Abstract
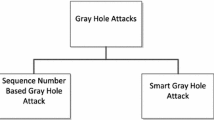
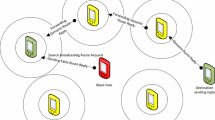
The recent development in wireless communication technology and portable devices has led to the development of Mobile Ad-Hoc Network which has unique features such as dynamic topology, open wireless medium, decentralized system etc but these network are susceptible to various denial of service attacks such as black hole, gray-hole, worm hole etc. In order to mitigate black-hole attack, various protocols have been proposed but these protocols have been not analyzed under gray-hole attack. In this paper, we have made classification of denial of service attack and highlighted the key differences among black hole, sequence number based gray-hole and smart gray-hole attack. We simulated two types of attacks namely Attack1 and Attack2 by modifying AODV protocol. The Attack1 (GAODV) is sequence number based gray-hole attack protocol whereas Attack2 (SGAODV) is smart gray-hole attack protocol. In order to observe the impact of gray-hole attacks on AODV, IDS-AODV and MBDP-AODV, NS-2.35 simulator is used. The simulation results show that MBDP-AODV performs well as compared with IDS-AODV and AODV under sequence number based gray-hole attack. Through simulation, it has also been found that the impact of the smart gray-hole attack is low as compared with the sequence number based gray-hole attack.



















Similar content being viewed by others
References
Singh, T., Singh, J., & Sharma, S. (2016). Energy efficient secured routing protocol for MANETs. Springer Wireless Network. https://doi.org/10.1007/s11276-015-1176-9.
Poongodi, T., & Karthikeyan, M. (2016). Localized secure routing architecture against cooperative black hole attack in mobile ad hoc networks. Springer Wireless Pers Commun. https://doi.org/10.1007/s11277-016-3318-5.
Murthy, C. S. R., & Manoj, B. S. (2004). Ad hoc wireless networks: Architectures and protocols. Upper Saddle River: Prentice Hall PTR.
Ning, P., & Sun, K. (2004). How to misuse AODV: a case study of insider attacks against mobile adhoc routing protocols. Adhoc Network, 3, 795–819. https://doi.org/10.1016/j.adhoc.2004.04.001.
Medadian, M., Mebadi, A., & Shahri, E. (2009). Combat with Black Hole attack in AODV routing protocol. In IEEE 9th Malaysia international conference, pp. 530–535. https://doi.org/10.1109/MICC.2009.5431439.
Jhaveri, R. H., & Patel, N. M. (2015). A sequence number based bait detection scheme to thwart grayhole attack in mobile ad hoc networks. Springer Wireless Network, 21, 2781–2798. https://doi.org/10.1007/s11276-015-0945-9.
Su, M. Y. (2011). Prevention of selective black hole attacks on mobile ad hoc networks through intrusion detection systems. Elsevier Computer Communication. https://doi.org/10.1016/j.comcom.2010.08.007.
Deng, H. M., Li, W., & Agrawal, D. P. (2002). Routing security in wireless ad hoc networks. IEEE Communication Magazine, 40(10), 70–75. https://doi.org/10.1109/MCOM.2002.1039859.
Jhaveri, R. H., Patel, S. J., & Jinwala, D.C. (2012). DoS attacks in mobile ad-hoc networks: A survey. In IEEE 2nd international conference on advanced computing & communication technologies, pp. 535–541. https://doi.org/10.1109/ACCT.2012.48.
Dorri, A. (2016). An EDRI- based approach for detecting and eliminating cooperative black hole nodes in MANET. Springer Wireless Network. https://doi.org/10.1007/s11276-016-1251-x.
Dabideen, S., & Aceves, J. J. G. L. (2012). Secure routing in MANETs using local times. Springer Wireless Network, 18, 811–826. https://doi.org/10.1007/s11276-012-0435-2.
Verma, K., Hasbullah, H., & Kumar, S. (2013). Prevention of DoS attacks in VANET. Springer Wireless Pers Commun, 2013(73), 95–126. https://doi.org/10.1007/s11277-013-1161-5.
Laxmi, V., Lal, C., Gaur, M. S., & Mehta, D. (2015). JellyFish attack: Analysis, detection and countermeasure in TCP-based MANET. Elsevier Journal of information security and Applications, 22, 99–112. https://doi.org/10.1016/j.jisa.2014.09.003.
Faghihniya, M. J., Hosseini, S. M., & Tahmasebi, M. (2016). Security upgrade against RREQ flooding attack by using balance index on vehicular adhoc network. Springer Wireless Network. https://doi.org/10.1007/s11276-016-1259-2.
Eissa, T., Razak, S. A., Khokhar, R. H., & Samian, N. (2013). Trust-based routing mechanism in MANET: Design and implementation. Mobile Network Application, Springer Telecommunication System,. https://doi.org/10.1007/s11036-011-0328-0.
