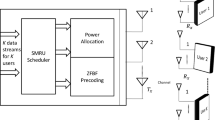
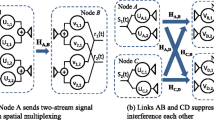
Abstract
Multiple Input Multiple Output (MIMO) based Spatial Time Division Multiple Access (STDMA) Wireless Mesh Networks (WMNs) have attracted extensive research attention. However, there are two problems in existing studies: (1) the employed MIMO link rate models are not suitable for a MIMO link of a practical STDMA WMN, and (2) the designed scheduling algorithms usually cannot take advantage of the multi-user diversity in a WMN. In this paper, we develop an analytical model for determining the MIMO link rate of an STDMA WMN. Based on a node-based slot assignment and scheduling algorithm (Chen and Lea in IEEE Trans Veh Technol 62(1):272–283, 2013), we propose a static/opportunistic hybrid scheduling framework that can exploit multi-user diversity and channel fading. The performance evaluation shows that the proposed framework has 33–46 % throughput gain over the prior joint routing and time slot assignment schemes for MIMO WMNs.





Similar content being viewed by others
References
Chen, W., & Lea, C. T. (2013). A node-based time slot assignment algorithm for stdma wireless mesh networks. IEEE Transactions on Vehicular Technology, 62(1), 272–283.
Pathak, P. H., & Dutta, R. (2010). A survey of network design problems and joint design approaches in wireless mesh networks. Communications Surveys & Tutorials, IEEE, 13(3), 396–428.
Allen, D. (1993). Hidden terminal problems in wireless lans. IEEE 802.11 Working Group Papers.
Nelson, R., & Kleinrock, L. (1985). Spatial TDMA: A collision-free multihop channel access protocol. IEEE Transactions on Communications, 33(9), 934–944.
Lee, M. J., Zheng, J., Ko, Y. B., & Shrestha, D. M. (2006). Emerging standards for wireless mesh technology. Wireless Communications, IEEE, 13(2), 56–63.
Hamdaoui, B., & Shin, K. G. (2007). Characterization and analysis of multi-hop wireless mimo network throughput. In Proceedings of the 8th ACM international symposium on Mobile ad hoc networking and computing, (pp. 120–129). ACM.
Bhatia, R., & Li, L. (2007). Throughput optimization of wireless mesh networks with mimo links. In INFOCOM 2007. 26th IEEE international conference on computer communications. IEEE, (pp. 2326–2330). IEEE.
Wang, Y., Chiu, D. M., & Lui, J. (2009). Characterizing the capacity gain of stream control scheduling in mimo wireless mesh networks. Wireless Communications and Mobile Computing, 9(6), 819–829.
Mumey, B., Tang, J., & Hahn, T. (2008). Joint stream control and scheduling in multihop wireless networks with mimo links. In ICC’08. IEEE international conference on Communications, (pp. 2921–2925). IEEE.
Bansal, M., & Trivedi, A. (2011). Joint routing and stream control scheduling in mimo-based wmns. In Proceedings of 20th international conference on Computer Communications and Networks (ICCCN), (pp. 1–6). IEEE.
Trivedi, A., & Bansal, M. D. (2010). Fair end-to-end rate allocation and stream control in mimo-based wmns. In International conference on signal processing and communications (SPCOM), (pp. 1–5). IEEE.
Chu, S., & Wang, X. (2010). Mimo-aware routing in wireless mesh networks. In INFOCOM, 2010 Proceedings IEEE, (pp. 1–9). IEEE.
Mumey, B., Tang, J., & Hahn, T. (2010). Algorithmic aspects of communications in multihop wireless networks with mimo links. In IEEE international conference on communications (ICC), (pp. 1–6). IEEE.
Hamdaoui, B., & Shin, K. G. (2009). Throughput behavior in multihop multiantenna wireless networks. IEEE Transactions on Mobile Computing, 8(11), 1480–1494.
