Abstract
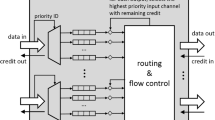
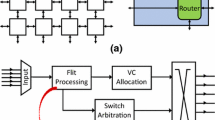
The Network-on-Chip (NoC) architecture is an interconnect network with a good performance and scalability potential. Thus, it comes as no surprise that NoCs are among the most popular interconnect mediums in nowadays available many-core platforms. Over the years, the real-time community has been attempting to make NoCs amenable to the real-time analysis. One such approach advocates to employ virtual channels. Virtual channels are hardware resources that can be used as an infrastructure to facilitate flit-level preemptions between communication traffic flows. This gives the possibility to implement priority-preemptive arbitration policies in routers, which is a promising step towards deriving real-time guarantees for NoC traffic. So far, various aspects of priority-preemptive NoCs were studied, such as arbitration, priority assignment, routing, and workload mapping. Due to a potentially large solution space, the majority of available techniques are heuristic-centric, that is, either pure heuristics, or heuristic-based search strategies are used. Such approaches may lead to an inefficient use of hardware resources, and may cause a resource over-provisioning as well as unnecessarily high design-cost expenses. Motivated by this reality, we take a different approach, and propose an integer linear program to solve the problems of priority assignment and routing of NoC traffic. The proposed method finds optimal routes and priorities, but also allows to reduce the search space (and the computation time) by fixing either priorities or routes, and derive optimal values for remaining parameters. This framework is used to experimentally evaluate both the scalability of the proposed method, as well as the efficiency of existing priority assignment and routing techniques.











Similar content being viewed by others
Notes
Note, that the existence of at most one packet of each flow, at any time instant, which is the fundamental requirement of the constrained workload model, can be easily assured e.g. by a proper configuration of the traffic injection mechanism in source routers.
Note, that in our formulation there exist binary variables, and that linear programs with integer and binary variables are in the literature often called Mixed Integer Linear Programs (MILP).
Although not conforming to the traditional ILP programming style, for clarity purposes, we use the equality sign in constraints. Note, that each of these constraints should be rewritten as two additional ones, one with the sign \( \le \), and another with the sign \(\ge \).
In Fig. 8, the box-edges represent the \( 25^{th} \) percentile (\( q_1 \)) and the \( 75^{th} \) percentile (\( q_3 \)), while every data input more than an interquartile range away from the box (i.e. less than \( q_1 - (q_3 - q_1) \), or greater than \( q_3 + (q_3 - q_1) \)) is considered an outlier.
References
Benini L, De Micheli G (2002) Networks on chips: a new soc paradigm. Comput J 35(1):70–78
Burns A, Harbin J, Indrusiak L (2014) A wormhole noc protocol for mixed criticality systems. In: Proceedings of the 35th IEEE real-time systems symposium
Dally W (1992) Virtual-channel flow control. IEEE Trans Parallel Distrib Syst 3(2):194–205
Dally W, Seitz C (1987) Deadlock-free message routing in multiprocessor interconnection networks. IEEE Trans Comput
Dasari D, Nikolić B, Nelis V, Petters SM (2013) Noc contention analysis using a branch and prune algorithm. ACM Trans Embed Comput Syst
Diemer J, Ernst R (2010) Back suction: Service guarantees for latency-sensitive on-chip networks. In: International symposium on Networks-on-Chip, pp 155–162
de Dinechin BD, van Amstel D, Poulhiès M, Lager G (2014a) Time-critical computing on a single-chip massively parallel processor. In: Proceedings of the 17th conference on design automation and test in Europe
de Dinechin BD, Durand Y, van Amstel D, Ghiti A (2014b) Guaranteed services of the noc of a manycore processor. In: Proceedings of the international workshop on network on chip architectures
Ferrandiz T, Frances F, Fraboul C (2011) A network calculus model for spacewire networks. In: Proceedings of the 17th IEEE conference on embedded and real-time computing and applications, vol 1, pp 295–299
Goossens K, Dielissen J, Radulescu A (2005) Aethereal network on chip: concepts, architectures, and implementations. IEEE Des Test Comput 22(5):414–421