Shahabi, S., Ghazvini, M., & Bakhtiarian, M. (2015). A modified algorithm to improve security and performance of AODV protocol against black hole attack. Springer Wireless Network. https://doi.org/10.1007/s11276-015-1032-y.
Mohanapriya, M., & Krishnamurthi, I. (2014). Modified DSR protocol for detection and removal of selective black hole attack in MANET. Elsevier Computers and Electrical Engineering, 40, 530–538. https://doi.org/10.1016/j.compeleceng.2013.06.001.
Gurung, S., & Chauhan, S. (2016). A novel approach for mitigating grayhole attack in MANET. Springer Wireless Network. https://doi.org/10.1007/s11276-016-1353-5.
Singh, S., Bajpai, A., & Suryambika. (2016). A survey on black hole attack in MANET. In Proceedings of the international conference on recent cognizance in wireless communication & image processing. Springer, pp 933–941. https://doi.org/10.1007/978-81-322-2638-3_105.
Kuma, J., Kulkarni, M., Gupta, D., & Indu, S. (2015). Secure route discovery in AODV in presence of blackhole attack. Springer CSI Transactions on ICT, 3(2), 91–98. https://doi.org/10.1007/s40012-016-0075-2.
Islam, N., & Shaikh, Z, A. (2013). Security issues in mobile ad hoc network. Springer wireless networks and security, part of the series signals and communication technology, pp. 49–80. https://doi.org/10.1007/978-3-642-36169-2_2.
Rathee, G., & Saini, H. (2016). Mitigation techniques for gray-hole and black hole attacks in wireless mesh network. In Proceedings of the international congress on information and communication technology. Springer, pp. 383–392. https://doi.org/10.1007/978-981-10-0755-2_41.
Swarna, M., Umar, S., & Babu, E, S. (2015). A proposal for packet prop attacks in MANETS. Springer Lecture Notes in Electrical Engineering, pp. 377–386. https://doi.org/10.1007/978-81-322-2728-1_33.
Abdelshafy, M. A., & King, P. J. B. (2014). AODV and SAODV under attack: Performance comparison. Spring Lecture Notes in Computer Science, pp. 318–331. https://doi.org/10.1007/978-3-319-07425-2_24.
Jhaveri, R, H., Patel, S, J., & Jinwala, D, C. (2012). A novel solution for grayhole attack in AODV based MANETs. Springer Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, pp. 60–67.https://doi.org/10.1007/978-3-642-35615-5_9.
Gharehkoolchian, M., Hemmatyar, A. M. A., & Izadi, M. (2015). Improving security issues in MANET AODV routing protocol. Springer Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, pp. 237–250, https://doi.org/10.1007/978-3-319-25067-0_19.
Patel, A. D., & Chawda, K. (2015). Dual security against gray-hole attack in MANETs. Springer Intelligent Computing, Communication and Devices, pp. 33–37. https://doi.org/10.1007/978-81-322-2009-1_4.
Gurung, S., & Chauhan, S. (2017). A review of black-hole attack mitigation techniques and its drawbacks in mobile ad-hoc network. In IEEE 2nd International conference on WISPNET, pp. 2409–2415.
Perkins, C. E., Beliding-Royer, E., Das, S. (2004). Ad hoc on-demand distance vector (AODV) routing. IETF internet draft, MANET working group.
Dokurer, S., Erten, Y. M., & Acar, C. E., (2007). Performance analysis of ad-hoc networks under black hole attacks. In Proceedings of the IEEE SoutheastCon. https://doi.org/10.1109/SECON.2007.342872.
Gurung, S., & Saluja, K. K. (2014). Mitigating impact of blackhole attack in MANET. In Proceedings of 5th international conference on recent trends in information, telecommunication and computing.
Gurung, S., & Chauhan, S. (2017). A dynamic threshold based approach for mitigating black-hole attack in MANET. Springer Wireless Network. https://doi.org/10.1007/s11276-017-1514-1
The Network Simulator-NS-2.35. https://www.isi.edu/nsnam/ns/.
Gurung, S., & Chauhan, S. (2017). A novel approach for mitigating route request flooding attack in MANET. Springer Wireless Network. https://doi.org/10.1007/s11276-017-1515-0.
Gurung, S., & Chauhan, S. (2017). A dynamic threshold based algorithm for improving security and performance of AODV under black-hole attack in MANET. Wireless Networks. https://doi.org/10.1007/s11276-017-1622-y.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Gurung, S., Chauhan, S. Performance analysis of black-hole attack mitigation protocols under gray-hole attacks in MANET. Wireless Netw 25, 975–988 (2019). https://doi.org/10.1007/s11276-017-1639-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-017-1639-2