Abstract
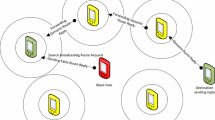
Ad Hoc network is a temporal network which is managed by autonomous nodes which have the ability to communicate with each other without having fixed network infrastructure or any central base station. Due to some reasons such as dynamic changes of the network topology, trusting the nodes to each other, lack of fixed substructure for the analysis of nodes’ behaviours and loss of specific offensive lines, this type of networks is not supportive against malicious nodes’ attacks. One of these attacks is black hole attack. In this attack, the malicious nodes absorb data packets and destroy them. Thus, it is essential to present an algorithm against the black hole attacks. This article suggests a new algorithm which enhances the security of AODV routing protocol to encounter the black hole attacks. This algorithm tries to identify malicious nodes according to nodes’ behaviours in an Ad Hoc network and delete them from routing. The suggested algorithm is simulated by NS2. The simulation results show some improvements in end-to-end delay and packet delivery rate in the suggested algorithm.


Similar content being viewed by others
References
Nguyen, H. L., & Nguyen, U. T. (2008). A study of different types of attacks on multicast in mobile ad hoc networks. Ad Hoc Networks, 6, 32–46.
Lima, M. N., dos Santos, A. L., & Pujolle, G. (2009). A survey of survivability in mobile ad hoc networks. Communications Surveys & Tutorials, IEEE, 11(1), 66–77.
Ebinger, P., & Parsons, M. (2009). Measuring the impact of attacks on the performance of mobile ad hoc networks. In Proceedings of the 6th ACM symposium on performance evaluation of wireless ad hoc, sensor, and ubiquitous networks, Tenerife, Canary Islands, Spain (pp. 163–164).
Liu, X. J. H., Wan, P., & Liu, X. (2007). A distributed and efficient flooding scheme using 1-hop information in mobile adhoc networks. IET Journals & Magazines, 18, 658–671.
Maurya, P. K., Sharma, G., Sahu, V., Roberts, A., Srivastava, M., Scholar, M., et al. (2012). An overview of AODV routing protocol. International Journal of Modern Engineering Research (IJMER), 2, 728–732.
Chhabra, M., Gupta, B., & Almomani, A. (2013). A novel solution to handle DDOS attack in MANET. Journal of Information Security, 4(3), 165–179.
Kurosawa, S., Nakayama, H., Kato, N., Jamalipour, A., & Nemoto, Y. (2007). Detecting blackhole attack on AODV-based mobile ad hoc networks by dynamic learning method. IJ Network Security, 5, 338–346.
Jamali, S. B. S. (2015). A survey over black hole attack detection in mobile ad hoc network. International Journal of Computer Science and Network Security (IJCSNS), 15, 44.
Fadlullah, Z. M., Taleb, T., Vasilakos, A. V., Guizani, M., & Kato, N. (2010). DTRAB: Combating against attacks on encrypted protocols through traffic-feature analysis. IEEE/ACM Transactions on Networking (TON), 18, 1234–1247.
Yao, G., Bi, J., & Vasilakos, A. V. (2015). Passive IP traceback: disclosing the locations of IP spoofers from path backscatter. Information Forensics and Security, IEEE Transactions on, 10, 471–484.
Yang, H., Zhang, Y., Zhou, Y., Fu, X., Liu, H., & Vasilakos, A. V. (2014). Provably secure three-party authenticated key agreement protocol using smart cards. Computer Networks, 58, 29–38.
Liu, B., Bi, J., & Vasilakos, A. V. (2014). Toward incentivizing anti-spoofing deployment. Information Forensics and Security, IEEE Transactions on, 9, 436–450.
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the Internet of Things: perspectives and challenges. Wireless Networks, 20, 2481–2501.
Yan, Z., Zhang, P., & Vasilakos, A. V. (2015). A security and trust framework for virtualized networks and software‐defined networking. Security and Communication Networks, 8(13). doi:10.1002/sec.1243.
Attar, A., Tang, H., Vasilakos, A. V., Yu, F. R., & Leung, V. (2012). A survey of security challenges in cognitive radio networks: Solutions and future research directions. Proceedings of the IEEE, 100, 3172–3186.
Nagrath, P., Aneja, S., Gupta, N., & Madria, S. (2015). Protocols for mitigating blackhole attacks in delay tolerant networks. Wireless Networks, 21(2), 1–12. doi:10.1007/s11276-015-0959-3.
Changela, H., & Lathigara, A. (2015). A survey on different existing technique for detection of black hole attack in MANETs. International Journal of Science and Research (IJSR), 4(1), 415–419.
Abdelshafy, M. A., & King, P. J. B. (2014). AODV and SAODV under attack: Performance comparison. In Ad hoc, Mobile, and Wireless Networks, Springer International Publishing (pp. 318–331).