Hu J, Marculescu R (2003) Energy-aware mapping for tile-based noc architectures under performance constraints. In: Proceedings of the 8th Asia and south pacific design automation conference
IBM (2016) ILOG CPLEX Optimizer. www.ibm.com/software/commerce/optimization/cplex-optimizer
Indrusiak LS (2014) End-to-end schedulability tests for multiprocessor embedded systems based on networks-on-chip with priority-preemptive arbitration. J Syst Archit 60(7):553–561
Indrusiak LS, Harbin J, Burns A (2015) Average and worst-case latency improvements in mixed-criticality wormhole networks-on-chip. In: Proceedings of the 27th euromicro conference on real-time systems
Indrusiak LS, Burns A, Nikolić B (2016) Analysis of buffering effects on hard real-time priority-preemptive wormhole networks. Technical report arXiv:1606.02942
Intel (2010) Single-Chip-Cloud Computer. www.intel.com/content/dam/www/public/us/en/documents/technology-briefs/intel-labs-single-chip-cloud-article
Intel (2013) Intel® Xeon Phi™. http://www.intel.com/content/www/us/en/processors/xeon/xeon-phi-detail.html
Kalray (2014) MPPA-256 Manycore Processor. www.kalrayinc.com/kalray/products/#processors
Kasapaki E, Schoeberl M, Sørensen RB, Müller C, Goossens K, Sparsø J (2016) Argo: A real-time network-on-chip architecture with an efficient gals implementation. IEEE Trans Very Large Scale Integr Syst 24(2):479–492
Kashif H, Patel H (2014) Bounding buffer space requirements for real-time priority-aware networks. In: Proceedings of the 19th Asia and South Pacific design automation conference
Kashif H, Patel H (2016) Buffer space allocation for real-time priority-aware networks. In: Proceedings of the 22nd IEEE real-time and embedded technology and applications symposium
Kashif H, Gholamian S, Patel H (2014) Sla: A stage-level latency analysis for real-time communication in a pipelined resource model. IEEE Trans Comput 99
Kavaldjiev NK, Smit GJM (2003) A survey of efficient on-chip communications for society. In: Proceedings of the 4th symposium on embedded systems
Liu M, Becker M, Behnam M, Nolte T (2015a) Improved priority assignment for real-time communications in on-chip networks. In: Proceedings of the 23rd international conference on real-time networks and systems
Liu M, Behnam M, Nolte T (2015b) A stochastic response time analysis for communications in on-chip networks. In: Proceedings of the 21st IEEE conference on embedded and real-time computing and applications
Liu M, Becker M, Behnam M, Nolte T (2016a) Scheduling real-time packets with non-preemptive regions on priority-based nocs. In: Proceedings of the 22nd IEEE conference on embedded and real-time computing and applications
Liu M, Becker M, Behnam M, Nolte T (2016b) Tighter time analysis for real-time traffic in on-chip networks with shared priorities. In: International symposium on Networks-on-Chip
Mesidis P, Indrusiak L (2011) Genetic mapping of hard real-time applications onto noc-based mpsocs—a first approach. In: 6th International Workshop on Reconfigurable Communication-centric Systems-on-Chip
Millberg M, Nilsson E, Thid R, Jantsch A (2004) Guaranteed bandwidth using looped containers in temporally disjoint networks within the nostrum network on chip. In: Proceedings of the 7th conference on design automation and test in Europe, vol 2, pp 890–895
Ni LM, McKinley PK (1993) A survey of wormhole routing techniques in direct networks. Comput J 26
Nikolić B, Petters SM (2014) Edf as an arbitration policy for wormhole-switched priority-preemptive nocs—myth or fact? In: Proceedings of the 14th international conference on embedded software
Nikolić B, Ali HI, Petters SM, Pinho LM (2013) Are virtual channels the bottleneck of priority-aware wormhole-switched noc-based many-cores? In: Proceedings of the 21st international conference on real-time networks and systems
Nikolić B, Yomsi PM, Petters SM (2014) Worst-case communication delay analysis for many-cores using a limited migrative model. In: Proceedings of the 20th IEEE conference on embedded and real-time computing and applications
Nikolić B, Pinho LM, Indrusiak LS (2016) On routing flexibility of wormhole-switched priority-preemptive nocs. In: Proceedings of the 22nd ieee conference on embedded and real-time computing and applications
Paukovits C, Kopetz H (2008) Concepts of switching in the time-triggered network-on-chip. In: Proceedings of the 14th IEEE conference on embedded and real-time computing and applications, pp 120–129