Cheng, M., Ye, Q., & Cheng, X. (2013). Simultaneous routing and multiplexing in ad hoc networks with mimo links. In IEEE International Conference on Communications (ICC), (pp. 1414–1418). IEEE.
Hamdaoui, B., & Shin, K. G. (2010). Maximum achievable throughput in multiband multiantenna wireless mesh networks. IEEE Transactions on Mobile Computing, 9(6), 838–849.
Liu, J., Shi, Y., & Hou, Y. T. (2010). A tractable and accurate cross-layer model for multi-hop mimo networks. In INFOCOM, 2010 Proceedings IEEE, (pp. 1–9). IEEE.
Gelal, E., Ning, J., Pelechrinis, K., Kim, T. S., Broustis, Ioannis, Krishnamurthy, Srikanth V, et al. (2013). Topology control for effective interference cancellation in multiuser mimo networks. IEEE/ACM Transactions on Networking (TON), 21(2), 455–468.
Shi, Y., Liu, J., Jiang, C., Gao, C., & Hou, Y. T. (2011). An optimal link layer model for multi-hop mimo networks. In INFOCOM, 2011 Proceedings IEEE, (pp. 1916–1924). IEEE.
Cao, M., Wang, X., Kim, S. J., & Madihian, M. (2007). Multi-hop wireless backhaul networks: A cross-layer design paradigm. IEEE Journal on Selected Areas in Communications, 25(4), 738–748.
Wang, P., Matyjas, J., & Medley, M. (2011). Resource allocation in mimo-based ad hoc networks. In 45th annual conference on information sciences and systems (CISS), (pp. 1–6). IEEE.
Gao, C., Shi, Y., Hou, Y. T., & Kompella, S. (2010). On the throughput of mimo-empowered multi-hop cognitive radio networks. DTIC Document: Technical report.
Louie, R. H. Y., McKay, M. R., & Collings, I. B. (2011). Open-loop spatial multiplexing and diversity communications in ad hoc networks. IEEE Transactions on Information Theory, 57(1), 317–344.
Blum, R. S. (2003). Mimo capacity with interference. IEEE Journal on Selected Areas in Communications, 21(5), 793–801.
Kang, M., Yang, L., & Alouini, M. S. (2007). Capacity of mimo channels in the presence of co-channel interference. Wireless Communications and Mobile Computing, 7(1), 113–125.
Wang, Y., & Yue, D. W. (2009). Capacity of mimo rayleigh fading channels in the presence of interference and receive correlation. IEEE Transactions on Vehicular Technology, 58(8), 4398–4405.
Kwak, J. S., Andrews, J. G., & Lozano, A. (2007). Mimo capacity in correlated interference-limited channels. In IEEE international symposium on information theory, 2007. ISIT 2007, (pp. 106–110). IEEE.
Ma, J., Zhang, Y. J., Su, X., & Yao, Y. (2008). On capacity of wireless ad hoc networks with mimo mmse receivers. IEEE Transactions on Wireless Communications, 7(12), 5493–5503.
Ji, B., Joo, C., & Shroff, N. B. (2013). Throughput-optimal scheduling in multihop wireless networks without per-flow information. IEEE/ACM Transactions on Networking, 21(2), 634–647.
Tse, D., & Viswanath, P. (2005). Fundamentals of wireless communication. Cambridge: Cambridge University Press.
Yee, J., & Pezeshki-Esfahani, H. (2002). Understanding wireless lan performance trade-offs. Communication Systems Design, 11, 32–35.
Moschopoulos, P. G. (1985). The distribution of the sum of independent gamma random variables. Annals of the Institute of Statistical Mathematics, 37(1), 541–544.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: the derivation of (1)
To study our scheme, we need to derive the SINR of a data stream in S.
