Abstract
We extend the modeling heuristic of (Harsha et al. 2006. In IEEE IWQoS ’06, pp 178 – 187) to evaluate the performance of an IEEE 802.11e infrastructure network carrying packet telephone calls, streaming video sessions and TCP controlled file downloads, using Enhanced Distributed Channel Access (EDCA). We identify the time boundaries of activities on the channel (called channel slot boundaries) and derive a Markov Renewal Process of the contending nodes on these epochs. This is achieved by the use of attempt probabilities of the contending nodes as those obtained from the saturation fixed point analysis of (Ramaiyan et al. 2005. In Proceedings ACM Sigmetrics, ’05. Journal version accepted for publication in IEEE TON). Regenerative analysis on this MRP yields the desired steady state performance measures. We then use the MRP model to develop an effective bandwidth approach for obtaining a bound on the size of the buffer required at the video queue of the AP, such that the streaming video packet loss probability is kept to less than 1%. The results obtained match well with simulations using the network simulator, ns-2. We find that, with the default IEEE 802.11e EDCA parameters for access categories AC 1, AC 2 and AC 3, the voice call capacity decreases if even one streaming video session and one TCP file download are initiated by some wireless station. Subsequently, reducing the voice calls increases the video downlink stream throughput by 0.38 Mbps and file download capacity by 0.14 Mbps, for every voice call (for the 11 Mbps PHY). We find that a buffer size of 75KB is sufficient to ensure that the video packet loss probability at the QAP is within 1%.












Similar content being viewed by others
Notes
The basic access mechanism is one of the two access mechanisms based on the CSMA/CA (carrier sense multiple access/collision avoidance) protocol for wireless transmissions. The other is the RTS/CTS (request to send/ clear to send) mechanism. See [23] for details.
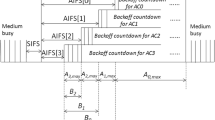
The only change will be the values of various possible channel slot lengths, L j ;j ≥ 0, due to the differences in packet transmission times.
References
IEEE 802.11e Part 11, Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications, Amend-ment 8: Medium Access Control (MAC) Quality of Service Enhancements, 11 November 2005.
Choi, S., Prado, J., Nandgopalan, S. S. N., & Mangold, S. (2003). IEEE 802.11e contention-based channel access (EDCF) performance evaluation. IEEE International Conference on Communications, 2, 1151–1156.
Garg, P., Doshi, R., Greene, R., Baker, M., Malek, M., & Cheng, X. (2003). Using IEEE 802.11e MAC for QoS over wireless. In Proceedings IEEE International Performance, Computing, and Communications Conference, pp. 537–542, 9–11 April 2003.
He, D., & Shen, C. (2003). Simulation study of IEEE 802.11e EDCF. In Vehicular Technology Conference, 2003. VTC 2003-Spring. The 57th IEEE Semiannual Volume 1, pp. 685–689, 22–25 April 2003.
Banchs, A., Azcorra, A., Garcia, C., & Cuevas, R. (2005). Applications and challenges of the 802.11e EDCA mechanism: An experimental study. IEEE Network, 19(4), 52–58.
Blum, B., He, T., & Pointurier, Y. (2001). MAC layer abstraction for simulation scalability improvements. Dept. of Computer Science, University of Virginia, Charlottsville, VA, Tech. Rep., December 2001, available at http://www.cs.virginia.edu/bmb5v/cs851/report.pdf.
Ji, Z., Zhou, J., Takai, M., & Bagrodia, R. (2004). Scalable simulation of large-scale wireless networks with bounded inaccuracies. In ACM MSWiM’04, pp. 62–69, 4–6 October 2004.
Kroller, A., Pfisterer, D., Buschmann, C., Fekete, S. P., & Fischer, S. (2005). Shawn: A New Approach to Simulating Wireless Sensor Networks, http://arxiv.org/pdf/cs.DC/050200.
Ramaiyan, V., Kumar, A., & Altman, E. (2005). Fixed point analysis of single cell IEEE 802.11e WLANs: Uniqueness, multistability and throughput differentiation. In Proceedings ACM Sigmetrics, ’05. Journal version accepted for publication in IEEE TON, ’08.
Kuo, Y., Lu, C., Wu, E., & Chen, G. (2003). An admission control strategy for differentiated services in IEEE 802.11. In Global Telecommunications Conference (GLOBECOM ’03), Vol. 2, pp. 707–712, 1–5 December 2003.
