Abstract
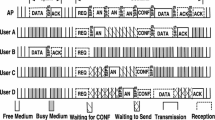
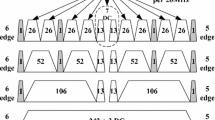
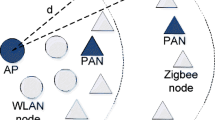
In this paper, we analytically study the dense basic service set network transmission problems in very high throughput (VHT, namely IEEE 802.11ac) wireless local area networks (WLANs) due to nervous bandwidth resources. Our contributions are threefold as follows. Firstly, we derive the closed-form expressions of throughput gains for primary channel establishment from multi-band selection using the optimal skipping rule, which balances the throughput gain from finding a good quality band with the overhead of measuring multiple bands. Secondly, in order to satisfy the quality of service of overlapping BSS users, we design a space interference avoidance mechanism, which can improve the system throughput for the whole dense WLANs. Thirdly, in order to further improve the transmission performance of dense BSS networks, we propose an unequal bandwidth transmission mechanism based on the VHT WLANs, which can not only clear the redundant network allocation vector duration timely but also use the limited bandwidth efficiently. The proposed protocols and mechanisms exploit both time and frequency diversity sufficiently, and are shown to result in typical throughput gains compared with the traditional IEEE 802.11 MAC protocol.















Similar content being viewed by others
References
Liu, Y., & Knightly, E. (2003). Opportunistic fair scheduling over multiple wireless channels. In Proceedings of IEEE INFOCOM 2003, San Francisco, CA.
Vishwanath, P., Tse, D., & Laroia, R. (2000). Opportunistic beamforming using dumb antenna. IEEE Transactions on Information Theory, 48(6), 1277–1294.
Bianchi, G. (2000). Performance analysis of the IEEE 802.11 distributed coordination function. IEEE Journal on Selected in Communications, 18(3), 535–547.
Liu, M., Li, Z. C., Guo, X. B., et al. (2008). Performance analysis and optimization of handoff algorithms in heterogeneous wireless networks. IEEE Transactions on Mobile Computing, 7(7), 846–857.
Son, K., Lee, S., Yi, Y., & Chong, S. (2011). REFIM: A practical interference management in heterogeneous wireless access networks. IEEE Journal on Selected Areas in Communications, 29(6), 1260–1272.
Zhu, J., Yang, H. C. (2011). Performance analysis of low-complexity dual-cell random beamforming transmission with user scheduling. EURASIP Journal on Wireless Communications and Networking, 2011(191), 1–11.
Li, P., Geng, X., and Fang, Y. (2009). An adaptive power controlled MAC protocol for wireless ad hoc networks. IEEE Transactions on Wireless Communications, 8(1), 226–233.
Ji, B. F., Zhu, J., Song, K., et al. (2014). Performance analysis of femtocells network with co-channel interference. Signal Processing, 100, 32–41.
Ji, B. F., Song, K., Hu, Y., et al. (2014). Cooperative transmission mechanisms in next generation WiFi: IEEE 802.11ac. International Journal of Distributed Sensor Network, 2014, 1–12.
Li, C. G., Yang, L. X., & Zhu, W. P. (2012). Joint source-and-relay beamforming for multiple-input multiple-output systems with single-antenna distributed relays. IET Communications, 6(1), 62–68.
Huang, Y. M., Xu, D. F., Yang, L. X., et al. (2008). A limited feedback precoding system with hierarchical codebook and linear receiver. IEEE Transactions on Wireless Communications, 7(12), 4843–4848.
Ji, B.F., Song, K., & Li, C.G. et al. (2012). Throughput enhancement for VHT WLANs based on two-level network allocation vector. In IEEE Globecom Workshops (pp. 881–885).
Horng, S. J., Chen, C. H., Ferng, H. W., et al. (2011). Enhancing WLAN location privacy using mobile behavior. Expert Systems with Applications, 38(1), 175–183.
Kuo, K. C., & Wu, C. W. (2014). A 5 GHz LC-VCO frequency synthesizer for unlicensed band of WiMAC. Expert Systems with Applications, 41(2), 622–634.
Choi, Y. J., Lee, N. H., et al. (2010). Exploiting multiuser MIMO in the IEEE 802.11 wireless LAN systems. IEEE Wireless Personal Communication, 54, 385–396.
Weng, C.E., & Chen C.Y. et al. (2011). Optimal performance study of IEEE 802.11 DCF with contention window. In International Conference on Broadband and Wireless Computing, Communication and Applications (pp. 505–508).
Babich, F., & Comisso, M. (2008). Optimum contention window for 802.11 networks adopting directional communications. IEEE Electronics Letters, 44(16), 994–995.