Abdelshafy, M. A., & King, P. J. (2014). Resisting flooding attacks on AODV. SECURWARE, 2014, 25.
Tamilselvan, L., & Sankaranarayanan, V. (2008). Prevention of co-operative black hole attack in MANET. Journal of Networks, 3, 13–20.
Ramaswamy, S., Fu, H., & Sreekantaradhya, M., Dixon, J., & Nygard, K. E. (2003). Prevention of cooperative black hole attack in wireless ad hoc networks. In International conference on wireless networks.
Hesiri Weerasinghe, H. W., & Huirong Fu, H. F. (2008). Preventing cooperative black hole attacks in mobile ad hoc networks: Simulation implementation and evaluation. In International journal of software engineering and its applications (IJSEIA) (Vol. 2, pp. 39–54).
Ioannis, K., Dimitriou, T., & Freiling, F. C. (2007). Towards intrusion detection in wireless sensor networks. In Proceedings of the 13th European wireless conference.
Su, M. Y. (2011). Prevention of selective black hole attacks on mobile ad hoc networks through intrusion detection systems. Computer Communications, 34, 107–117.
Khemariya, N., & Khuntetha, A. (2013). An efficient algorithm for detection of blackhole attack in AODV based MANETs. International Journal of Computer Applications, 66(18), 18–24.
Araghi, T. K., Zamani, M., Manaf, A. B. A., Abdullah, S. M., Bojnord, H. S., & Araghi, S. K. (2013). A secure model for prevention of black hole attack in wireless mobile ad hoc networks. In 12th WSEAS international conference on applied computer and applied computational science, Malaysia.
Medadian, M., Mebadi, A., & Shahri, E. (2009). Combat with black hole attack in AODV routing protocol. In Communications (MICC), 2009 IEEE 9th Malaysia international conference on, IEEE (pp. 530–535).
Choudhary, N., & Tharani, L. (2015). Preventing black hole attack in AODV using timer-based detection mechanism. In Signal processing and communication engineering systems (SPACES), 2015 international conference on (pp. 1–4).
Ahmad, S. J., Reddy, V., Damodaram, A., & Krishna, P. R. (2015). Detection of black hole attack using code division security method. In Emerging ICT for bridging the future-proceedings of the 49th annual convention of the computer society of india CSI volume 2 (pp. 307–314).
Nandini, N., & Aggarwal, R. (2015). Prevention of black hole attack by different methods in MANET. Network, 4, 297–300.
Mandala, S., Jenni, K., Ngadi, M. A., Kamat, M., & Coulibaly, Y. (2014). Quantifying the severity of blackhole attack in wireless mobile adhoc networks. In Security in computing and communications, Springer (pp. 57–67).
Gao, H., Wu, R., Cao, M., & Zhang, C. (2014). Detection and defense technology of blackhole attacks in wireless sensor network. In Algorithms and architectures for parallel processing, Springer (pp. 601–610).
Jaisankar, N., Saravanan, R., & Swamy, K. D. (2010). A novel security approach for detecting black hole attack in MANET. In Information processing and management, Springer (pp. 217–223).
Jain, A. K., & Tokekar, V. (2015). Mitigating the effects of black hole attacks on AODV routing protocol in mobile ad hoc networks. In Pervasive computing (ICPC), 2015 international conference on (pp. 1–6).
Shi, F., Liu, W., Jin, D., & Song, J. (2014). A cluster-based countermeasure against blackhole attacks in MANETs. Telecommunication Systems, 57, 119–136.
Rashmi, A. S. (2014). Detection and prevention of black-hole attack in MANETS. International Journal of Computer Science Trends and Technology (IJCST)-Volume, 2, 204–209.
Tseng, F.-H., Chou, L.-D., & Chao, H.-C. (2011). A survey of black hole attacks in wireless mobile ad hoc networks. Human-Centric Computing and Information Sciences, 1, 1–16.
Jain, S., & Khunteta, A. (2015). Detection techniques of blackhole attack in mobile adhoc network: A survey. In Proceedings of the 2015 international conference on advanced research in computer science engineering & technology (ICARCSET 2015) (p. 47).
Medadian, M., Fardad, K., & Barazandeh, I. (2011). Discovered and removed a mass black hole attacks on mobile networks ad hoc. In 1st national conference on soft computing and information technology, Iran.
Rezaei, R., Medadian, M., & Darvishi, M. (2014). Provide a way to deal with attacks on black holes in wireless networks case: The behavior of nodes. In National conference on computer engineering and information technology management, Iran.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Shahabi, S., Ghazvini, M. & Bakhtiarian, M. A modified algorithm to improve security and performance of AODV protocol against black hole attack. Wireless Netw 22, 1505–1511 (2016). https://doi.org/10.1007/s11276-015-1032-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-015-1032-y