Abstract
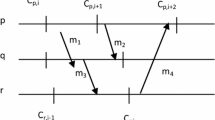
Mobility database that stores the users’ location records is very important to connect calls to mobile users on personal communication networks. If the mobility database fails, calls to mobile users may not be set up in time. This paper studies failure restoration of mobility database. We study per-user location record checkpointing schemes that checkpoint a user’s record into a non-volatile storage from time to time on a per-user basis. When the mobility database fails, the user location records can be restored from the backup storage. Numeric analysis has been used to choose the optimum checkpointing interval so that the overall cost is minimized. The cost function that we consider includes the cost of checkpointing a user’s location record and the cost of paging a user due to an invalid location record. Our results indicate that when user registration intervals are exponentially distributed, the user record should never be checkpointed if checkpointing costs more than paging. Otherwise, if paging costs more, the user record should be always checkpointed when a user registers.





Similar content being viewed by others
References
EIA/TIA. (1991). Cellular radio-telecommunication intersystem operation: Automatic roaming. BEIA/TIA Technical Report IS-41.3.
ETSI/TC. (1993). Restoration procedures, version 4.2.0. ETSI Technical Report Recommendation GSM 03.07.
Haas, Z. J., & Lin, Y.-B. (1998). On the optimizing the location update costs in the presence of database failures. ACM-Baltzer Wireless Networks, 4, 419–426.
Fang, Y., Chlamtac, I., & Fei, H. B. (2000). An active mobility database failure recovery scheme and performance analysis for PCS networks, In Conference of the IEEE Communications Society (March 2000) (pp. 757–764).
Fang, Y., Chlamtac, I., & Fei, H. B. (2000). Analytical results for optimal choice of location update interval for mobility database failure restoration in PCS networks. IEEE Transactions on Parallel and Distributed Systems, 11, 615–624.
Haas, Z. J., & Lin, Y.-B. (1999). Demand re-registration for PCS database restoration. In Proceedings Military Communications Conference 2 (October–November, 1999). (pp. 887–892).
Lin, Y.-B., & Lin, P. (1998). Performance modeling of location tracking systems. ACM Mobile Computing and Communications Review, 2, 24–27.
3GPP. (June 2001). 3rd Generation partnership project: Technical specification group services and system aspects; General packet radio service (GPRS); Service description; Stage 2, Technical Specification 3G TS 23.060 version 4.1.0.
Lin, Y.-B. (1995). Failure restoration of mobility database for personal communication networks. ACM-Baltzer Wireless Networks, 1, 365–372.
Wang, T.-P., Tseng, C.-C., & Chou, W.-K. (1997). An aggressive approach to failure restoration of PCS mobility databases. ACM Mobile Computing and Communications Review, 1, 21–28.
Lin, Y.-B. (2005). Per-user checkpointing for mobility database failure restoration. IEEE Transactions on Mobile Computing, 4, 189–194.
Varghese, G., & Lauck, A. (1997). Hashed and hierarchical timing wheels: Efficient data structures for implementing a timer facility. IEEE/ACM Transactions on Networking, 5, 824–834.
Young, J. W. (1974). A first order approximation to the optimum checkpoint interval. ACM communications, 17, 530–531.
Gelenbe, E. (1979). On the optimum checkpoint interval. Journal of the Association for Computing Machinery, 26, 259–270.
Plank, J. S., & Elwasif, W. R. (1998). Experimental assessment of workstation failures and their impact on checkpointing systems. In 28th International Symposium on Fault-Tolerant Computing (pp. 48–57).
Plank, J. S., Li, K., & Puening, M. A. (1998). Diskless checkpointing. IEEE Transactions on Parallel and Distributed Systems, 9, 972–986.
Bruno, J. L., Coffman, E. G. (1997). Optimal fault-tolerant computing on multiprocessor systems. Acta Informatica, 34, 881–904.
Bruno, J. L., Coffman, E. G., Lagarias, J. C., Richardson, T. J., & Shor, P. W. (1999). Processor shadowing: Maximizing expected throughput in fault-tolerant systems. Mathematics of Operations Research, 24, 362–382.
Coffman, E. G., Flatto, L., & Wright, P. E. (1993). A stochastic checkpoint optimization problem. SIAM Journal of Computing, 22, 650–659.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chang, HH., Chang, MF. & Tseng, CC. An analysis of location record checkpointing interval for mobility database in PCS networks. Wireless Netw 15, 991–998 (2009). https://doi.org/10.1007/s11276-008-0097-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-008-0097-2