Abstract
In this paper, we consider underlay cognitive radio (CR) networks where an amount of interference caused by secondary stations (STAs) has to be kept below a predefined level, which is called interference temperature. We propose opportunistic p-persistent carrier sense multiple access schemes for the CR networks, which opportunistically exploit wireless channel conditions in transmitting data to the secondary access point. We also devise an adaptive interference-level control technique to further improve quality-of-service of a primary network by limiting the excessive interference due to collisions among STAs. The performances of the proposed schemes are mathematically analyzed, and they are validated with extensive computer simulations. The simulation results show that the proposed schemes achieve near optimal throughput of the secondary network while they are backward-compatible to the conventional p-persistent CSMA scheme.







Similar content being viewed by others
Notes
This interference constraint guarantees that the PR can accept only predetermined degradation of its quality of service (QoS).
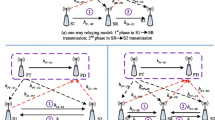
Most emerging wireless applications, such as vehicle-to-vehicle (V2V) communications, vehicle-to-infrastructure (V2I) communications, or millimeter wave communications, operate in a decentralized manner. For instance, the IEEE 802.11p system [19, 20], which is also called the wireless access in vehicular environments (WAVE) protocol, is based on the carrier sense multiple access with collision avoidance (CSMA/CA) protocol which is one of the most popular distributed scheduling algorithm.
In addition to this difference, we have also considered more sophisticated transmit power control scheme in our work compared with our previous work [1].
In this paper, we assume that the number of PR is one. However, when multiple PRs coexist, \(g_i\) can be selected by referring the channel condition of the PR whose channel gain is largest, i.e., \(\mu _{G}\) is highest.
The proper value of Q can be notified by the PR or the SAP.
The exploitation of the channel opportunity means that the transmission of STAs is adjusted according to randomly varying channel conditions. For example, the STA with high signal channel gain can be selected in scheduling to achieve higher throughput.
Unfortunately, the closed form of the inverse function of \(F_F(x)\) does not exist, such that \(\{T_k\}\) for the COpCSMA-III should be numerically calculated.
Given that the transmission is scheduled in distributed manner, the collision is inevitable.
The violation probability is the probability that the interference constraint is violated.
References
Kang, M. S., & Jung, B. C. (2010). A cognitive p-persistent CSMA scheme for spectrum sharing based cognitive radio networks. In Proceedings of IEEE WCNC.
Kang, M. S., & Jung, B. C. (2011). Performance analysis of an opportunistic CSMA scheme in cognitive radio networks. In Proceedings of IEEE MTT-S IMWS.
Mitola, J., & Maguire, G. Q. (1999). Cognitive radio: Making software radios more personal. IEEE Personal Communications, 6(4), 13–18.
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220.
Lee, W., & Cho, D.-H. (2011). Enhanced spectrum sensing scheme in cognitive radio systems with MIMO antennae. IEEE Transactions on Vehicular Technology, 60(3), 1072–1085.
Ban, T. W., Choi, W., Jung, B. C., & Sung, D. K. (2009). Multi-user diversity in a spectrum sharing system. IEEE Transactions on Wireless Communications, 8(1), 102–106.
Lee, W., & Cho, D.-H. (2013). Cooperation based new channel state acquisition scheme for ad hoc cognitive radio systems’. IEEE Transactions on Vehicular Technology, 62(7), 3325–3338.
Federal Communications Commission, Spectrum policy task force report, (ET Docket No. 02-135), (2002). http://hraunfoss.fcc.gov/edocs_public/attachmatch/DOC-228542A1.
ET Docket No. 03-237; FCC 07-78, Interference Temperature Operation, site. http://www.gpo.gov/fdsys/pkg/FR-2007-05-30/pdf/E7-10337.
Ban, T. W., Choi, W., & Sung, D. K. (2009). Capacity and energy efficiency of multi-user spectrum sharing systems with opportunistic scheduling. IEEE Transactions on Wireless Communications, 8(6), 2836–2841.
Zhang, L., Xin, Y., & Liang, Y.-C. (2009). Weighted sum rate optimization for cognitive radio MIMO broadcast channels. IEEE Transactions on Wireless Communications, 8(6), 2950–2959.
Zhang, L., Liang, Y.-C., Xin, Y., & Poor, H. (2009). Robust cognitive beamforming with partial channel state information. IEEE Transactions on Wireless Communications, 8(8), 4143–4153.
Guimaraes, F., da Costa, D., Tsiftsis, T., Cavalcante, C., & Karagiannidis, G. (2014). Multiuser and multirelay cognitive radio networks under spectrum-sharing constraints. IEEE Transactions on Vehicular Technology, 63(1), 433–439.
Gastpar, M. (2007). On capacity under receive and spatial spectrum-sharing constraints. IEEE Transactions on Information Theory, 53(2), 471–487.
Ghasemi, A., & Sousa, E. (2007). Fundamental limits of spectrum-sharing in fading environments. IEEE Transactions on Wireless Communications, 6(2), 649–658.
