of Finding Similar Function of Genetic Factor, Genome and Protein. Higher Education, 4(7), 151–159.
Pinto, M. D., Wilhelm, E. N., Tricoli, V., Pinto, R. S., & Blazevich, A. J. (2014). Differential effects of 30-vs. 60-second static muscle stretching on vertical jump performance. The Journal of Strength and Conditioning Research, 28(12), 3440–3446.
Westwood, J. (2004). Marine and ocean technology worldwide market potential what are the marine industries ? What is their value ? What are their growth prospects ? no. April.
Saltz, L. B., et al. (2008). Bevacizumab in combination with oxaliplatin-based chemotherapy as first-line therapy in metastatic colorectal cancer: A randomized phase III study. Journal of Clinical Oncology, 26(12), 2013–2019.
Ikado, K., et al. (2006). Evidence of the purely leptonic decay B- → τ-ν̄τ. Physical Review Letters, 97(25), 1–6.
Ahmadzadeh, S., Ghanavati, M., Branch, A., & Branch, M. (2012). Navigation of mobile robot using the pso particle swarm. Journal of Academic and Applied Studies (JAAS), 2(1), 32–38.
Christensen, A. L., O’Grady, R., & Dorigo, M. (2009). From Fireflies to Fault Tolerant Swarms of Robots. IEEE Transactions on Evolutionary Computation, 13(4), 754–766.
Haseeb, K., Arshad, M., Yasin, S., & Abbas, N. (2010). A survey of VANET’ s authentication (vol. 1).
Saeed, N., Celik, A., & Al-naffouri, T. Y. (2018). Underwater optical wireless communications, networking, and localization: A survey (pp. 1–40).
Lotufo, M. A., Perez-Montegro, C., Colangelo, L., Canuto, E., & Novara, C. (2016). Identification and control of a quadrotor from experimental data. In 2016 24th Mediterranean conference on control and automation (pp. 895–900).
Perez-Montenegro, C., Lotufo, M., & Canuto, E. (2013). Control architecture and simulation of the borea quadrotor. In IFAC proceedings (vol. 2, no. PART 1, pp. 168–173).
Tong, L., & Wu, Q. (2014). Intrusion feature selection algorithm based on particle swarm optimization. Jisuanji Gongcheng yu Yingyong (Computer Engineering and Applications), 49(7), 89–92.
Bai, E. (2002). A blind approach to the Hammerstein – Wiener model identification. Automatica, 38, 967–979.
Adhy, S., & Panda, S. (2017). A hybrid stochastic fractal search and pattern search technique based cascade PI-PD controller for automatic generation control of multi-source power systems in presence of plug in electric vehicles. CAAI Transactions on Intelligence Technology, 2(1), 12–25.
Saska, M., Vonásek, V., Chudoba, J., Thomas, J., Loianno, G., & Kumar, V. (2016). Swarm distribution and deployment for cooperative surveillance by micro-aerial vehicles. Journal of Intelligent and Robotic Systems: Theory and Applications, 84(1–4), 469–492.
Tarapore, D., & Christensen, A. (2013). Abnormality detection in multiagent systems inspired by the adaptive immune system. In Multi-agent systems (pp. 6–10).
Hu, W., Yao, L. G., & Hua, Z. Z. (2008). Optimization of sheet metal forming processes by adaptive response surface based on intelligent sampling method. Journal of Materials Processing Technology, 197(1–3), 77–88.
Deepak, B., & Parhi, D. (2012). PSO based path planner of an autonomous mobile robot. Open Computer Science, 2(2), 152–168.
Frantz, N. R. (2005). Swarm intelligence for autonomous UAV control. In Computer Engineering.
Design, I., & Rath, M. K. (2015). Motion control of automated mobile motion control of automated mobile.
Mellinger, D., Michael, N., & Kumar, V. (2014). Trajectory generation and control for precise aggressive maneuvers with quadrotors. Springer Tracts in Advanced Robotics, 79, 361–373.
Valentin, J. et al. (2016). Learning to navigate the energy landscape. In Proceedings—2016 4th international conference 3D vision, 3DV 2016 (pp. 323–332).
Fragoso, A. T., Cigla, C., Brockers, R., & Matthies, L. H. (2018). Dynamically feasible motion planning for micro air vehicles using an egocylinder. In Springer tracts in advanced robotics (pp. 1–14).
Deters, R. W., & Selig, M. S. (2008). Static testing of micro propellers. In 26th AIAA applications aerodynamics conference.
Xue, S., & Zeng, J. (2009). Controlling swarm robots for target search in parallel and asynchronously. International Journal of Modelling Identification and Control, 8(4), 353–360.
Cao, Y. U., Fukunaga, A. S., Kahng, A. B., & Meng, F. (1997). Cooperative mobile robotics: antecedents and directions. In Proceedings of the 1995 IEEE/RSJ international conference on intelligence robotic systems humun robot interactions cooperation robot (vol. 1, pp. 226–234).
Hsieh, M. A., Kumar, V., & Chaimowicz, L. (2008). Decentralized controllers for shape generation with robotic swarms. Robotica, 26(5), 691–701.
Krieger, M. J. B., Billeter, J. B., & Keller, L. (2000). Ant-like task allocation and recruitment in cooperative robots. Nature, 406(6799), 992–995.
Günes, M., Sorges, U., & Bouazizi, I. (2002). ARA—The ant-colony based routing algorithm for MANETs. In ICPPW’02 Proceedings of the 2002 international conference on parallel process work, no. November (pp. 79–85).
Dinh, H. T., & Holvoet, T. (2017). Dancing UAVs: Using linear programming to model movement behavior with safety requirements (pp. 326–335).
Savsani, P., Jhala, R. L., & Savsani, V. J. (2014). Comparative study of different metaheuristics for the trajectory planning of a robotic arm. IEEE Systems Journal, 10(2), 1–12.
Kavdia, M., & Chindambaram, M. (1996). On-Line Controller Tuning For Unstable Systems. Computers & Chemical Engineering, 20(3), 301–305.
Acknowledgements
I might want to give my sincere tribute to Prof. Dr. Carlo Novara, Department of Control and Computing Engineering (DAUIN), Politecnico di Torino, Italy and Shakeel Qadar Khan, Secretary KPK, Peshawar, Pakistan. Without their participation, support and direction, I would not have the capacity to finish this exploration work in a positive heading.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Khan, G.R., Novara, C., Haseeb, K. et al. A novel algorithm for integrated control model using swarm robots for intruder detection and rescue schedules. Telecommun Syst 72, 273–284 (2019). https://doi.org/10.1007/s11235-019-00569-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-019-00569-5