-
\(X_t^S(k)\) the signals transmitted from t in slot k with node pattern S. \(X_t^S(k)\) is an \(n_t^S\times 1\) vector with \(E(X_t^S(k)(X_t^S(k))^*)={p_t}I_{n_t}^S/{n_t^S}\), where \(M^*\) is the conjugate transpose of matrix (vector) M and \(I_n\) is an \(n\times n\) identity matrix. Furthermore, different transmitters will transmit independent data streams to their receivers, and \(E(X_p^S(k)(X_q^S(k))^*)=0_{n_p^S\times n_q^S}\) with \(p\ne q\). Here \(0_{a\times b}\) represents an \(a\times b\) matrix with all entries equal to 0;
-
\(H_{r,t}^S(k)\) the channel response function from transmitter t to receiver r in slot k;
-
\(Y_r^S(k)\): the received signal at r from all of its transmitters in slot k.
To simplify the notations, we drop S and k in the notations below and use \(T_r\) for \(T_r^S(k)\) and \(Y_r\) for \(Y_r^S\). \(Y_r\) can then be expressed as
Here \(\varsigma\) is the thermal noise at each receiving antenna and \(1_{j\times 1}\) is a \(j\times 1\) vector with all elements equal to 1. We assume a rich scattering environment and a block-wise Rayleigh distributed flat fading channel [30]. Therefore, \(H_{r,t}\) consists of three parts: path loss, shadow fading and fast fading. Hence \(H_{r,t}=\sqrt{l_{r,t}^{-\alpha }\cdot 10^{\frac{f_{r,t}}{10}}}\cdot \left( \begin{array}{ccc} \pi _{1,1} &{} \cdots &{} \pi _{1,n_t} \\ \vdots &{} \ddots &{} \vdots \\ \pi _{m,1} &{} \cdots &{} \pi _{m,n_t} \end{array} \right)\). Note that \(l_{r,t}\) is the distance between t and r, \(\alpha\) is a constant which usually varies from 2 to 4 and \(f_{r,t}\) is the shadow fading effect and is modeled as a log-normal distributed random variable (r.v.). In a mesh backbone network, since all the nodes are stable, it is assumed that \(f_{r,t}\) does not change with time. Likewise, the fast fading components (\(\pi _{i,j}\)) are identically independently distributed (i.i.d.) complex Gaussian random variables with mean and variance equal to 0 and 1 respectively.
Furthermore, let \(H_r=[ H_{r,t_1},\cdots , H_{r,t_n} ]\) and \({\varPhi }_r=[ X_{t_1}^T]\) with \(t_j \in T_r\). Here \(M^T\) is the transpose of matrix M. In case all the nodes in \(T_r\) are transmitting to node r, it is required that \(\sum _{\lbrace j \mid t_j\in T_r\rbrace } n_{t_j} \le m\). Hence (10) can be rewritten as \(Y_r=H_r {\varPhi }_r+\sum \limits _{t'\in \lbrace T\setminus T_r\rbrace }H_{r,t'}X_{t'}+\varsigma 1_{m\times 1}.\) When the streams arrive at receiver r, ZF (zero forcing) is applied. Let \(M^\dagger\) denote the pseudo-inverse of matrix M, i.e., \(M^\dagger =(M^*M)^{-1}M^*\). After ZF, the received signal becomes
Performing the pseudo-inverse of \(H_r\) requires that all the columns of \(H_r\) be linearly independent. This condition can usually be satisfied for two reasons. First, the number of rows (i.e., the number of receiving antennas) is \(\ge\) the number of columns (i.e., the number of data streams). Second, each entry (each element in the matrix) of \(H_r\) is independent. Hence we will ignore the case when the columns in \(H_r\) are linearly dependent.
Since \(n_t\) antennas will transmit \(n_t\) different data streams, the transmitting power at an antenna is \({p_t}/{n_t}\). At receiver r, the SINR, denoted by \(\omega _{r,t}^i\), for the ith stream from node t
Here \((\cdot )_{i,i}\) is the ith entry of a matrix, and \(\kappa\) is the power of the thermal noise \(\varsigma\). Let \(p_{r,t}={p_t}/{n_t}\cdot l_{r,t}^{-\alpha } \cdot 10^{{f_{r,t}}/{10}}\) and \(\triangle =m-\sum _{t \in T_r}n_t+1\).