Racu A, Indrusiak L (2012) Using genetic algorithms to map hard real-time on noc-based systems. In: 7th international workshop on reconfigurable communication-centric systems-on-chip
Sayuti M, Indrusiak L (2013) Real-time low-power task mapping in networks-on-chip. In: IEEE computer society annual symposium on VLSI
Schoeberl M (2007) A time-triggered network-on-chip. In: Proceedings of the 17th international conference on field-programmable logic and applications
Schoeberl M, Abbaspour S, Akesson B, Audsley N, Capasso R, Garside J, Goossens K, Goossens S, Hansen S, Heckmann R, Hepp S, Huber B, Jordan A, Kasapaki E, Knoop J, Li Y, Prokesch D, Puffitsch W, Puschner P, Rocha A, Silva C, Sparsø J, Tocchi A (2015) T-crest: Time-predictable multi-core architecture for embedded systems. J Syst Archit 61(9):449–471
Shi Z, Burns A (2008a) Priority assignment for real-time wormhole communication in on-chip networks. In: Proceedings of the 29th IEEE real-time systems symposium
Shi Z, Burns A (2008b) Real-time communication analysis for on-chip networks with wormhole switching. In: International symposium on Networks-on-Chip
Shi Z, Burns A (2010) Schedulability analysis and task mapping for real-time on-chip communication. Real Time Syst J 46(3):360–385
Shi Z, Burns A, Indrusiak LS (2010) Schedulability analysis for real time on-chip communication with wormhole switching. Int J Embed Real Time Commun Syst
Song H, Kwon B, Yoon H (1997) Throttle and preempt: a new flow control for real-time communications in wormhole networks. In: Proceedings of the 1997 international conference on parallel processing
Stefan RA, Molnos A, Goossens K (2012) daelite: A tdm noc supporting qos, multicast, and fast connection set-up. IEEE Trans Comput 63(3):583–594
Tilera (2012) TILE64™ Processor. www.mellanox.com/repository/solutions/tile-scm/docs/UG130-ArchOverview-TILE-Gx
Xiong Q, Lu Z, Wu F, Xie C (2016) Real-time analysis for wormhole noc: Revisited and revised. In: Proceedings of the 26th ACM great lakes symposium on VLSI
Acknowledgements
This work was partially supported by National Funds through FCT/MEC (Portuguese Foundation for Science and Technology) and co-financed by ERDF (European Regional Development Fund) under the PT2020 Partnership, within the CISTER Research Unit (CEC/04234); also by the European Union under the Seventh Framework Programme (FP7/2007-2013), grant agreement n\(^{\circ }\) 611016 (P-SOCRATES).
Author information
Authors and Affiliations
Corresponding author
Additional information
An erratum to this article is available at http://dx.doi.org/10.1007/s11241-017-9278-3.
Appendix
Appendix
1.1 1. Linearising the implication operator
Let A be a non-negative integer variable, and let B be a binary variable. Moreover, let us linearise the following implication: \( (B = 1) \Rightarrow (A = 0) \). That is, if B is equal to 1, then A must be zero. Conversely, if B is equal to 0, then A can have any value. This reasoning can be implemented with the following constraint:
Note, that the symbol M represents a “big enough constant”, which is commonly used in linear programming, and it is called the big M method. In our example, if B is equal to 0, then A can be any positive number and the condition is redundant. Conversely, if B is equal to 1, then A must be 0, which is the desired implication.
1.2 2. Linearising the equivalence operator
Let A and B be binary variables, and let us linearise the following equivalence: \( A \Leftrightarrow B \). This can be done with two mutual implications (the linearisation of which was explained in the previous subsection), as demonstrated below:
1.3 3. Linearising the ceiling operator
Let A be an integer variable, and let B be a decimal variable. Moreover, let us linearise the following constraint: \( A = \lceil B \rceil \). The following two constraints can be written:
In the second constraint, \( \epsilon \) is an infinitesimally small positive number. The first constraint provides a lower bound on the value of A, while the second constraint provides a corresponding upper bound. There exists only one integer in the range between B and \( B + 1 - \epsilon \), and that is the value of A.
Rights and permissions
About this article
Cite this article
Nikolić, B., Pinho, L.M. Optimal minimal routing and priority assignment for priority-preemptive real-time NoCs. Real-Time Syst 53, 578–612 (2017). https://doi.org/10.1007/s11241-017-9273-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11241-017-9273-8