Zhang, R., & Liang, Y.-C. (2008). Exploiting multi-antennas for opportunistic spectrum sharing in cognitive radio networks. IEEE Journal on Selected Areas in Communications, 2(1), 88–102.
Shah, G. A., & Akan, O. B. (2014). Performance analysis of CSMA-based opportunistic medium access protocol in cognitive radio sensor networks. Ad Hoc Networks, 15, 4–13.
Li, S., Ekici, E., & Shroff, N. (2015). Throughput-optimal queue length based CSMA/CA algorithm for cognitive radio networks. IEEE Transactions on Mobile Computing, 14(5), 1098–1108.
Gozalvez, J., Sepulcre, M., & Bauza, R. (2012). IEEE 802.11p vehicle to infrastructure communications in urban environments. IEEE Communications Magazine, 50(5), 176–183.
Pyun, S., Lee, W., & Cho, D. (2016). Resource allocation for Vehicle-to-Infrastructure communication using directional transmission. IEEE Trans. Intell. Transp. Syst., 17(4), 1183–1188.
Zhao, Q., Tong, L., Swami, A., & Chen, Y. (2007). Decentralized cognitive MAC for opportunistic spectrum access in ad hoc networks: A POMDP framework. IEEE Journal on Selected Areas in Communications, 25(3), 589–600.
Zhang, Q., Fitzek, F., & Iversen, V. (2008). Cognitive radio MAC protocol for WLAN. In Proceedings of PIMRC.
Adamis, A., & Constantinou, P. (2007). Performance study of CSMA/CA over spectrum pooling environment for cognitive radios. In Proceedings of WiMOB.
Cheng, Y. C., Wu, E. H., & Chen, G. H. (2016). A decentralized MAC protocol for unfairness problems in coexistent heterogeneous cognitive radio networks scenarios with collision-based primary users. IEEE Systems Journal, 10(1), 346–357.
Wu, C. M., & Su, H. K. (2014). Cooperative power and contention control mac protocol in multichannel cognitive radio ad hoc networks. In Proceedings of IMIS.
Banaei, A., Eslami, A., Georghiades, C. N., & Cui, S. (2014). Joint random spectrum sensing and access scheme for decentralized cognitive radio networks. In Proceedings of ICC.
Joshi, G. P., Nam, S. Y., & Kim, S. W. (2014). Decentralized predictive MAC protocol for ad hoc cognitive radio networks. Wireless Personal Communications, 74(2), 803–821.
Liao, Y., Wang, T., Bian, K., Song, L., & Han, Z. (2015). Decentralized dynamic spectrum access in full-duplex cognitive radio networks. In Proceedings of ICC.
Wang, P., Ansari, J., Petrova, M., & Mhnen, P. (2014). Demo: CogMAC+-a decentralized multichannel MAC protocol for cognitive wireless networks. In Proceedings of ACM SRIF.
Knopp, R., & Humblet, P. (1995). Information capacity and power control in single-cell multiuser communications. In Proceedings of ICC.
Viswanath, P., Tse, D., & Laroia, R. (2002). Opportunistic beamforming using dumb antennas. IEEE Transactions on Information Theory, 48(6), 1277–1294.
Qin, X., & Berry, R. (2003). Exploiting multiuser diversity for medium access control in wireless networks. In Proceedings of INFOCOM.
Hwang, C.-S., Seong, K., & Cioffi, J. (2008). Throughput maximization by utilizing multi-user diversity in slow-fading random access channels. IEEE Transactions on Wireless Communications, 7(7), 2526–2535.
Kleinrock, L., & Tobagi, F. (1975). Packet switching in radio channels: Part I-carrier sense multiple-access modes and their throughput-delay characteristics. IEEE Transactions on Communications, 23(12), 1400–1416.
Cali, F., Conti, M., & Gregori, E. (2000). Dynamic tuning of the IEEE 802.11 protocol to achieve a theoretical throughput limit. IEEE/ACM Transactions on Networking, 8(6), 785–799.
Gradshteyn, I. S., & Ryzhik, I. (2000). Table of integrals, series, and products. Cambridge: Academic Press.
Acknowledgments
This research was supported in part by the National GNSS Research Center program of Defense Acquisition Program Administration and Agency for Defense Development and by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2015R1D1A1A01057529).
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
1.1 The CDF of the effective channel gain \(f_i\)
The CDF of \(f_i\) is, by definition, given as
\({\text {Pr}}\left\{ { Q \frac{\eta _i}{\gamma _i} \le x,\gamma _i> Q /\overline{P}}\right\}\) in (30) can be further derived as follows.
By substituting (31) into (30), we obtain the CDF of the effective secondary channel gain \(f_i\) given as
Rights and permissions
About this article
Cite this article
Jung, B.C., Lee, W. Performance analysis of opportunistic CSMA schemes in cognitive radio networks. Wireless Netw 24, 833–845 (2018). https://doi.org/10.1007/s11276-016-1375-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-016-1375-z