Our goal is to derive the CDF of \(\omega _{r,t}^i\) when ZF is used at the receiver side. Although this was also intended in [23], its assumption that nodes follow a homogeneous PPP (Poisson Point Process) on the plane does not apply to a mesh network where nodes’ locations are fixed. In the following, we show how to derive the CDF for \(\omega _{r,t}^i\) in a mesh network.
According to [23], the numerator and each element in the denominator of (12) can be modelled as gamma distributed random variables
Since nodes are situated at different locations, all the elements in \(H_{r,t'}\) can be assumed to be independent from each other. Moreover, similar to lemma 1 of [23], the distribution of \(z_{t'}\) is only dependent on \(H_{r,t'}\) but not on \(H_r\). Hence the denominators (\(z_{t'}\)) in (12) are also assumed to be independent.
Let \(v_t={z_t}/{\gamma \kappa }\) and \(v_{t'}={z_{t'}}/{\kappa }\), where \(v_t \sim {\varGamma }( \triangle , {p_{r,t}}/{\gamma \kappa })\) and \(v_{t'} \sim {\varGamma }( n_{t'}, {p_{r,t'}}/{\kappa } )\). According to [32], \(Pr ( \sum\nolimits_{t' \in \{ T {\setminus} T_r \} }v_{t'} \le y )= b\sum\nolimits_{k=0}^{\infty }\delta _k( 1-\sum\nolimits_{i=0}^{\rho _r+k-1}\frac{y^i}{\theta _1^ii!}e^{-\frac{y}{\theta _1}} )\). Since \(\lim _{y\rightarrow \infty }Pr ( \sum\nolimits_{t'\in \lbrace T\setminus T_r \rbrace } v_{t'} \le y )\rightarrow b\sum\nolimits_{k=0}^\infty \delta _k\),we can obtain \(b\sum _{k=0}^{\infty }\delta _k=1\). From (12-13)
Appendix 2: the selection of \(k^*\)
According to (14), even though there is an infinite number of terms, as k grows larger and larger, \(\sum _{k=0}^\infty \delta _kd_{p.k}^{(p)}\) shrinks to 0. One possible way of determining \(k^*\) is:
Moreover, \(\delta _k\) will increase first. After it reaches the peak point, it tends to decrease to 0. Let \(k_{max}=\arg \max _k \delta _k\). \(k^*\) becomes:
Appendix 3: maximum throughput scaling parameter of the link-based scheme
To compute the maximum throughput scaling parameter of the link-based scheme, we can use the following formula:
Here, L denotes a link pattern, and LP is the set of all the link patterns. Note that, a link pattern determines both the set of activated links and the number of data streams used by each link. \(\mu ^L\) is the activation time of link pattern L, \(E^L\) is the set of activated links in link pattern L, and \(c_e^L\) is the average rate of link e in link pattern L. \(c_e^L\) is determined by the product of the average data rate of each data stream (refer to (1-3) in Sect. 3.2) and the number of data streams used for link e in link pattern L. Since the number of link patterns is even larger than that of the node patterns’, the column generation method is used to resolve the issue. Moreover, the column generation method for a link based scheme is a special case of a node based scheme, and similar technics we discussed before can still be used here.
Appendix 4: upper bound of the quantization loss
Given the intended frame length z, the quantization loss \(\delta _L\) after frame generation of the node-based scheme is upper bounded by \(\frac{c1}{2z}+\frac{n'}{2z+n'}\), where \(c_1=\max _{l\in E}\frac{ (\max _{S\in T_{l,2}}c_e^S)\mid T_{l,2}\mid }{2z (\sum _{\lbrace S\mid e\in E_p^S\rbrace }c_e^S\lambda _{p,e}^S )}\) and \(T_{l,2}=\lbrace S \mid S\in N',l\in E_p^S,\theta ^Sz<1/2\rbrace\). Denote \({\tilde{x}}_{f,e}\) to be the normalized routing scheme of (4) in Sect. 3.1. In other words, \({\tilde{x}}_{f,e}={x_{f,e}}/{\zeta h_f}\), where r is the maximum throughput scaling parameter derived from (4) in Sect. 3.1. Let \(\zeta _z'\) be the maximum throughput scaling parameter after frame generation with intended frame length equal to z. \(\zeta _z'\) can be derived from (7) in Sect. 3.1. We then construct the following LP.