Robinson, J., & Randhawa, T. (2004). Saturation throughput analysis of IEEE 802.11e enhanced distributed coordination function. IEEE Journal on Selected Areas in Communications, 22(5), 917–928.
Zhu, H., & Chlamtac, I. (2003). An analytical model for IEEE 802.11e EDCF differential services. In Proceedings of The 12th International Conference on Computer Communications and Networks, pp. 163–168, 20–22 October 2003.
Kong, Z., Tsang, D. H. K., Bensaou, B., & Gao, D. (2004). Performance analysis of IEEE 802.11e contention-based channel access. IEEE Journal on Selected Areas in Communications, 22(10), 2095–2106.
Shankar, S., del Prado Pavon, J., & Wienert, P. (2004). Optimal packing of VoIP calls in an IEEE 802.11 a/e WLAN in the presence of QoS constraints and channel errors. In Global Telecommunications Conference, GLOBECOM ’04, Vol. 5, pp. 2974–2980, 29 November–3 December 2004.
Kumar, A., Altman, E., Miorandi, D., & Goyal, M. (2005). New Insights from a Fixed Point Analysis of Single Cell IEEE 802.11 WLANs. in Proceedings of IEEE INFOCOM 2005, pp. 1550–1561, 13 – 17 March 2005.
Clifford, P., Duffy, K., Foy, J., Leith, D. J., & Malone, D. (2006). Modeling 802.11e for Data traffic parameter design. In WiOPT ’06, 3–7 April 2006.
Harsha, S., Kumar, A., & Sharma, V. (2006). An analytical model for the capacity estimation of combined VoIP and TCP file transfers over EDCA in an IEEE 802.11e WLAN. In IEEE IWQoS ’06, pp. 178–187, 19–21 June 2006.
Wolff, R. W. (1989). Stochastic modelling and the theory of queues. Eaglewood Cliffs, NJ: Prentice Hall.
Kulkarni, V. G. (1995). Modeling and analysis of stochastic systems. London, UK: Chapman and Hall.
Kuriakose, G., Harsha, S., Kumar, A., & Sharma, V. (2008). Analytical models for capacity estimation of IEEE 802.11 WLANs using DCF for internet applications. In Wireless Networks. Springer Netherlands. doi:10.1007/s11276-007-0051-8.
Li, M., Claypool, M., & Kinicki, B. (2002). MediaPlayer versus RealPlayer—a comparison of network turbulence. In Proc. ACM Sigcomm Internet Measurement Workshop, pp. 131–136, November 2002.
Oelbaum, T., Baroncini, V., Tan, T. K., & Fenimore, C. (2004). Subjective Quality Assessment of the Emerging AVC/H.264 Video Coding Standard, http://www.itl.nist.gov/div895/papers/IBC-Paper-AVC%20VerifTestResults.pdf.
IEEE 802.11 WG, Reference number ISO/IEC 8802–11:1999(E) IEEEStd 802.11, 1999 edition.
Wiethlter, S., & Hoene, C. (2006). An IEEE 802.11e EDCF and CFB Simulation Model for ns-2. In http://www.tkn.tu-berlin.de/research/802.11e_ns2.
Prabhakaran, M. (2004). Design and Analysis of Link Scheduling Algorithms for Wireless Networks. Master’s thesis, Indian Institue of Science, Bangalore.
Tickoo, O. & Sikdar, B. (2004). A queueing model for finite load IEEE 802.11 random access MAC. In IEEE ICC, 2004, Vol. 1, pp. 175–179, 20–24 June 2004.
Kumar, A., Manjunath, D., & Kuri, J. (2004). Communication networking: An analytical approach. San Francisco: Morgan-Kaufmann (an imprint of Elsevier), May 2004.
Dembo, A., & Zeitouni, O. (1998). Large deviations techniques and applications (2nd ed.). Springer.
Harsha, S., Anand, S., Kumar, A., & Sharma, V. (2006). An analytical model for capacity evaluation of VoIP on HCCA and TCP file transfers over EDCA in an IEEE 802.11e WLAN. In International Conference on Distributed Computing and Networking (ICDCN ’06), pp. 245–256, 27–30 December 2006.
Harsha, S. (2006). Master of Engg Thesis: Performance of Multimedia Applications on IEEE 802.11e Wireless LANs, ECE Department, Indian Institue of Science, Bangalore.
Acknowledgment
This work is based on research sponsored by Intel Technology, India.