Zhou, L., Wang, X. B., Tu, W., et al. (2010). Distributed scheduling scheme for video streaming over multi-channel multi-radio multi-hop wireless networks. IEEE Journal on Selected Areas in Communications, 28(3), 409–419.
Le, L. (2010). Practical multi-channel MAC for Ad Hoc networks. In IEEE Secon (pp. 1–9).
Kwon, H., Kim, S., & Lee, B. G. (2010). Opportunistic multi-channel CSMA protocol for OFDMA systems. IEEE Transactions on Wireless Communications, 9(5), 1552–1557.
Liu, Y., Liu, M. Y., & Deng, J. (2013). Evaluating opportunistic multi-channel MAC: Is diversity gain worth the pain? IEEE Journal on Selected Areas in Communications, 31(11), 2301–2311.
Singh, S. R., & Motani, M. (2012). Cooperative multi-channel access for 802.11 mesh networks. IEEE Journal on Selected Areas in Communications, 30(9), 1684–1694.
Sabharwal, A., Khoshnevis, A., & Knightly, E. (2007). Opportunistic spectral usage: Bounds and a multi-band CSMA/CA protocol. IEEE Transactions on Networking, 15(3), 533–545.
Call, F., Conti, M., & Gregori, E. (1998). IEEE 802.11 wireless LAN: Capacity analysis and protocol enhancement. IEEE Computer and Communications Societies Proceedings INFOCOM, 1, 142–149.
Ji, B. F., & Yang, L. X. (2013). The research on solutions for OBSS interference problems in MU-MIMO transmission based on VHT WLANs. Journal of Signal Processing, 29(1), 44–53.
IEEE 802.11ac/D2.0, Draft STANDARD for Information Technology-Telecommunications and information exchange between systems: Local and metropolitan area networks-Specific requirements, Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications, Amendment 5: Enhancements for Very High Throughput for Operation in Bands below 6 GHz (2012).
Prudnikov, A. P., Brychkov, Y. A., & Marichev, O. I. (1986). Integrals and series. Gordon and Breach Science, 2, 3.
Chen, M. (2009). Stochastic process in information and communication engineering (3rd ed.). Beijing: Science Press.
Francois, B., & Bartlomiej, B. (2010). Stochastic geometry and wireless networks volume I, II. Paris: Now Publisher.
Gradshteyn, I. S., & Ryzhik, I. M. (2000). Table of integrals, series, and products (6th ed.). San Diego, CA: Academic.
Acknowledgments
This work was supported by the National Natural Science Foundation of China under Grants 61271018, 61071113 and 61201176, the National Science and Technology Major Project of China under Grant 2012ZX03004005-003, the Research Project of Jiangsu Province under Grants BK2011597 and BE2012167, SRTP of Henan University of Science and Technology and the Program for New Century Excellent Talents in University under Grant NCET-11-0088
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1
Here we will give the proof of the proposition 2. Due to the throughput gains definition and \(E[P_u]=\lambda _s\), then we can rewritten the definition as
Then we can know the distribution of throughput gains can be calculated as follows.
Appendix 2
This appendix gives the proof of the corollary 1. \(E_{SU\_gains}=E[\dfrac{x}{y}]=E[x]E[\dfrac{1}{y}]=\lambda _s\lambda _{\overline{\mathcal {N}}}E[\dfrac{1}{y}]\) Then
Then corollary 1 can be obtained.
Appendix 3
In this appendix we can give the proof of the proposition 3. Due to the redundant time of MU mode is \(T_{MU\_redun}=t-\Delta -con\_t\sum ^{G}_{u=2}\lambda _u-X\) , then the distribution of the \(T_{MU\_redun}\) contains the sum of Poisson variable \(x\) and \(m\)-Erlang variable \(y\). We firstly obtain the \(z=x+y\) distribution as follows.
Then the distribution of the \(T_{MU\_redun}\) can be obtained as follows.
Appendix 4
In this appendix we can give the proof of the corollary2. \(E_{MU\_gains}=E[\dfrac{x}{y}]=E[x]E[\dfrac{1}{y}]=\lambda _s\lambda _{\overline{\mathcal {N}}}E[\dfrac{1}{y}]\) Then
The integral term can be calculated as follows.
where \(I_1\) can be calculated using [14, 3.353.5]
where \(\int\limits ^{\infty }_{b}e^{-\lambda s}(s-b)^{m-1-j}\dfrac{1}{s}ds\) can be obtained through [14, 3.383.9]. then the results can be seen as follows.
Rights and permissions
About this article
Cite this article
Ji, B., Song, K., Zhu, J. et al. Efficient MAC protocol design and performance analysis for dense WLANs. Wireless Netw 20, 2237–2254 (2014). https://doi.org/10.1007/s11276-014-0733-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-014-0733-y