Abstract
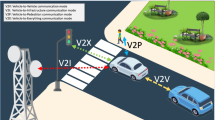
Vehicular ad-hoc networks differ from the wired networks and behave in a highly dynamic context, e.g. frequently changing signal-to-noise ratio (SNR) and security risks, which undoubtedly affects the experienced quality-of-service (QoS) and security. In this paper, we propose to dynamically balance the anticipated QoS and security for adapting to the varying vehicular context and the served applications with aims to attain a satisfactory performance rating but without compromising any security. To this end, a variant of IKEv2 called Vehicular Internet Key Exchange (VIKE) is put forward to autonomously negotiate the optimal encryption and integrity algorithms and the related profile that particularly suit to the current context with respect to the confronted SNR, security risk and application requirements. We theoretically derive the relations between the QoS and security for analytical solutions in terms of four categories of vehicular applications. The extensive numerical calculations are conducted to comprehensively investigate how the proposed VIKE responses to the various combinations of the SNR, modulation scheme and key length. The results show that the VIKE is capable of self-adapting to the vehicular context, and of contributing to the quality of communication performance without compromising any security. The proposed VIKE is expected to port the mass-deployed IKE into securing the emerging numerous vehicular applications and services.

























Similar content being viewed by others
References
Simic, M. N. (2013). Vehicular Ad Hoc Networks. In 2013 11th international conference on telecommunication in modern satellite, cable and broadcasting services (TELSIKS) IEEE, vol. 2, pp. 613–618.
Karagiannis, G., Altintas, O., Ekici, E., et al. (2011). Vehicular networking: A survey and tutorial on requirements, architectures, challenges, standards and solutions. IEEE Communications Surveys & Tutorials, 13(4), 584–616.
European Telecommunications Standards Institute. (2010). ETSI EN 302 665: Intelligent Transport System (ITS); Communication Architecture, v1.1.1.
International Organization for Standardization. (2010). ISO 21217: 2010: Intelligent Transport Systems—Communications Access for Land Mobiles (CALM)—Architecture.
European Telecommunications Standards Institute. (2011). ETSI TS 102 687: Intelligent transport systems (ITS); decentralized congestion control mechanisms for intelligent transport systems operating in the 5 GHz range; Access layer part, v1.1.1.
Alsa’deh, A., Meinel, C., & Westphal, F., et al. (2013). CGA integration into IPsec/IKEv2 authentication. In: Proceedings of the 6th international conference on security of information and networks. ACM, pp. 326–330.
Wang, Y., & Li, F. (2009). Vehicular ad hoc networks, guide to wireless ad hoc networks. In S. Misra, I. Woungang, & S. C. Misra (Eds.), Computer communications and networks (pp. 503–525). London: Springer.
Cremers, C. (2011). Key exchange in IPsec revisited: Formal analysis of IKEv1 and IKEv2 (pp. 315–334). Berlin Heidelberg: Springer.
Kaufman, C., Hoffman, P., Nir, Y., & Eronen, P. (2014). Internet key exchange protocol version 2 (IKEv2), IETF RFC7296.
Aamir, M., Zaidi, M., & Mansoor, H. (2012). Performance analysis of diffserv based quality of service in a multimedia wired network and VPN effect using OPNET. International Journal of Computer Science Issues, 9(3), 368–376.
Emmanouilidis, C., Koutsiamanis, R. A., & Tasidou, A. (2013). Mobile guides: Taxonomy of architectures, context awareness, technologies and applications. Journal of Network and Computer Applications, 36(1), 103–125.
Shankar, P., Nadeem, T., & Rosca, J., et al. (2008). Cars: Context-aware rate selection for vehicular networks. In Proceedings of IEEE International Conference on Network Protocols, pp. 1–12.
Liu, J., Sun, J., & Lv, S. (2010). A novel throughput optimization approach in wireless systems. In Proceedings of IEEE international conference on communication technology, pp. 1373–1377.
Haleem, M. A., Mathur, C. N., Chandramouli, R., et al. (2006). On optimizing the security-throughput trade-off in wireless networks with adversaries (pp. 448–458). Applied Cryptography and Network Seurity. Springer: Berlin Heidelberg.
Haleem, M. A., Mathur, C. N., Chandramouli, R., et al. (2007). Opportunistic encryption: A trade-off between security and throughput in wireless networks. IEEE Transactions on Dependable and Secure Computing, 4(4), 313–324.