Author information
Authors and Affiliations
Corresponding author
Additional information
This is an extended version of our paper (Harsha et al. 2006. An analytical model for the capacity estimation of combined VoIP and TCP file transfers over EDCA in an IEEE 802.11e WLAN, pp. 178–187, 19–21 June 2006) in IEEE IWQoS ’06.
Appendices
Appendices
1.1 Appendix A: Expressions for various probability functions (defined in 3.2)
Define
Then,
Note that all the probability functions are denoted as functions of \(Y_j^{(v)}\) and \(Y_j^{(t)}\) even when one of them may not be there in the expression, since β and hence τ is a function of both \(Y_j^{(v)}\) and \(Y_j^{(t)}.\)
1.2 Appendix B: Numerical calculation of stationary distribution (refers to Sect. 3.2)
The transition probability matrix can be numerically generated using the above probability functions and distributions of arrivals of VoIP packets. For instance, consider N v = 5, N t = 10 and N vd = 1. Let \((Y_j^{(v)} , Y_j^{(t)}, C_j)=(3,2,0)\) be the state of the Markov chain \(\{Y_j^{(v)},Y_j^{(t)},C_j; j{\geq}0 \}\) at the end of jth channel slot. Then all three types of AC categories can contend in the next channel slot, implying that QAP v , QAP vd , QAP t , 3 QSTA v s and 2 QSTA t s may contend for the channel in the (j + 1)th channel slot.
Now let C j+1 = 0. This implies that an idle slot has occurred because none of the nodes contended for the channel. Then the number of contending QSTA t s does not change. The number of contending QSTA v s cannot decrease, but may increase by at most 2 (due to new arrival of packets). Then the state at (j + 1)th channel slot boundary can be one of the 3 states : (3,2,0), if no VoIP packet arrives, (4,2,0), if one VoIP packet arrives, and (5,2,0), if 2 VoIP packets arrive. Then the transitional probabilities are as under:
Instead, if C j+1 = 1, then this implies that an activity has occurred in the channel and that could have been either a successful transmission by one of the contending nodes or there has been collision between two or more contending nodes. Then the next states could be one of the these 10 states: (2,2,1) if QSTA v succeeded and no VoIP packet arrived; (3,2,1) if collision took place and no VoIP packet arrived or QAP v succeeded and no VoIP packet arrived or QAP vd succeeded and no VoIP packet arrived or QSTA v succeeded and 1 VoIP packet arrived; (4,2,1) if collision took place and 1 VoIP packet arrived or QAP v succeeded and 1 VoIP packet arrived or QAP vd succeeded and 1 VoIP packet arrived or QSTA v succeeded and 2 VoIP packets arrived; (5,2,1) if collision took place and 2 VoIP packets arrived or QAP v succeeded and 2 VoIP packets arrived or QAP vd succeeded and 2 VoIP packets arrived; (3,3,1) if QAP t succeeded and no VoIP packet arrived; (4,3,1) if QAP t succeeded and 1 VoIP packet arrived; (5,3,1) if QAP t succeeded and 2 VoIP packets arrived; (3,1,1) if QSTA t succeeded and no VoIP packet arrived; (4,1,1) if QSTA t succeeded and 1 VoIP packet arrived; and (5,1,1) if QSTA t succeeded and 2 VoIP packets arrived. The transition probabilities for these transitions can similarly be written (as for C j+1 = 0 case) using the probability functions and conditional probability function of VoIP packet arrivals.
Thus the transition probability matrix can be numerically worked out and then, combining with \(\sum_{n_v=0}^{N_v}\sum_{n_t=0}^{N_t}\sum_{c=0}^{1}\pi_{n_v,n_t,c}=1,\) the stationary distribution \(\varvec{\pi}\) of the Markov chain \(\{Y_j^{(v)},Y_j^{(t)},C_j; j{\geq}0 \}\) can be evaluated.
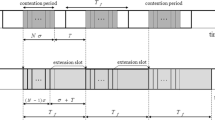
1.3 Appendix C: Mean cycle length, L j (refers to Sect. 3.3)
and
Note that the above Equations use L j in units of system slots.
Rights and permissions
About this article
Cite this article
Harsha, S., Kumar, A. & Sharma, V. An analytical model for performance evaluation of multimedia applications over EDCA in an IEEE 802.11e WLAN. Wireless Netw 16, 367–385 (2010). https://doi.org/10.1007/s11276-008-0137-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-008-0137-y