Abstract
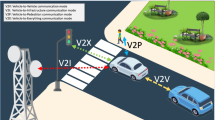
Vehicular Ad-hoc Networks (VANETs) will start becoming deployed within the next decade. Among other benefits, it is expected that VANETs will support applications and services targeting the increase of safety on the road, and assist in improving the efficiency of the road transportation network. However, several serious challenges remain to be solved before efficient and secure VANET technology becomes available, one of them been efficient authentication of messages in a VANET. In this paper, we analyse a recent authentication scheme for VANETs introduced by Lee et al. Unfortunately this scheme is vulnerable to the impersonation attack so that a malicious user can generate a valid signature on behalf of the other vehicles. Based on the attack, we propose an improved scheme and introduce a simulation expressing the efficiency of the proposed scheme.






Similar content being viewed by others
References
(2005) Vehicle safety communications project: Task 3 final report: Identify intelligent vehicle safety applications enabled by dsrc, camp vehicle safety communications consortium and others.
(2008) Car talk-[update]. IEEE Spectrum, 45, 10.
(2010) Dedicated short range communications (5.9 ghz dsrc). http://www.leearmstrong.com/DSRC/DSRCHomeset.htm.
(2010) Gnu m, the gnu multiple precision arithmetic library, 5.0.
Leee std 1609.2-2013 (revision of ieee std 1609.2-2006), 2013. doi:10.1109/IEEESTD.2013.6509896., p 1289.
Boneh. D., & Franklin, M. (2001). Identity-based encryption from the weil pairing. In: Advances in cryptology CRYPTO 2001 (pp. 213–229). New York: Springer.
Boyen, X., & Waters, B. (2006). Compact group signatures without random oracles. In: Advances in cryptology-EUROCRYPT 2006 (pp. 427–444). New York: Springer.
de Fuentes, J. M., González-Manzano, L., González-Tablas, A. I., & Blasco, J. (2014). Security models in vehicular ad-hoc networks: A survey. IETE Technical Review, 31(1), 47–64.
Freudiger, J., Raya, M., Félegyházi, M., & Papadimitratos, P., et al. (2007). Mix-zones for location privacy in vehicular networks. In: Proceedings of the first international workshop on wireless networking for intelligent transportation systems (Win-ITS).
Guo, J., Baugh, J. P., & Wang, S. (2007). A group signature based secure and privacy-preserving vehicular communication framework. Mobile Networking for Vehicular Environments, 2007, 103–108.
Hankerson, D., Vanstone, S., & Menezes, A. J. (2004). Guide to elliptic curve cryptography. New York: Springer.
He, D., Chen, C., Chan, S., & Bu, J. (2012). Analysis and improvement of a secure and efficient handover authentication for wireless networks. IEEE Communications Letters, 16(8), 1270–1273.
He, D., Chen, C., Chan, S., & Bu, J. (2012). Secure and efficient handover authentication based on bilinear pairing functions. IEEE Transactions on Wireless Communications, 11(1), 48–53.
Horng, S., Tzeng, S., Pan, Y., Fan, P., Wang, X., Li, T., et al. (2013). b-specs+: Batch verification for secure pseudonymous authentication in vanet.
Krajzewicz, D., Hertkorn, G., Rössel, C., & Wagner, P. (2002). Sumo (simulation of urban mobility). In: Proceedings of the 4th middle east symposium on simulation and modelling, pp. 183–187.
Lee, C. C., & Lai, Y. M. (2013). Toward a secure batch verification with group testing for vanet. Wireless Networks, 19(6), 1441–1449.
Lin, X., Sun, X., Ho, P. H., & Shen, X. (2007). Gsis: A secure and privacy-preserving protocol for vehicular communications. IEEE Transactions on Vehicular Technology, 56(6), 3442–3456.
Lin, X., Lu, R., Zhang, C., Zhu, H., Ho, P. H., & Shen, X. (2008). Security in vehicular ad hoc networks. IEEE Communications Magazine, 46(4), 88–95.
Lu, R., Lin, X., Zhu, H., Ho, PH., & Shen, X. (2008). Ecpp: Efficient conditional privacy preservation protocol for secure vehicular communications. In: INFOCOM 2008. The 27th IEEE conference on computer communications. IEEE.
Lu, R., Lin, X., Liang, X., & Shen, X. (2012). A dynamic privacy-preserving key management scheme for location-based services in vanets. IEEE Transactions on Intelligent Transportation Systems, 13(1), 127–139.
Miyaji, A., Nakabayashi, M., & Takano, S. (2001). New explicit conditions of elliptic curve traces for fr-reduction. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 84(5), 1234–1243.
Raya, M., & Hubaux, J. P. (2007). Securing vehicular ad hoc networks. Journal of Computer Security, 15(1), 39–68.
Scott, M. (2007). Efficient implementation of cryptographic pairings. In: Online. http://www.pairing-conference.org/2007/invited/Scottslide.pdf.
Sun, X. (2007). Anonymous, secure and efficient vehicular communications.
Sun, X., Lin, X., & Ho, PH. (2007). Secure vehicular communications based on group signature and id-based signature scheme. In: ICC’07. IEEE international conference on communications, 2007. IEEE, pp. 1539–1545.
Wasef, A., Jiang, Y., & Shen, X. (2010). Dcs: An efficient distributed-certificate-service scheme for vehicular networks. IEEE Transactions on Vehicular Technology, 59(2), 533–549.
Xiong, H., Beznosov, K., Qin, Z., & Ripeanu, M. (2010). Efficient and spontaneous privacy-preserving protocol for secure vehicular communication. In: 2010 IEEE international conference on communications (ICC). IEEE, pp. 1–6.
Xiong, H., Chen, Z., & Li, F. (2012). Efficient and multi-level privacy-preserving communication protocol for vanet. Computers & Electrical Engineering, 38(3), 573–581.
Zhang, C., Lin, X., Lu, R., & Ho, PH. (2008). Raise: An efficient rsu-aided message authentication scheme in vehicular communication networks. In: ICC’08. IEEE international conference on communications, 2008. IEEE, pp. 1451–1457.
Zhang, C., Ho, P. H., & Tapolcai, J. (2011). On batch verification with group testing for vehicular communications. Wireless Networks, 17(8), 1851–1865.
Acknowledgments
The authors would like to thank the anonymous reviewers for their helpful and constructive comments that greatly contributed to improving the final version of the paper. In addition, this work was partially supported by Iran NSF under Grant No. 92.32575.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Bayat, M., Barmshoory, M., Rahimi, M. et al. A secure authentication scheme for VANETs with batch verification. Wireless Netw 21, 1733–1743 (2015). https://doi.org/10.1007/s11276-014-0881-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-014-0881-0