Here \(\tau _{z,,p,e}^S={[z\cdot \theta ^S]\cdot \frac{\lambda _{p,e}^S}{\theta ^S}}/{\sum _{S\in N}[z\cdot \theta ^S]}\), and \(\tau _{z,p,e}^{S}\) can be obtained after (4) has been resolved. Clearly, \(\zeta _{2,z}\le \zeta _z'\). Define \(E_1=\left\{ e\mid e\in E, \sum _{f\in F}{\tilde{x}}_{f,e}h_f\zeta =\sum _{\lbrace S\mid e\in E_p^S, \rbrace }c_e^S \tau _{z,p,e}^S\right\}\), and \(\zeta _3=\min _{e\in E_1}{\sum _{\lbrace S\mid e\in E_p^S\rbrace }c_e^S\lambda _{p,e}^S}/{\sum _{f\in F}{\tilde{x}}_{f,e}h_f}\). Obviously \(\zeta \le \zeta _3\). Hence,
Denote \(T_{e,1}=\lbrace S \mid S\in N',e\in E_p^S,\theta ^Sz\ge \frac{1}{2}\rbrace\), \(T_{e,3}=\lbrace S \mid S\in N',e\notin E_p^S\rbrace\) and \(n'=|N'|\) (\(n'=\mid T_{e,1}\mid +\mid T_{e,2}\mid +\mid T_{e,3}\mid\) is the number of node patterns used in (7)). Therefore,
where \(n_z=\sum _{S\in N'}\theta ^Sz\le \sum _{\left\{ S\mid S\in T_{e,1}\cup T_{e,3}\right\} }(\theta ^Sz+\frac{1}{2})+\sum _{\lbrace S\mid S\in T_{e,2}\rbrace }\theta ^Sz\le z+\frac{\mid T_{e,1}\mid }{2}+\frac{\mid T_{e,3}\mid }{2}\le z+\frac{n'}{2}\). Hence \(\lambda _{p,e}^S-\tau _{z,p,e}^S\le \lambda ^S(1-\frac{z}{n_z}-\frac{1}{2n_z\theta ^S})\le \lambda _{p,e}^S(1-\frac{z}{n_z})\le \lambda _{p,e}^S \frac{n'}{2z+n'}\). Since for any \(e\in T_{e,2}, \tau _{z,p,e}^Sz<\theta ^S z<\frac{1}{2}\), \(\sum \limits _{\lbrace S \mid e\in T_{e,2}\rbrace }c_e^S\tau _{z,p,e}^S \le \frac{\left( \max _{S\in T_{e,2}}c_e^S\right) \mid T_{e,2}\mid }{2z}\), \(1-\frac{z}{n_z}-\frac{1}{2n_z\theta ^S}<1-\frac{z}{n_z}\le \frac{\frac{\mid T_{e,1}\mid }{2}+\frac{\mid T_{e,3}\mid }{2}+\frac{\mid T_{e,2}\mid }{2}}{z-\frac{\mid T_{e,1}\mid }{2}-\frac{\mid T_{e,3}}{2}-\frac{\mid T_{e,2}\mid }{2}}\). Therefore,
Here, \(c_1=\max _{e\in E}{(\max _{\lbrace S\in T_{e,2}\rbrace } c_e^S) \mid T_{e,2} \mid }/{(2z\sum _{\left\{ S\mid e\in E_p^S \right\} }c_e^S \lambda _e^S)}\). We can oberve that, \(\delta _L\) converges to 0 as z approaches to infinity.
Rights and permissions
About this article
Cite this article
Chen, W., Lea, CT. A static/opportunistic hybrid-scheduling scheme for MIMO wireless networks. Wireless Netw 24, 497–512 (2018). https://doi.org/10.1007/s11276-016-1333-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-016-1333-9