Chen, J., Zeng, H., Hu, C., et al. (2011). Optimization between security and delay of quality-of-service. Journal of Network and Computer Applications, 34(2), 603–608.
Jindal, P., & Tingh, B. (2012). Study and performance evaluation of seurity-throughput tradeoff with link adaptive encryption scheme. arXiv:1211.5080.
Jindal, P., & Singh, B. (2013). Performance evaluation of security-throughput tradeoff with channel adaptive encryption. International Journal of Computer Network and Information Security, 5(1), 49–55.
Zibideh, W. Y., & Matalgah, M. M. (2012). An optimized encryption framework based on the modified-DES algorithm: A trade-off between security and throughput in wireless channels. In IEEE Radio and Wireless Symposium, pp. 419–422.
Zhou, X., Ganti, R. K., Andrews, J. G., et al. (2011). On the throughput cost of physical layer security in decentralized wireless networks. IEEE Transactions on Wireless Communications, 10(8), 2764–2775.
Wei, L., Zhu, H., Cao, Z., et al. (2014). Security and privacy for storage and computation in cloud computing. Information Sciences, 258, 371–386.
Wei, L., Zhu, H., & Cao, Z., et al. (2010). SecCloud: Bridging secure storage and computation in cloud. In IEEE international conference on distributed computing systems workshops, pp. 52–61.
Zhou, Y., Zhang, Y., Liu, H., et al. (2012). A bare-metal and asymmetric partitioning approach to client virtualization. IEEE Transactions on Services Computing, 7(1), 40–53.
Yan, Z., Zhang, P., & Vasilakos, A. V. (2014). A survey on trust management for internet of things. Journal of Network and Computer Applications, 42, 120–134.
Zhang, Y., Li, X., Yang, J., et al. (2013). A real-time dynamic key management for hierarchical wireless multimedia sensor network. Multimedia Tools and Applications, 67(1), 97–117.
Yang, H., Zhang, Y., Zhou, Y., et al. (2014). Provably secure three-party authenticated key agreement protocol using smart cards. Computer Networks, 58, 29–38.
Attar, A., Tang, H., Vasilakos, A. V., et al. (2012). A survey of security challenges in cognitive radio networks: Solutions and future research directions. Proceedings of the IEEE, 100(12), 3172–3186.
Fadlullah, Z. M., Taleb, T., Vasilakos, A. V., et al. (2010). DTRAB: Combating against attacks on encrypted protocols through traffic-feature analysis. IEEE/ACM Transactions on Networking, 18(4), 1234–1247.
Faigl, Z., Lindskog, S., & Brunstrom, A. (2010). Performance evaluation of IKEv2 authentication methods in next generation wireless networks. Security and Communication Networks, 3(1), 83–98.
Lee, D. H., & Kim, J. G. (2014). IKEv2 authentication exchange model and performance analysis in mobile IPv6 networks. Personal and Ubiquitous Computing, 18(3), 493–501.
Raza, S., Voigt, T., & Jutvik, V. (2012). Lightweight IKEv2: A key management solution for both the compressed IPSec and the IEEE 802.15.4 security. In Proceedings of the IETF workshop on smart object security.
Ruiz, P. J. F., & Skarmeta, A. F. G. (2011). Providing security using IKEv2 in a vehicular network based on WiMAX technology. In Proceedings of IEEE Consumer Communications and Networking Conference, pp. 282–286.
Tamimi, A. A. (March 2014). Performance analysis of data encryption algorithms. http://www.cs.wustl.edu/~jain/cse567-06/ftp/encryption_perf/index.html
Acknowledgments
This work was supported by National Nature Science Foundation [51175215, 61202472, 61373123]; Research Fund for the Doctoral Program of Higher Education of China [20120061120060]; China Post-doc Science Foundation [2011M500614, 2013T60328]. The Fundamental Research Funds of the Central Universities [201103136]; The Fund of Key Laboratory of Symbolic Computation and Knowledge Engineering of Ministry of Education [93K172012K05]; Foundation of State Key Laboratory of Automotive Simulation and Control [20120108]; Jilin Provincial Foundation for Young Scholars [20130522116JH]; Jilin Provincial Science and Technology Development Foundation [20120301,20130206040GX]; and Jilin Provincial International Cooperation Foundation [20140414008GH, 20150414004GH].
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Xu, J., Liu, Y., Wang, J. et al. VIKE: vehicular IKE for context-awareness. Wireless Netw 21, 1343–1362 (2015). https://doi.org/10.1007/s11276-014-0856-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-014-0856-1